Identityserver4: Support ASP.NET Core 2.0
All 84 comments
is there a row map?
We will target asp.net core 2 preview 2 once it is released.
https://www.nuget.org/packages/Microsoft.AspNetCore/2.0.0-preview2-final looks like it's just been released.
thx for the heads up
Should we expect an identityserver4 support for asp.net core 2.0 preview2 anytime soon? Would you be able to estimate when, approximately?
No, as we're both already quite booked with consulting and holiday travel.
Would there be any workaround that we could do to have a temporary fix for this or do we have to wait on you guys to release it?
Hire us to accelerate the process.
I would if I could
I'd be willing to sponsor you one beer.
Maybe we could crowd source this :) ?
I appreciate the positions individual developers are in trying to use FOSS to get their jobs done. Companies don't usually know (or care) what tools you're using to get the job done, and they miss the point that this FOSS is not really free. If the company has a need for it, then they should be led to understand that some cost must be incurred. If they aren't willing to do that, then the individual devs have to explain to upper management that they must wait until the project owners take time away from their paying jobs and families to work on this product that your company is using for free.
Absolutely agree with everything you are saying. Was suggesting that us developers at smaller companies that cannot afford to hire you by themselves, perhaps it could be done as a group. I am sure I could convince my boss to make a healthy contribution, but only that. I have no problem explaining the situation to him as you have written above. We are already getting a lot for nothing. What you and Dominick have done is amazing and gratefully received.
I'm not trying to make a suggestion you wouldn't want, so feel free to delete my post.
perhaps it could be done as a group
I appreciate the sentiment. Personally I'd be uncomfortable if it was individual contributors -- your companies should be paying for this, not you. Do you pay for a personal copy of Visual Studio to get your job done? Just an example. This is why I was trying to promote the idea of the devs at the company raising this as awareness to the management level. Also, Microsoft does an awful job in this space, as they have lulled companies into thinking that tooling and frameworks are all free (and the cost comes in by paying for the platform which is where Microsoft makes their money from providing their free frameworks).
I would be happy to contribute to this too. Perhaps a crowdfunding page/contribution page of some sorts?
I did a conversion to 2.0-preview2 - good enough to play around - but needs more work
https://github.com/IdentityServer/IdentityServer4/tree/aspnetcore2
@leastprivilege Glad to hear that. I have couples of projects that depend heavily on ID4 currently. So there is any plan to release it?
Well - once ASP.NET Core 2 is released - we will have a new version too.
come on, give me a IdentityServer4 Core 2.0 Preview 2
Could you please make it a NuGet package so we can use it? Maybe as a pre-release? My projects are all depending on the core 2.0 (ef, aspnet, identity server) to continue :(
I'm talking about this branch: https://github.com/IdentityServer/IdentityServer4/tree/aspnetcore2
why don't you run build.ps1 yourself - the result will be a nuget package...
First nuget with aspnet core 2 preview2 support:
https://www.nuget.org/packages/IdentityServer4/2.0.0-preview2
Give it a try and let us know what's not working...
Awesome! Will the other packages like identityServer4 with ASP Net identity
or JWT Authentication work fine or do they need to be updated as well?
On Wed, Jul 19, 2017 at 7:54 AM, Dominick Baier notifications@github.com
wrote:
First nuget with aspnet core 2 preview2 support:
https://www.nuget.org/packages/IdentityServer4/2.0.0-preview2
Give it a try and let us know what's not working...
—
You are receiving this because you commented.
Reply to this email directly, view it on GitHub
https://github.com/IdentityServer/IdentityServer4/issues/1055#issuecomment-316290372,
or mute the thread
https://github.com/notifications/unsubscribe-auth/AFqqs65RRaXWJlVqh-5eiRNA62NcYFRmks5sPag5gaJpZM4M7gaj
.
they also need updating.
