V8-archive: [SECURITY] Replay Attack
Feature Request
About audited Directus version.
It has been cloned from suite repo.
Latest commit https://github.com/directus/directus/commit/1d151a9034514e3f2ec1c80001e7c5fffdef2d4e
Description:
In a replay attack the attacker issues requests that are identical to the ones the user has sent. The application could not distinguish the original legitimate request from the malicious identical requests and will process them again. If HTTPS encryption is in place while call sent to the REST API, then the protocol protects application from replay attacks at the network level. But it will not prevent legitimate clients from issuing the same request multiple times.
Business risk:
A legitimate but malicious user can perform a successful attack against the system.
Technical details:
By sending a great number of HTTP requests to the web server it is possible in some cases to cause a Denial of Service condition to the application.
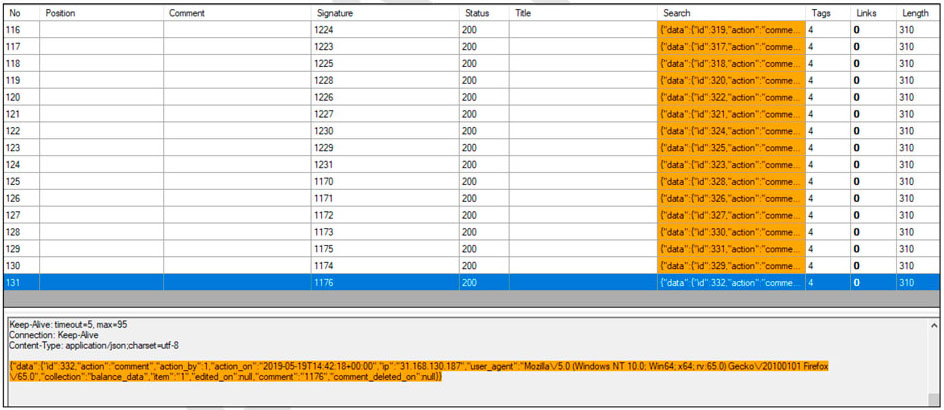
The following screenshot represent several identical requests sent by the same user in a short period of time:
What problem does this feature solve?
Fixes security hole.
How do you think this should be implemented?
It is recommended to implement an anti-automation mechanism such as CAPTCHA.
Would you be willing to work on this?
Maybe, with help/guidance from Directus team.
All 6 comments
So you mean something like a Dos/DDos protection?
Yes, I think that one is about DDos. It's obvious that you can't add captcha to all API endpoints because it will kill API usability. I discussed this part of report with my colleague and he suggested CSRF protection instead of Captcha.
Ah, this feature directus has already as far as I am concirned.
You have these 2 options in the api config which can restict access and add a rate limit.
'cors' => [
'enabled' => true,
'origin' => ['*'],
'methods' => [
'GET',
'POST',
'PUT',
'PATCH',
'DELETE',
'HEAD',
],
'headers' => [],
'exposed_headers' => [],
'max_age' => null, // in seconds
'credentials' => false,
],
'rate_limit' => [
'enabled' => false,
'limit' => 100, // number of request
'interval' => 60, // seconds
'adapter' => 'redis',
'host' => '127.0.0.1',
'port' => 6379,
'timeout' => 10
],
@ybelenko
We can restrict identical malicious requests by two options as mentioned by @Nitwel.
@bjgajjar Can you please close the issue?
You could add a timecode to each request, making it unique. The timecode has to fit to the current time on the server.
Most helpful comment
@ybelenko
We can restrict identical malicious requests by two options as mentioned by @Nitwel.
@bjgajjar Can you please close the issue?