Joplin: Vulnerability report - please contact
I would like to report a vulnerability. Could you please contact me on [email protected] as I did not manage to find any e-mail from your repo to contact you.
Best,
Silvia
All 4 comments
Contacted, and keeping the issue open for further reference.
Fix will be available in next release.
1.0.90 released
"XSS vulnerability evolving into code execution due to enabled nodeIntegration for the renderer process"
Fixed in version 1.0.90
Vulnerable field: Note content field
As Electron-based applications are built using web technologies like HTML, CSS and JS, they
are also prone to be vulnerable to web-based attacks. If a cross-site scripting vulnerability (XSS) is
found in an Electron application, where node integration has been enabled for that particular BrowserWindow instance (XSS+under webPreferences nodeIntegration:True), the attacker has the capability to require node modules like 'os', etc. ..., hence access operating system native primitives. This allows XSS in Electron applications to evolve into code execution.
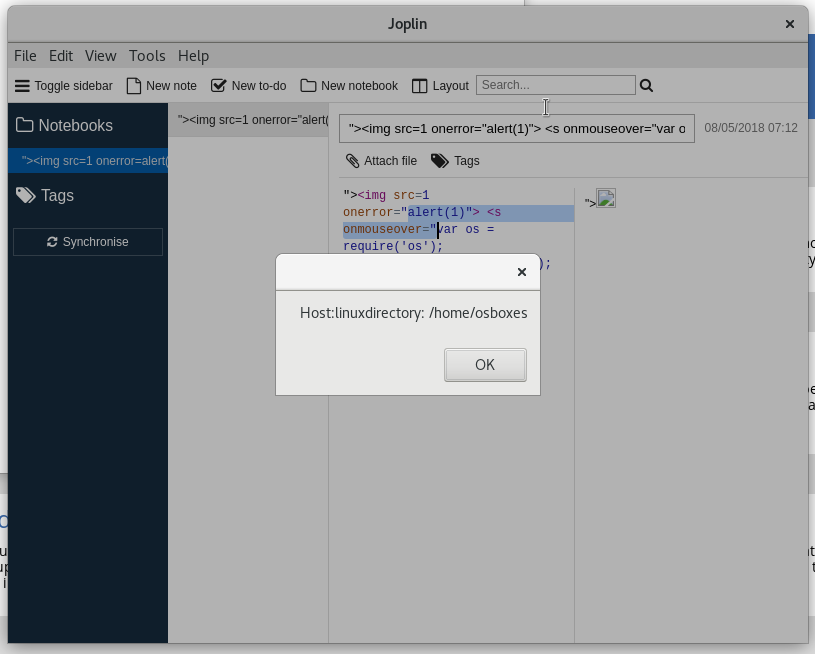
Payload used for poc:
"><img src=1 onerror="var os = require('os');
var hostname = os.platform(); var homedir = os.homedir();
alert('Host:' + hostname + 'directory: ' + homedir);">
Good reference to Electron related issues:
https://www.blackhat.com/docs/us-17/thursday/us-17-Carettoni-Electronegativity-A-Study-Of-
Electron-Security-wp.pdf
Most helpful comment
"XSS vulnerability evolving into code execution due to enabled nodeIntegration for the renderer process"
Fixed in version 1.0.90
Vulnerable field: Note content field
As Electron-based applications are built using web technologies like HTML, CSS and JS, they
are also prone to be vulnerable to web-based attacks. If a cross-site scripting vulnerability (XSS) is
found in an Electron application, where node integration has been enabled for that particular BrowserWindow instance (XSS+under webPreferences nodeIntegration:True), the attacker has the capability to require node modules like 'os', etc. ..., hence access operating system native primitives. This allows XSS in Electron applications to evolve into code execution.
Payload used for poc:
"><img src=1 onerror="var os = require('os'); var hostname = os.platform(); var homedir = os.homedir(); alert('Host:' + hostname + 'directory: ' + homedir);">Good reference to Electron related issues:
https://www.blackhat.com/docs/us-17/thursday/us-17-Carettoni-Electronegativity-A-Study-Of-
Electron-Security-wp.pdf