Hi , Thanks for the great work . i'm trying to implement IDS4 in Core 2.0 ,i also update IDS4 using below nuget comment " Install-Package IdentityServer4 -Pre" , i'm getting following error
app.UseIdentityServerAuthentication(new IdentityServerAuthenticationOptions
{
//Identity Server URL
Authority = "http://localhost:49370",
RequireHttpsMetadata = false,
ApiName = "api1"
});
Severity Code Description Project File Line Suppression State
Error CS7069 Reference to type 'AuthenticationOptions' claims it is defined in 'Microsoft.AspNetCore.Authentication', but it could not be found
The access token validation middleware hasn't been ported. Use Microsoft's JwtBearer as a replacement for now.
@leastprivilege am i correct ?
* app.UseJwtBearerAuthentication(new JwtBearerOptions {
Authority= "http://localhost:49370",
RequireHttpsMetadata=false
});*
is this correct way?
And Audience
I'm getting following
everity Code Description Project File Line Suppression State
Error CS0619 'JwtBearerAppBuilderExtensions.UseJwtBearerAuthentication(IApplicationBuilder, JwtBearerOptions)' is obsolete: 'See https://go.microsoft.com/fwlink/?linkid=845470'
can you provide any suggestion
Well - there are breaking changes in aspnetcore2 - this is not really the place to discuss them - but have a look here
services.AddJwtBearerAuthentication(o => {
o.Authority = "http://localhost:49371/";
o.Audience = "myapi";
});
IDS4 running in this URL "http://localhost:49371" ,but i's not authorize
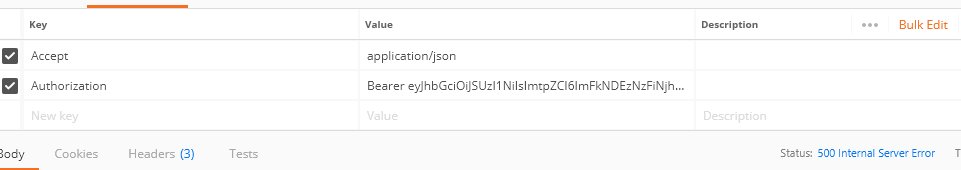
its showing 500 error , am i wrong in my configuration?
Maybe try setting the DefaultAuthenticate Scheme to JwtBearer Scheme? This works for me.
services.AddAuthentication(options =>
{
options.DefaultAuthenticateScheme = JwtBearerDefaults.AuthenticationScheme;
options.DefaultChallengeScheme = JwtBearerDefaults.AuthenticationScheme;
});
Or disable https
services.AddJwtBearerAuthentication(o =>
{
o.Audience = "myapi";
o.Authority = "http://localhost:5000";
o.RequireHttpsMetadata = false;
});
Still same issue :( 401 unauthorized ,
services.AddJwtBearerAuthentication(o => {
o.Authority = "http://localhost:49371/";
o.Audience = "http://localhost:49371/resources";
o.RequireHttpsMetadata = false;
});
Did you put app.UseAuthentication(); before app.UseMvc(); in the Configure method?
Yes @KalBence
in configure method
app.UseAuthentication();
in ConfigureServices method
services.AddJwtBearerAuthentication(o => {
o.Authority = "http://localhost:49371/";
o.Audience = "http://localhost:49371/resources";
o.RequireHttpsMetadata = false;
});
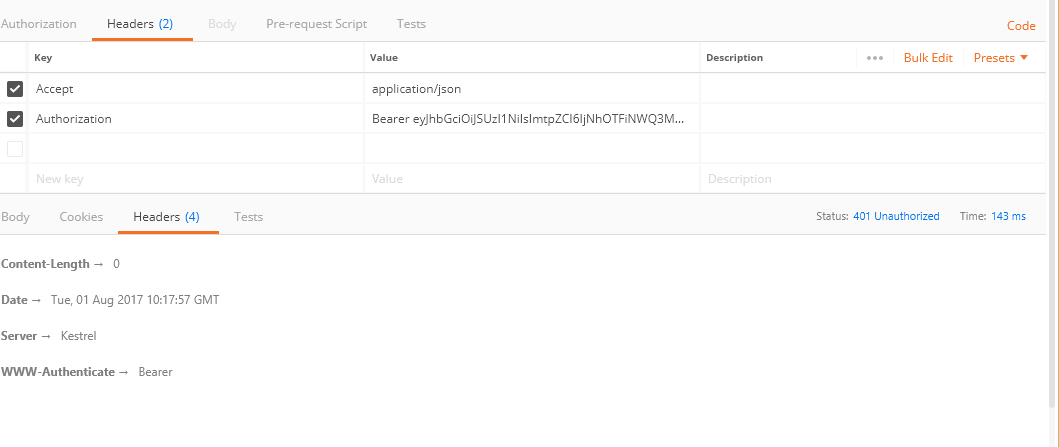
this is my request
Remove the last '/' from o.Authority = "http://localhost:49371/";
to,
o.Authority = "http://localhost:49371";
I hope this helps someone trying to use Identity Server with net Core 2 following the IDS4 Tutorial.
