Metasploit-framework: `option_values_sessions': undefined method `compatible_sessions'
msfconsole crashes when using tab autocomplete for set session, ie: set session <tab>
# ./msfconsole
[-] ***rTing the Metasploit Framework console...|
[-] * WARNING: No database support: No database YAML file
[-] ***
_ood>H&H&Z?#M#b-\.
.\HMMMMMR?`\M6b."`' ''``v.
.. .MMMMMMMMMMHMMM#&. ``~o.
. ,HMMMMMMMMMM`' ' ?MP?.
. |MMMMMMMMMMM' `"$b&\
- |MMMMHH##M' HMMH?
- TTM| >.. \HMMMMH
: |MM\,#-""$~b\. `MMMMMM+
. ``"H&# - &MMMMMM|
: *\v,#MHddc. `9MMMMMb
. MMMMMMMM##\ `"":HM
- . .HMMMMMMMMMMRo_. |M
: |MMMMMMMMMMMMMMMM#\ :M
- `HMMMMMMMMMMMMMM' |T
: `*HMMMMMMMMMMM' H'
: MMMMMMMMMMM| |T
; MMMMMMMM?' ./
` MMMMMMH' ./'
- |MMMH#' .
` `MM* . `
_ #M: . . .-'
. ., .-'
'-.-~ooHH__,,v~--`'
__ __ __ __ __ ____ __ __
/ / / /___ ______/ /__ / /_/ /_ ___ / __ \/ /___ _____ ___ / /_
/ /_/ / __ `/ ___/ //_/ / __/ __ \/ _ \ / /_/ / / __ `/ __ \/ _ \/ __/
/ __ / /_/ / /__/ ,< / /_/ / / / __/ / ____/ / /_/ / / / / __/ /_
/_/ /_/\__,_/\___/_/|_| \__/_/ /_/\___/ /_/ /_/\__,_/_/ /_/\___/\__/
=[ metasploit v5.0.0-dev-d49d7a1 ]
+ -- --=[ 1823 exploits - 1033 auxiliary - 315 post ]
+ -- --=[ 539 payloads - 42 encoders - 10 nops ]
+ -- --=[ ** This is Metasploit 5 development branch ** ]
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload solaris/x86/shell_reverse_tcp
payload => solaris/x86/shell_reverse_tcp
msf5 exploit(multi/handler) > set lport 1337
lport => 1337
msf5 exploit(multi/handler) > set lhost 172.16.191.196
lhost => 172.16.191.196
msf5 exploit(multi/handler) > set exitonsession false
exitonsession => false
msf5 exploit(multi/handler) > run -jz
[*] Exploit running as background job 0.
[*] Started reverse TCP handler on 172.16.191.196:1337
msf5 exploit(multi/handler) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell x86/solaris 172.16.191.196:1337 -> 172.16.191.153:32822 (172.16.191.153)
msf5 exploit(multi/handler) > set session /pentest/exploit/metasploit-framework/lib/msf/ui/console/command_dispatcher/core.rb:2228:in `option_values_sessions': undefined method `compatible_sessions' for #<Msf::Modules::Mod6578706c6f69742f6d756c74692f68616e646c6572::MetasploitModule:0x0000001a76db70> (NoMethodError)
Did you mean? compatible_encoders
from /pentest/exploit/metasploit-framework/lib/msf/ui/console/command_dispatcher/core.rb:2101:in `tab_complete_option'
from /pentest/exploit/metasploit-framework/lib/msf/ui/console/command_dispatcher/core.rb:1610:in `cmd_set_tabs'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:421:in `tab_complete_helper'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:381:in `block in tab_complete_stub'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:370:in `each'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:370:in `tab_complete_stub'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:355:in `tab_complete'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/shell.rb:62:in `block in init_tab_complete'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/readline.rb:136:in `readline_attempted_completion_function'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:6329:in `gen_completion_matches'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:6813:in `rl_complete_internal'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:6903:in `rl_complete'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:4374:in `_rl_dispatch_subseq'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:4363:in `_rl_dispatch'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:4779:in `readline_internal_charloop'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:4853:in `readline_internal'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:4875:in `readline'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/input/readline.rb:162:in `readline_with_output'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/input/readline.rb:100:in `pgets'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/shell.rb:309:in `get_input_line'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/shell.rb:134:in `run'
from /pentest/exploit/metasploit-framework/lib/metasploit/framework/command/console.rb:48:in `start'
from /pentest/exploit/metasploit-framework/lib/metasploit/framework/command/base.rb:82:in `start'
from ./msfconsole:49:in `<main>'
All 8 comments
I like the banner, I never got that one.. Is it custom made??
