Status-react: Stronger security checks in browser
User Story
As a user, I want my browser to check pages for suspected threats so that I'm protected against malicious behavior on web3.
Description
Type: Feature
Summary: The goal is to do more than simply verify whether an SSL cert is valid. We'll use Google Safe Browsing APIs to check for content that matches unsafe webpages.
Google's black list includes phishing sites and sites that host malware/unwanted software.
In the future, we may consider employing MetaMask's phishing detector, as well.
Expected behavior
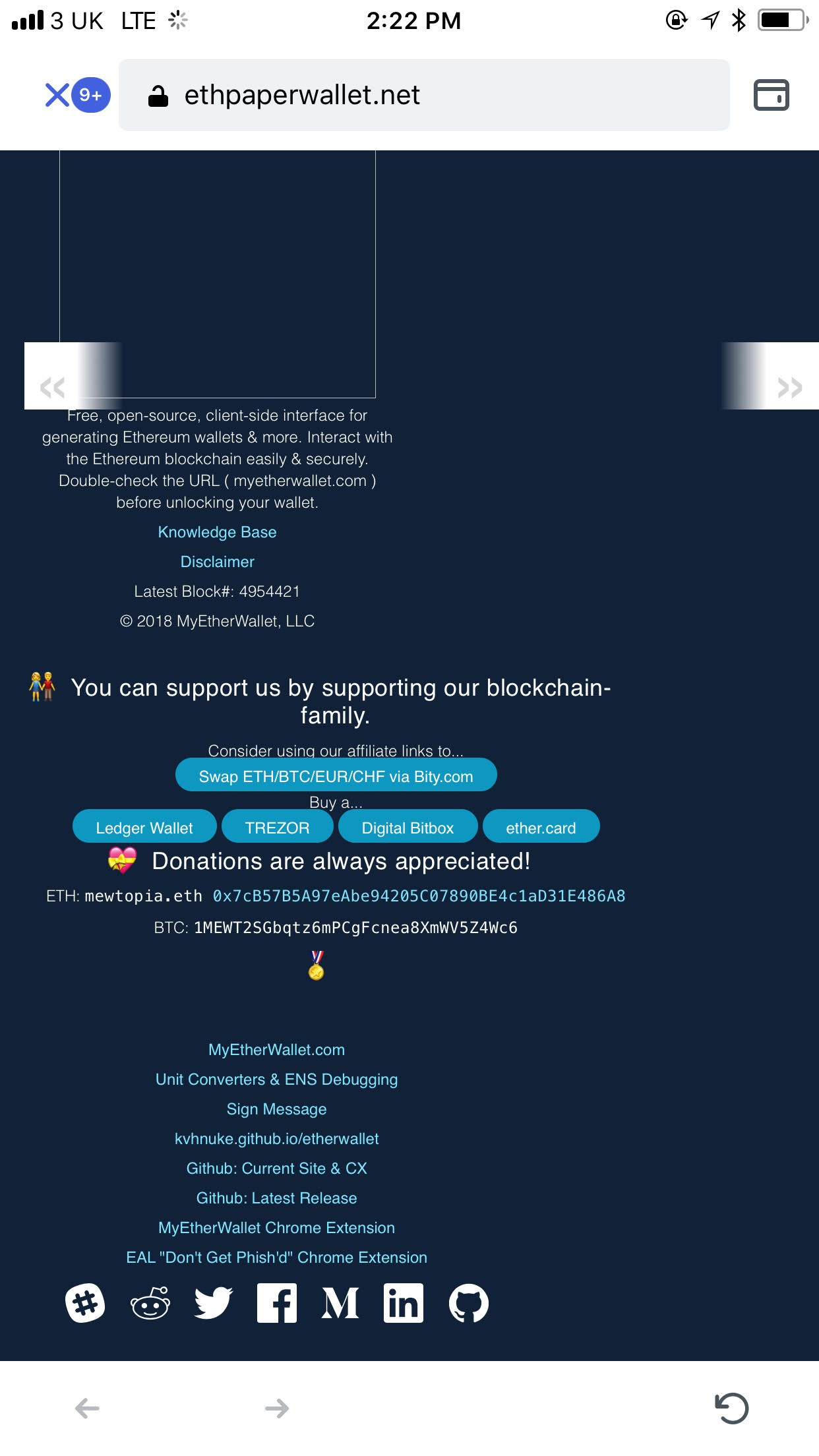
When I visit an unsafe website (e.g. ethpaperwallet.net) in Status, I'm blocked from entering with a warning message.