There is not full support for all the identity server 4 packages for Net Core 2 Yet, the workaround it's build up your Identity Server with net core 1.1, and you can validate tokens from resources build in net core 2.0 using Microsoft JwtBearer like this:
After creating the api add this to ConfigureServices
services.AddAuthentication(options =>
{
options.DefaultAuthenticateScheme = JwtBearerDefaults.AuthenticationScheme;
options.DefaultChallengeScheme = JwtBearerDefaults.AuthenticationScheme;
}).AddJwtBearer(o =>
{
o.Authority = "http://localhost:5000";
o.Audience = "api1";
o.RequireHttpsMetadata = false;
});
and change this code in Configure Method (As written in the tutorial):
app.UseIdentityServerAuthentication(new IdentityServerAuthenticationOptions
{
Authority = "http://localhost:5000",
RequireHttpsMetadata = false,
ApiName = "api1"
});
for this (Remember just before app.UseMvc() ):
app.UseAuthentication();
This is a workaround while the rest of the identity server nuget's get updated to net core 2.0 !
In the meantime I'll keep testing the project.
Good work guys ! and Awesome project ! Keep it up please !
Dear,
I'm following the official documentation on how to implement my first ID4 server on ASPNET CORE 2.0, but when i try to debug the application i encounter the exception:
System.MissingMethodException:'Method not found: 'Microsoft.Extensions.DependencyInjection.IServiceCollection Microsoft.Extensions.DependencyInjection.AuthenticationServiceCollectionExtensions.AddAuthentication(Microsoft.Extensions.DependencyInjection.IServiceCollection)'.'
My ConfigureServices() is this:
var migrationsAssembly = typeof(Startup).GetType().Assembly.GetName().Name;
services.AddMvc();
services.AddIdentityServer()
.AddTemporarySigningCredential()
.AddTestUsers(Config.GetUsers())
.AddConfigurationStore(builder =>
builder.UseSqlServer(Configuration.GetConnectionString("credential"), options =>
options.MigrationsAssembly(migrationsAssembly)))
.AddOperationalStore(builder =>
builder.UseSqlServer(Configuration.GetConnectionString("credential"), options =>
options.MigrationsAssembly(migrationsAssembly)));
My NuGets are:
- IdentityServer4.AspNetIdentity 1.0.1
- IdentityServer4.EntityFramework 1.0.1
- All MS packages are 2.0.0
I tried also using IdentitServer4 => v2.0.0-preview2 but the error remain.
Do you have some suggestion?
@michaelsogos I'll will try to explain it a little more detailed:
Yeah, there is a IdentityServer4 2.0.0-preview2 that works on netcore 2, but you only have the server functionality, that means that, if you try to attach a persistent storage like EntityFrameworkCore or an identity manager like AspNet.Identity even when both Microsoft Packages are updated and working on netcore 2, you need to tell IDS4 to use them and for that you need these 2 packages:
IdentityServer4.AspNetIdentity 1.0.1
IdentityServer4.EntityFramework 1.0.1
And they have dependencies to netcore 1 and nothing more, so that's why you get exceptions, they are not migrated yet.
So here are your choises (At least what I think)
- You can build your IDS4 and web apis using netcore 1 as the tutorial and docs explain.
