Kibana: Kibana completely broken in Edge browser on 6.7.0
Kibana version: 6.7.0 BC2
Elasticsearch version: 6.7.0 BC2
Server OS version: CentOS 7
Browser version: Microsoft Edge 42.17134.1.0
Browser OS version: Windows 10
Original install method (e.g. download page, yum, from source, etc.): rpms on CentOS VM
Describe the bug: The Kibana login page won't load on Edge.
Screenshots (if relevant):
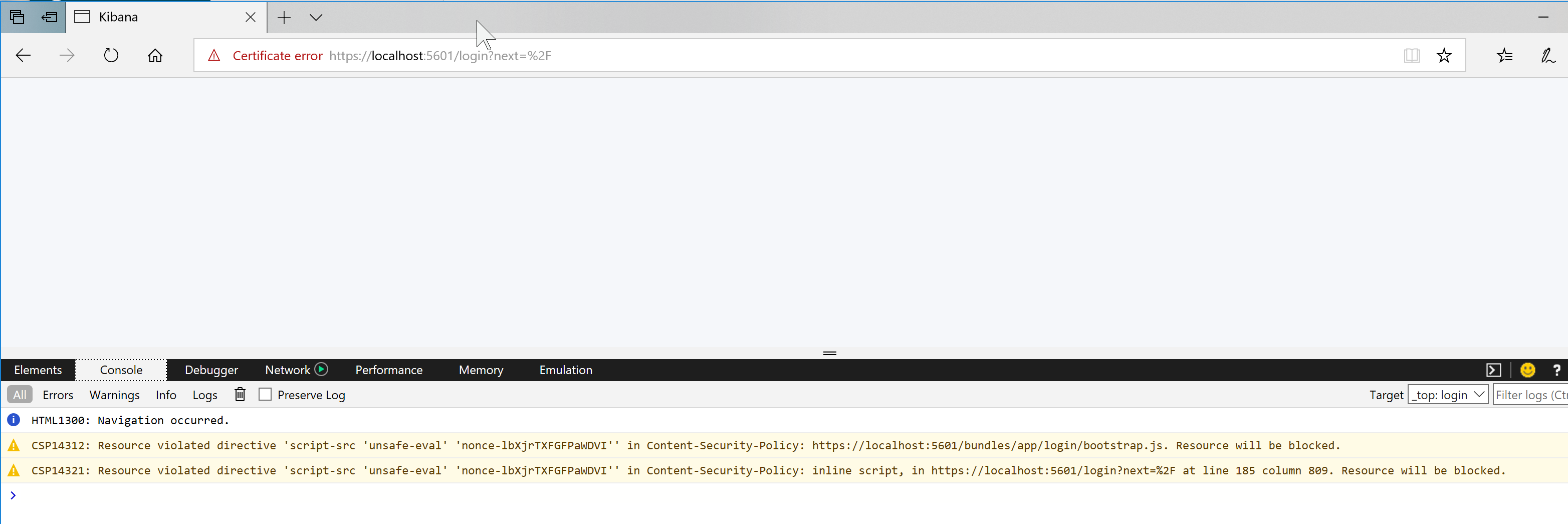
Errors in browser console (if relevant): See screenshot
Searchable text of the console messages;
CSP14312: Resource violated directive 'script-src 'unsafe-eval' 'nonce-qS/c93oyDimKcatR'' in Content-Security-Policy: http://localhost:5601/bundles/app/kibana/bootstrap.js. Resource will be blocked.
CSP14321: Resource violated directive 'script-src 'unsafe-eval' 'nonce-qS/c93oyDimKcatR'' in Content-Security-Policy: inline script, in http://localhost:5601/app/kibana at line 185 column 809. Resource will be blocked.
All 12 comments
Pinging @elastic/kibana-platform
I'm filing as a blocker, but technically Edge isn't listed on our support matrix (but should be by now).
setting csp.strict: false in kibana.yml and restarting doesn't appear to fix it.
Pinging @elastic/kibana-security
The issue here is that Microsoft Edge is broken, and I assume at this point that they won't fix it and will instead just wait until they release the new version of Edge built on chromium. Maybe late 2019?
Edge is not a supported browser for Kibana, and I do not recommend that anyone use unsupported browsers with Kibana. The only solution on Kibana's end is to serve a less secure content security policy for the sake of accommodating a bug in Edge, which I don't think we should do.
That said, if anyone must support Edge for some reason, the workaround is to relax the content security policy via kibana.yml. The following example policy should make Kibana work in Edge:
csp.rules:
- "script-src 'self' 'unsafe-eval' 'unsafe-inline'"
- "worker-src blob:"
- "child-src blob:"
This example policy is less secure than the default shipped with Kibana versions 6.7 and up, and I strongly recommend that people do not set their own csp.rules unless they absolutely have to. However, this example policy provides no less security than what existed in Kibana versions 6.6 and below, since they didn't have content security policies at all.
@elastic/kibana-security thoughts?
If we're comfortable from a product perspective making Kibana not work on Edge, this at least feels like something we should be introducing in a major version.
cc @AlonaNadler @alexfrancoeur
If we leave it this way at least we'll find our who uses Edge browser (or who can't use another browser).
Often admins don't necessarily control which browsers users are using. When using the workaround @epixa provided it will make entire Kibana less secure so it will probably not a good workaround for most.
When users trying to use Edge can we have a message specifically to edge users asking to change to different browsers?
@epixa is that the most simple workaround? If csp.strict = false (https://github.com/elastic/kibana/pull/29856), Edge still does not work? I believe in 6.7 this is set to false by default, but wanted to confirm.
Is it possible to offer a way to disable CSP in 6.x and then remove that capability in 7.0? I realize we don't technically support Edge, but it does feel like a breaking change. I tend to agree with Brandon here.
As Alona suggested, are we able to show a more meaningful error message?
@alexfrancoeur let me sync with @epixa a little later today to figure out our game plan, I think we'll need at least some changes to the way we're handling this today, breaking Edge in 6.7 without an obvious error message doesn't feel like something we want to do.
Court and I just spoke on Zoom, and we're planning on making changes to 6.7 to prevent Edge from breaking. To do so, we're going to use script-src: 'self' and remove the use of the nonce, which is where we're hitting the bug in Edge. We'll leave the code in place so that it's possible for users to opt into using the nonce based approach, but it will not be the default.
Starting in 7.0, we will begin using the nonce based approach, which will break Edge support. The reason why Edge doesn't work isn't due to them not supporting the CSP 2 rules which we're using, it's because there's a bug in their implementation, which they've failed to address to date. Given the current state of Edge, particularly the fact that Microsoft is abandoning efforts on the current code-base in an effort to move to a Chromium based browser, coupled with our really low usage data, I don't think we should be adding Edge to our support matrix.
This should have been closed by https://github.com/elastic/kibana/pull/31610