_Google Safe Browsing warning_

Actual behavior
I can visit certain unsafe sites in Status.
_ethpaperwallet.net_
Additional info
From the wall of shame:
Browser only validates whether SSL certificates are valid or not. But phishing sites can have valid certificates. By comparison, Google Safe Browsing checks suspicious terms from a site against Google servers.
We're in a transitionary phase, meaning we support Web 2.0 sites. While dependant on the implicit trust model of a server, we don't follow best practices in this environment. Checking SSL certificates gives us stronger guarantee's that the server we are talking to is the intended one.
As an extension to this, we could look at DNS at the same time, perhaps via ENS' DNS Layer or DNSCrypt could be another issue, if we don't trust OS's DNS lookups.
This was an issue with myetherwallet had a DNS poisoning attack made against it (beyond the usual spoofing)
Another extension to that is to look at a layer 2 safebrowsing system, ENS is/was looking to build this system out.
All 12 comments
@corpetty @mandrigin I'd love to pick your brains about this.
Can we use Google Safe Browsing APIs, or do we need a custom solution? What's the deal with ENS' DNS layer?
For me it is totally ok to start with Google APIs, they should have existing blacklists.
Also, we need to use certificate pinning for the APIs we use (like Infura, Etherscan, etc)
@mandrigin very lightweight issue for security pinning here: https://github.com/status-im/status-react/issues/5666
Would this fall within mobile client team's wheelhouse?
This task requires us to set up Google APIs and get keys.
Are we sure that we want to be dependent on Google? By calling their API every time a user navigates to somewhere we're also sending all navigation history to Google.
If yes, somebody needs to set up anything in Google Console. Add the payment method, specify company details, etc.