- You can build your IDS4 using netcore 1; Build your web api's or any other resource using netcore 2, and for token validation until the IdentityServer4.AccessTokenValidation package gets migrated, install and configure Microsoft JwtBearer in your resource as suggested by @leastprivilege the way I commented before; If you do so, when we get IdentityServer4 fully supported, you only worry about porting your IDS4 to netcore 2, and minor changes in your web apis.
Good Luck Friend !
OK, i get it.
Its released its releases! :)
However guys relax there will be support for ASP.NET Core 1 for a full year so no need to immediately upgrade. Not a good idea anyways before being sure its really stable. :)
@rh78 what do you mean ? I don't see full support yet
I mean ASP.NET Core 2 has been officially released which means that there can be stable and meaningful works to upgrade IDSrv4 now
Omg ! I was so busy at work, I didnt know that .... you made my day @rh78 Thank you !
@DavidNorena Just highlighting yesterday announcements...
https://blogs.msdn.microsoft.com/dotnet/2017/08/14/announcing-net-core-2-0/
https://blogs.msdn.microsoft.com/webdev/2017/08/14/announcing-asp-net-core-2-0/
https://blogs.msdn.microsoft.com/dotnet/2017/08/14/announcing-net-standard-2-0/
https://blogs.msdn.microsoft.com/dotnet/2017/08/14/announcing-entity-framework-core-2-0/
@DavidNorena , following your suggestion with the ASP.NET Core 2 officially, I have the following error when I try the services.AddJwtBearerAuthentication
'IServiceCollection' does not contain a definition for 'AddJwtBearerAuthentication' and no extension method 'AddJwtBearerAuthentication' accepting a first argument of type 'IServiceCollection' could be found (are you missing a using directive or an assembly reference?)
Is this something that existed on preview and didn't make it to the final version?
@DanielSSilva , this is from the ASP.NET Core not IdentityServer4 changes. Do this;
services.AddAuthentication(o =>
{
o.DefaultChallengeScheme = JwtBearerDefaults.AuthenticationScheme;
o.DefaultAuthenticateScheme = JwtBearerDefaults.AuthenticationScheme;
}).AddJwtBearer(...);
@DanielSSilva yeah, It was changed, I updated my comment to reflect those changes !
Thank you @rizamarhaban, I was aware that it was on ASP.NET and not on IS4, but the sintax changes :)
asp.net core 2.0 scopes are readonly ? how do we set { "offline_access", "email", "roles" } scopes
@domenkogler Your solution doesn't appear to do the same thing as the original "Quickstart3_ImplicitFlowAuthentication" sample. If I run the MvcClient from that sample, clicking on the "Secure" link redirects me to the IDS and all is well.
When I do as you've instructed, my secure page returns a 401 instead of going through the auth flow.
Can you help?
Anyone have finished work on net core 2.0.?
give the sample please.
I am trying to port an ASP.NET Core 1.1 client that uses hybrid flow to Core 2.0 (to get better Entity Framework experience). Like empitegayan above, I cannot find a way to specify the Scope (This may not be the full extent of my problems, but it is where I have got to):
.AddOpenIdConnect(options => {
options.Authority = "https://localhost:5000";
options.ClientId = "coretest";
options.ClientSecret = "mysecret";
options.ResponseType = "code id_token";
options.Scope = {"openid", "profile", "name", "email", "role"} // Read-only compilation error
options.TokenValidationParameters = new TokenValidationParameters {
NameClaimType = "name",
RoleClaimType = "role"
};
});
Any direction on the correct way to reconfigure hybrid flow from 1.1 to 2.0 would be appreciated.
@Neilski you need to do options.Scope.Add() to add each of them individually, you can't specify them with a constructor anymore.
after configuration you will get this error :
InvalidCastException: Cannot cast Newtonsoft.Json.Linq.JArray to Newtonsoft.Json.Linq.JToken.