@Auxilus yes :) You can find some custom logos here: https://github.com/bcoles/metasploit-logos
@bcoles thanks! 😃
@Green-m: Any chance this is related to #10379?
@wvu-r7 @bcoles
This cannot reproduce on my machine.
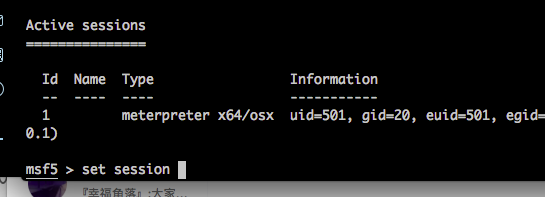
What's your env? @bcoles
@Green-m You'll need to select a module first. The issue is not reproducible form the msf5 > prompt. Any module should do. I've verified using exploit/multi/handler and some local exploits.
Latest version of Metasploit from GitHub, Ruby 2.3.0, no database connected.
Apparently it's a little more complicated. Not any module is sufficient to trigger the bug.
The output below shows that msfconsole crashes when exploit/multi/handler is selected. I'm certain that I've also received a crash when the module I've selected was not compatible with any of the open sessions, in particular cmd/unix/reverse_netcat.
msf5 exploit(solaris/local/extremeparr_dtappgather_priv_esc) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell x86/solaris 172.16.191.196:1337 -> 172.16.191.141:32829 (172.16.191.141)
msf5 exploit(solaris/local/extremeparr_dtappgather_priv_esc) > set session 1
session => 1
msf5 exploit(solaris/local/extremeparr_dtappgather_priv_esc) > use exploit/windows/local/wmi
msf5 exploit(windows/local/wmi) > set session
set session set sessionlogging
msf5 exploit(windows/local/wmi) > set session
set session set sessionlogging
msf5 exploit(windows/local/wmi) > use exploit/multi/handler
msf5 exploit(multi/handler) > set session /pentest/exploit/metasploit-framework/lib/msf/ui/console/command_dispatcher/core.rb:2228:in `option_values_sessions': undefined method `compatible_sessions' for #<Msf::Modules::Mod6578706c6f69742f6d756c74692f68616e646c6572::MetasploitModule:0x00000016a753f8> (NoMethodError)
Did you mean? compatible_encoders
from /pentest/exploit/metasploit-framework/lib/msf/ui/console/command_dispatcher/core.rb:2101:in `tab_complete_option'
from /pentest/exploit/metasploit-framework/lib/msf/ui/console/command_dispatcher/core.rb:1610:in `cmd_set_tabs'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:421:in `tab_complete_helper'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:381:in `block in tab_complete_stub'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:370:in `each'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:370:in `tab_complete_stub'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:355:in `tab_complete'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/shell.rb:62:in `block in init_tab_complete'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/readline.rb:136:in `readline_attempted_completion_function'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:6329:in `gen_completion_matches'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:6813:in `rl_complete_internal'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:6903:in `rl_complete'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:4374:in `_rl_dispatch_subseq'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:4363:in `_rl_dispatch'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:4779:in `readline_internal_charloop'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:4853:in `readline_internal'
from /usr/local/rvm/gems/ruby-2.3.0/gems/rb-readline-0.5.5/lib/rbreadline.rb:4875:in `readline'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/input/readline.rb:162:in `readline_with_output'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/input/readline.rb:100:in `pgets'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/shell.rb:309:in `get_input_line'
from /pentest/exploit/metasploit-framework/lib/rex/ui/text/shell.rb:134:in `run'
from /pentest/exploit/metasploit-framework/lib/metasploit/framework/command/console.rb:48:in `start'
from /pentest/exploit/metasploit-framework/lib/metasploit/framework/command/base.rb:82:in `start'
from ./msfconsole:49:in `<main>'
@bcoles Succeed to crashed on my env.
With a quick look, seems that it is not related to #10379 ,I would drill it down.