We can also start by using MetaMask phishing detector, it's much easier and sends nothing to Google or any other third party.
@alwx that's kind of my preference. It's a more targeted version of Google Safe Browsing.
cc @jeluard
Since there is no design yet, this is how it currently looks in my branch:
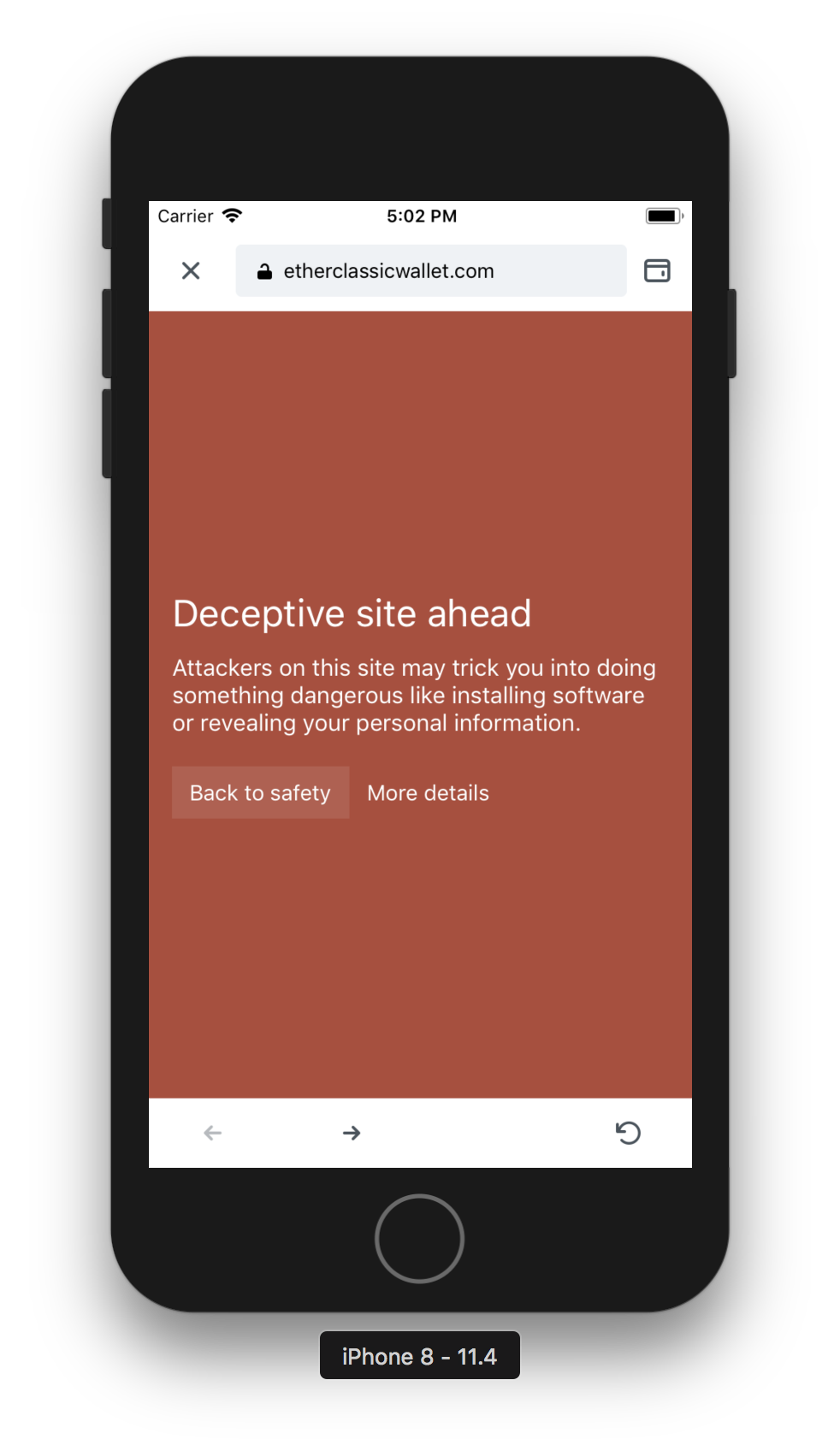
Nice. We don't actually have more details to provide, do we?
@obi2020 do you have any thoughts on the copy for this warning screen? We're now detecting potential phishing/scam sites in the browser and preventing users from navigating there. The current copy is more or less exactly what Google's warning says. I figure we'd like to customize it.
cc @denis-sharypin for design ❤️
I can rewrite, but what are the key things that are specific to Status or web3?
Should we be explicit about private keys, or give warnings about sending funds to sites that promise 10x returns? e.g. what's the scam etherpaperwallet.net?
@obi2020 good point. This current implementation will protect users from scam crypto sites, in particular, thanks for a list from MetaMask.
But in the next iteration, we'll be protecting users from _any_ suspect site (not just crypto-specific), using a Google API.
So the important information is:
- The website has been identified as malicious in some way—in some cases, this is because it's a known phishing site, but in cases identified by Google, we don't know the reason.
- Always be sure you trust a site before signing a transaction and never share with anyone your private keys.
I think that would cover it.
Copy proposal cc @obi2020
This site is blocked
We detected potential malicious activity from this address. To protect you and your wallet, we're preventing further navigation.
If you think this is an error, let us know in #status.