Microsoft.AspNetCore.Authentication.RemoteAuthenticationHandler+<HandleRequestAsync>d__12.MoveNext()
System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw()
System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
System.Runtime.CompilerServices.TaskAwaiter.GetResult()
Microsoft.AspNetCore.Authentication.AuthenticationMiddleware+<Invoke>d__6.MoveNext()
System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw()
System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
Microsoft.AspNetCore.Diagnostics.DeveloperExceptionPageMiddleware+<Invoke>d__7.MoveNext()
Thanks @danjohnso - my small brain completely overlooked that possibility!
there is a bug with claim name
this is the response of userinfo
{
"sub": "10",
"name": [ "user.name", "User Name" ],
"AspNet.Identity.SecurityStamp": "240dc561-37ff-4eb9-a58a-f760d1b9abaa",
"role": [ "CSM_User", "dev", "admin", "SuperAdmin", "Admin", "LdapUser", "TranslationAdmin" ],
"UnitCode": "3120002566",
"JobTitle": "Kidemli Yazilim Uzmani",
"JobPhone": "0212 999 9349",
"given_name": "User",
"family_name": "Name",
"birthdate": "03/06/1978",
"email": "[email protected]",
"gender": "male"
}
as you see name claim is an array
would you please look at this link http://openid.net/specs/openid-connect-core-1_0.html#StandardClaims
standard name claim is string and with .net core 2.0 client you cannot use this result
@fadihania this is the wrong issue - open a new one with steps to repro.
Any updates here? When could release a version to support .net core 2.0?
There's a prerelease package on NuGet: https://www.nuget.org/packages/IdentityServer4/2.0.0-preview3
Yes but that's not a release. Many libraries that have a dependency on IdentityServer have their upgrades on hold because IdentityServer has not released a 2.0 update yet.
Given that it contains breaking changes, because ASP.NET Core 2.0.0 Identity has breaking changes, starting work against a prerelease package would probably get you ready sooner than waiting for the final 2.0.0 release of the package.
I agree this is helpful if you are developing with IdentityServer.
In my case, I'm using a framework that leverages IdentityServer, and I'm stuck waiting on them waiting on IdentityServer. I can't force them to develop against a prerelease version.
Has anyone tried using an asp.net core 2.0 Client?
Just tried updating one of our clients (which uses IdServer v4), but it is not working as expected, although the issue is on the client - not IdSrv. Instead of the client redirecting to the IdentityServer authority url as configured under AddOpenIdConnect it goes to /account/login - like if it were doing regular old identity auth and not recognizing the configuration.
Client's config in startup.cs looks like this
services.AddAuthentication(o => o.DefaultScheme = "Cookies")
.AddCookie(o => o.Cookie.Domain = settingSection.GetValue<string>("SiteDomainCookie") )
.AddOpenIdConnect(o =>
{
o.SignInScheme = "Cookies";
o.Authority = authority;
o.RequireHttpsMetadata = requireHttpsMetadata;
o.ClientId = clientId;
o.ClientSecret = clientSecret;
o.ResponseType = "code id_token";
o.Scope.Add("juntoz");
o.Scope.Add("offline_access");
o.GetClaimsFromUserInfoEndpoint = true;
o.SaveTokens = true;
});
// Add Identity
services.AddIdentity<IdentityAccount, IdentityRole>()
.AddUserStore<AccountStore>()
.AddRoleStore<RoleStore>();
@JamesReate, I am trying to do the same thing. Here is my Core 1.1 authentication code:
JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Clear();
app.UseCookieAuthentication(
new CookieAuthenticationOptions
{
AuthenticationScheme = AuthenticationTypes.Cookies,
AutomaticAuthenticate = true,
AccessDeniedPath = "/AccessDenied",
ExpireTimeSpan = new TimeSpan(2, 0, 0)
});
app.UseOpenIdConnectAuthentication(
new OpenIdConnectOptions
{
AuthenticationScheme = "oidc",
Authority = "https://localhost:44316",
ClientId = "coretemplate",
ClientSecret = "secret",
GetClaimsFromUserInfoEndpoint = true,
PostLogoutRedirectUri = "https://localhost:44324",
RequireHttpsMetadata = true,
ResponseType = "code id_token",
Scope = { "openid", "profile", "name", "email", "role" },
SignInScheme = AuthenticationTypes.Cookies,
SaveTokens = true,
