Nixpkgs: How to be keep up with security upgrades?
Describe the bug
Subscribing to all security issues on GitHub is far too work intensive for anyone simply interested in whether they need to upgrade.
Expected result
Some easily consumable, automatically updated list of security updates, including at least the package name, the new version number, and a CVE link.
Actual result
Keeping up with security updates is a non-starter.
Additional context
Arch Linux has at least a web feed, Ubuntu has a mailing list, and I expect every major distro has something similar.
All 8 comments
If you follow a stable channel, you are pretty much just getting security updates. I'm not saying that it wouldn't be nice to have some way to list security issues, but presently the best thing is just to always update stable.
Could also filter PR's on github with is:pr label:"1.severity: security". Though I'm not sure everything gets labeled properly.
@peterhoeg
[…] presently the best thing is just to always update stable.
The problem with that approach is having to upgrade "arbitrarily often" to try to stay on top of security updates. That is not a viable strategy for someone using NixOS as a server OS, unless they have already perfected a continuous delivery pipeline and are willing to use lots of extra resources to deploy whenever anything at all upstream changes. And as an end user updating very often makes the probability of breakages much higher than it would otherwise be. I'm not saying the probability would be high — my experience with Arch Linux was that running an update approximately daily was much less error prone than other distros — but it would be higher, and for a reason which it should be possible to remove.
A workaround would be to have an upgrade script which only actually upgrades when there's a security update to any of the installed packages. Then running it very often would not be such a problem.
@worldofpeace That's not a viable approach for anyone except extreme die-hards. First, GitHub doesn't provide a feed of PR updates (at least not on that filter page), and implementing one myself is just out of the question. Second, such a feed would then have to be filtered to only contain merge events, and only those for packages I have already installed. Third, knowing that a PR has been merged is not the same as the PR code being available in the NixOS repositories. So a bunch of work would still be needed to tie the PR to an actual package release to make the entire system usable.
It would be nice if https://github.com/NixOS/nixpkgs/security/advisories could be used for this purpose, similar to what arch linux has going on. I only suggested a way to keep up with security updates, as we currently don't have any other way to do this.
I expose feeds per label for myself at https://feed.nix.tx0.co, which I subscribed to in Thunderbird.
It's a little crude, and has no guarantees for accuracy or uptime, but it's what I use to be notified of interesting issues.
Security feed: https://feed.nix.tx0.co/1.severity%3A_security/atom.xml (rss might work, not tested)
I'm working on a little something that extracts the data from the PR title/body using regex
Not the world's most reliable solution, but should work for creating a feed that yields the needed data
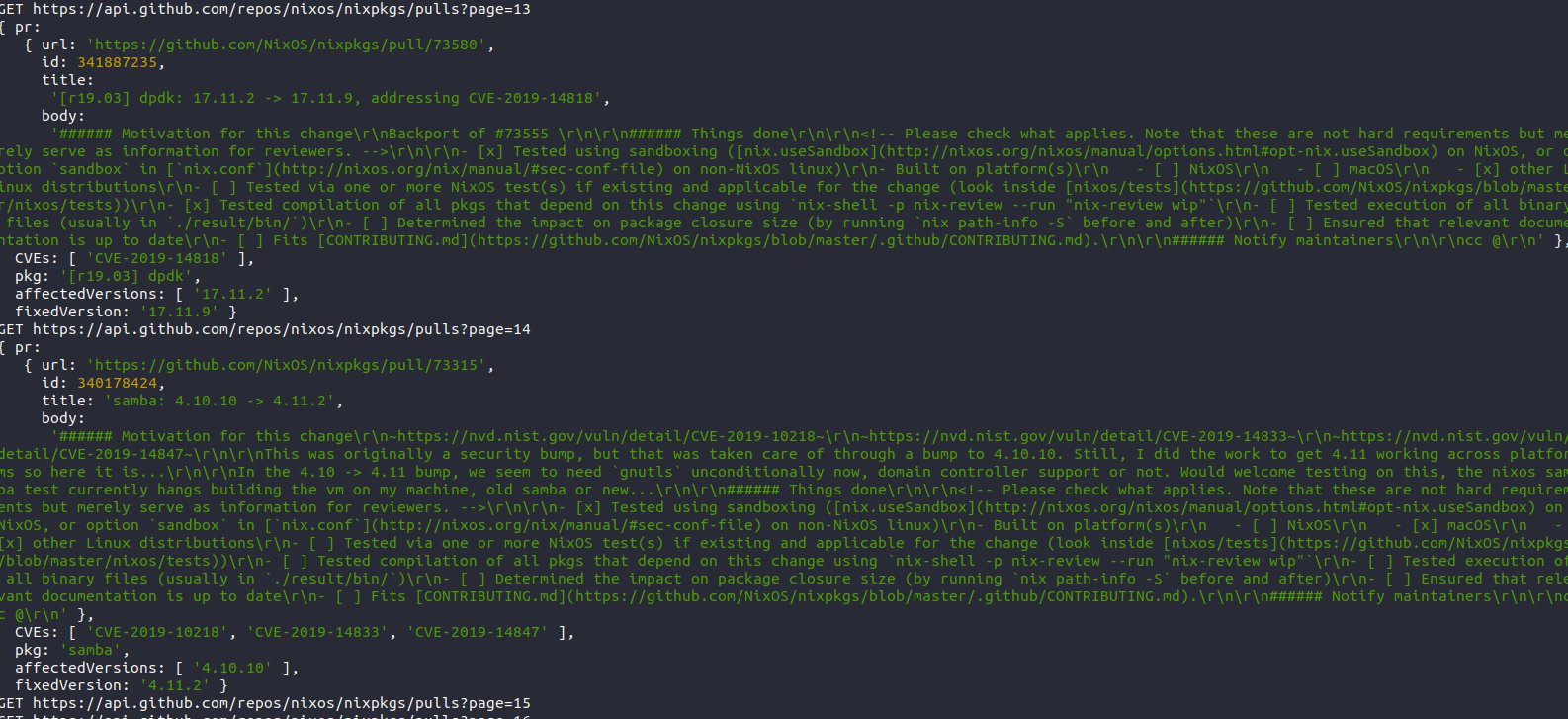
(edit: source's here https://github.com/mkg20001/nix-sec-tracker )
fwiw I put together a similar script a while ago. It tries to figure which channel the system is running on and scans any commits between system state and channel head. Unfortunately the GitHub API only allows going back in time, not forward from a given commit, so the script has to fetch a bunch of commits on a best-effort basis.
see here https://github.com/wamserma/nixos-check-update
Most helpful comment
It would be nice if https://github.com/NixOS/nixpkgs/security/advisories could be used for this purpose, similar to what arch linux has going on. I only suggested a way to keep up with security updates, as we currently don't have any other way to do this.