[Go back]
@rachelhamlin @alwx Design:
https://www.figma.com/file/gD2idhA7Uof5lc8R5nmaEXfs/DApp-browser?node-id=21%3A416
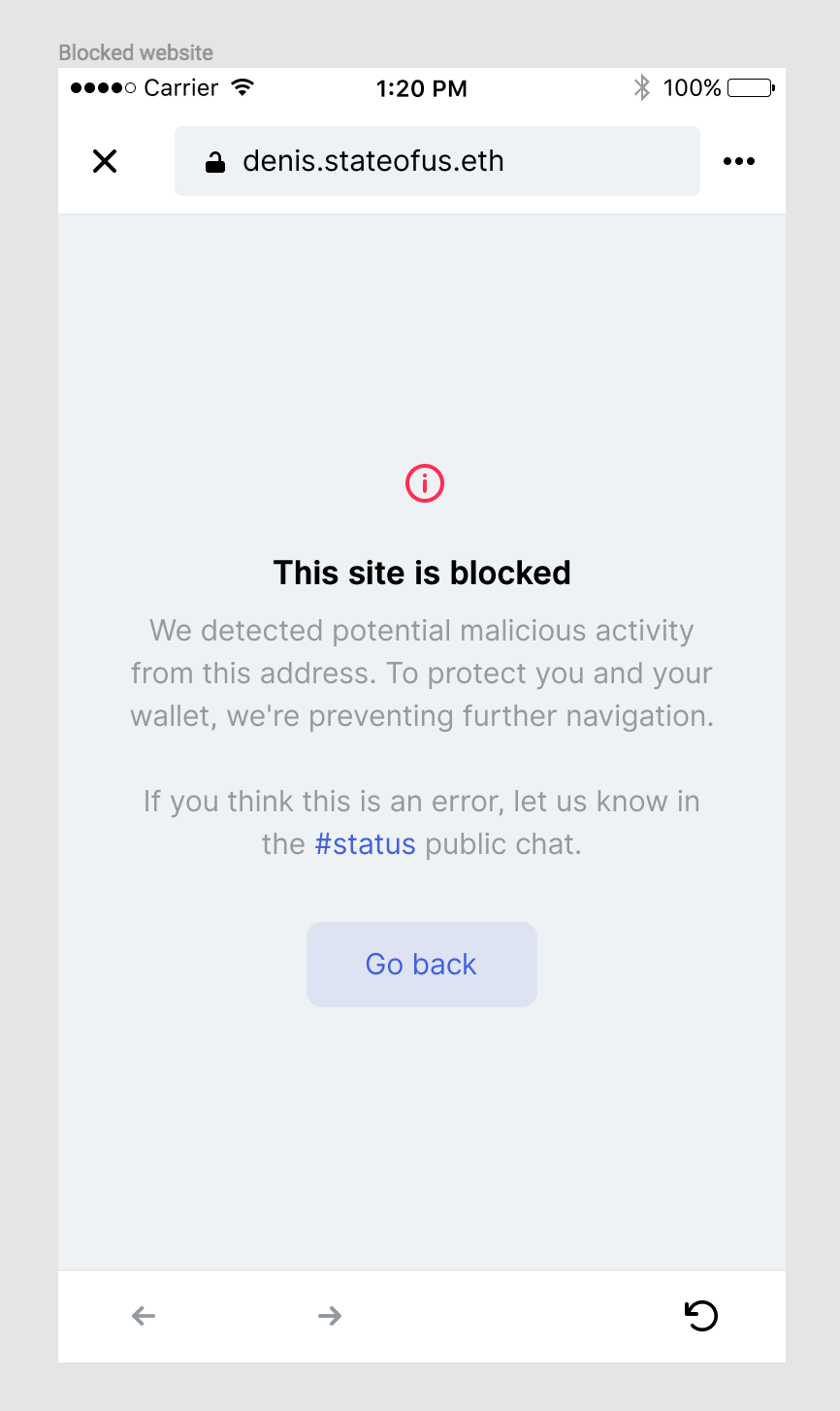
I like the addition of public chats at the end of the text.
In this case, can we write "If you think this is an error, let us know in the #status public chat" @alwx ? (Insert _the_)