TokenValidationParameters = new TokenValidationParameters
{
NameClaimType = JwtClaimTypes.Name,
RoleClaimType = JwtClaimTypes.Role
}
});
which I have 'more or less' replicated for Core 2.0
JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Clear();
services.AddAuthentication(
options =>
{
options.DefaultAuthenticateScheme = CookieAuthenticationDefaults.AuthenticationScheme;
options.DefaultChallengeScheme = OpenIdConnectDefaults.AuthenticationScheme;
})
.AddCookie(
options =>
{
options.SlidingExpiration = true;
options.AccessDeniedPath = "/AccessDenied";
options.ExpireTimeSpan = new TimeSpan(2, 0, 0);
})
.AddOpenIdConnect(
options =>
{
options.Authority = "https://localhost:44316";
options.ClientId = "coretemplate";
options.ClientSecret = "secret";
options.GetClaimsFromUserInfoEndpoint = true;
options.SignedOutRedirectUri = "https://localhost:44324";
options.SignInScheme = CookieAuthenticationDefaults.AuthenticationScheme;
options.ResponseType = "code id_token";
options.RequireHttpsMetadata = true;
options.SaveTokens = true;
options.Scope.Add("openid");
options.Scope.Add("profile");
options.Scope.Add("name");
options.Scope.Add("email");
options.Scope.Add("role");
options.TokenValidationParameters = new TokenValidationParameters
{
NameClaimType = "name",
RoleClaimType = "role"
};
});
In Core 1.1 this works as expected i.e. authenticates against the Identity Server and returns the expected claims and roles. In Core 2.0 this _almost_ works but the defined roles are not be mapped.
We are working on a 2.0 version - given the number of breaking changes between 1.0 and 2.0 - we need to re-test everything (in addition to substantial under-the-hood changes).
I would recommend everyone chills out a little bit - 2.0 hasn't even turned into an LTS version because also Microsoft needs more time to validate that their stuff is good enough.
For those living on the bleeding edge - go with 2.0 and use our preview package. For those that want stable and tested security software: it's done when it's done.
For using the IdentityServer4.AspNetIdentity, I do some simple workaround first just to make it work for my demo tonight. So far so good. Here is the link: https://github.com/IdentityServer/IdentityServer4.AspNetIdentity/issues/33#issuecomment-325934840
I just released another preview to nuget: 2.0.0-preview4. This should now be pretty well done for the new authentication changes in 2.0. Please have a look and provide any feedback. Given that I think all the major changes have been accounted for, I'll close this issue now. Again, if you find problems, please open a new issue.
Also, the quick start UI has been updated.
I'm now moving my attention to the EF and AspNetId projects now.
Looks like the .AddTemporarySigningCredential() is missing in the preview builds. Is this expected?
See #1139, use AddDeveloperSigningCredential instead.
As you find these sorts of things that are renamed or just moved, feel free to add to this: https://github.com/IdentityServer/IdentityServer4/issues/1057. That way we'll have a running list of what to update in the docs. Thanks.
For those of you that had problems co-hosting IdentityServer and an API in the same host, here's a sample: https://github.com/brockallen/IdentityServerAndApi
Hi everyone,
i'd like to start a project for learning with Identity server and .net core and i'd like to start with .net core 2.
Do you have any tutorial or guides on how everything can be done or do i have to start from version 1.1 and try to adapt to 2.0?
@pippo46 I think there are some articles, just googling it. I have noticed that https://github.com/aspnetboilerplate already used the .NET Core 2 with ID4. And I upgraded my sample code to .NET Core 2 yesterday as well. If you want, just have a look at https://github.com/thangchung/blog-core/tree/netcore2. Hope this help.
@thangchung thanks a lot, i'll give it a check
@thangchung - I looked at your blog-core code and noticed you add roles manually as claims to the token in identity server.
Is there a way to automatically include asp.net core identity roles in the identity server token? I still cannot get roles to come across in the token using asp.net core identity.
I set up my client as @leastprivilege shows here
In my IdentityServer config I have tried adding various Identity Resources (variants of Role, Roles) and in the client config allowed scopes.
I have looked for online examples of this on the IdentityServer and LeastPrivilege repos.
Is there a config setting I am missing to automatically load the roles from the standard asp.net core identity into the identity token claims, or must this be done manually?
@smoses2 You're right. I have added the role manually in the IdentityWithAdditionalClaimsProfileService class, but I think you could do it easier by getting all roles via UserManager
Can't upgrade to 2.0. Please help me: https://github.com/IdentityServer/IdentityServer4/issues/1625.
Thanks @thangchung. I had initially thought the asp.net identity roles magically appeared in token claims. Now after seeing your example and the one here and here - it now makes sense.
Would be great to see the IdentityServer 4 documentation describe with examples adding various claims (including roles) via IProfileService - maybe here (and maybe a quickstart addition here).
Here is how I implemented the IProfileService to move the roles to claims (modifying @damienbod code from the link above):
` public async Task GetProfileDataAsync(ProfileDataRequestContext context)
{
var sub = context.Subject.GetSubjectId();
var user = await _userManager.FindByIdAsync(sub);
var role = await _userManager.GetRolesAsync(user);
var principal = await _claimsFactory.CreateAsync(user);
var claims = principal.Claims.ToList();
claims = claims.Where(claim => context.RequestedClaimTypes.Contains(claim.Type)).ToList();
claims.Add(new Claim(JwtClaimTypes.GivenName, user.UserName));
if (role.Contains("admin"))
{
claims.Add(new Claim(JwtClaimTypes.Role, "admin"));
}
else if (role.Contains("editor")) {
claims.Add(new Claim(JwtClaimTypes.Role, "editor"));
}
else
{
claims.Add(new Claim(JwtClaimTypes.Role, "user"));
}
claims.Add(new Claim(IdentityServerConstants.StandardScopes.Email, user.Email));
context.IssuedClaims = claims;
}
`
Hi
I am new to this forum. I am also having similar issue.
I have my auth server developed using Identityserver3 framework. i am using local signing cert and ssl enabled. The auth server is working fine and i get the response to https://localhost:44300/identity/.well-known/openid-configuration.
Recently, i started developing asp.net core 2.0 webapi and i had to use the existing auth server as mentioend above.
I tried the following in core api startup.cs.
public void ConfigureServices(IServiceCollection services)
{
services.AddAuthentication("Bearer")
.AddIdentityServerAuthentication(options =>
{
options.Authority= "https://localhost:44300";
options.ApiName = "web_api";
services.AddMvc();
}
public void Configure(IApplicationBuilder app, IHostingEnvironment env, ILoggerFactory loggerFactory)
{
loggerFactory.AddConsole(Configuration.GetSection("Logging"));
loggerFactory.AddDebug();
if (env.IsDevelopment())
{
app.UseDeveloperExceptionPage();
}
// Enable CORS
app.UseCors(builder => builder.AllowAnyOrigin()
.AllowAnyMethod()
.AllowAnyHeader()
.AllowCredentials());
app.UseAuthentication();
app.UseMvc();
}
I used postman to get a token and use the token to access my api and getting error saying:
<h1>An unhandled exception occurred while processing the request.</h1>
<div class="titleerror">JsonReaderException: Unexpected character encountered while parsing value: <. Path '', line 0, position 0.</div>
<p class="location">Newtonsoft.Json.JsonTextReader.ParseValue()</p>
<div class="titleerror">InvalidOperationException: IDX10803: Unable to obtain configuration from: 'https://localhost:44300/.well-known/openid-configuration'.</div>
<p class="location">Microsoft.IdentityModel.Protocols.ConfigurationManager+<GetConfigurationAsync>d__24.MoveNext()</p>
As mentioned above, i am completely new to Identityserver.
Appreciate if anyone could help with this?
Thanks
This thread has been automatically locked since there has not been any recent activity after it was closed. Please open a new issue for related bugs.
Most helpful comment
Hire us to accelerate the process.