We may be able to reduce anti-malware false-positives by specifically signing the Tor binary we distribute. Perhaps we should sign every file we install with the executable attribute.
All 12 comments
cc: @mbacchi
Copying some tidbits from private discussion for posterity:
- This seems to be an issue only on Windows
- (I have no idea what signing executables on Windows entails)
- Current build process for tor executable is at https://github.com/brave/tor_build_scripts
- We have an open ticket to transition this to jenkins: https://github.com/brave/devops/issues/27
- Only real criterion for tor executable build process is that pj and I be able to easily run the build scripts on Linux and macOS to build and test tor without all the CI rigmarole when updating
Possibly another case of an anti-virus company blocking Brave downloads due to Tor. Reported from the community:
https://community.brave.com/t/dr-web-blocking-the-brave-download/45024
@tomlowenthal mentions this is also an applicable issue on MacOS
I've created a signed Windows tor binary and @Brave-Matt is testing it. Will investigate Mac signing next.
@mbacchi,
I installed both Kaspersky AV on my Windows 7 and 10 machines and ran the signed binary file you provided. Installation went through without issue and I don't see anything flagged in Kaspersky. Note that this was done using Kaspersky "free" -- this is the same version I used to confirm that we were getting flagged when this issue first appeared.
Please let me know if there is any additional information or testing needed on my end.
I've signed the Mac tor binary. After a suggestion by @tomlowenthal, I ran a test with the before and after binaries. Using the unsigned tor binary, Little Snitch would show that the binary was unsigned:
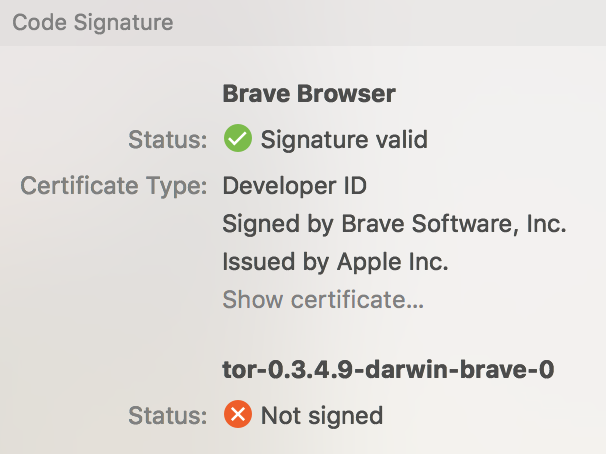
After signing it shows up as signed:
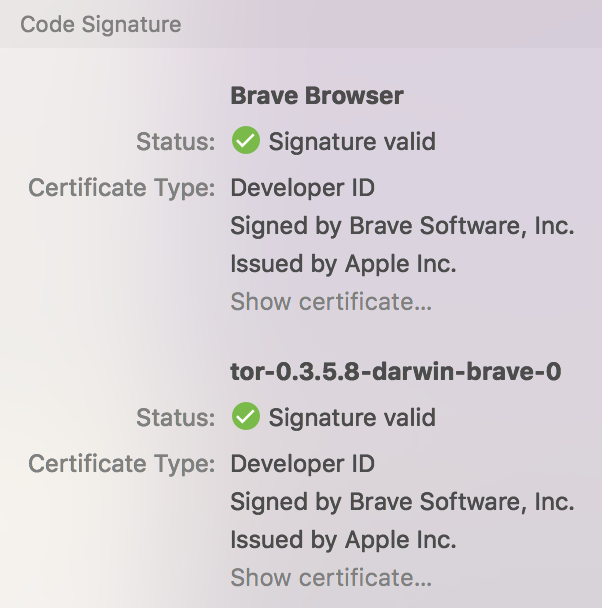
Since we've solved the problem of signing both Mac and Windows tor binaries, what's stopping us from doing the same on Linux? While Linux doesn't have the same concept of a 'signed binary' where the OS checks the signature validity(install packages are signed instead,) we could perform a gpg2 --detach-sign command thus creating an ASCII armored signature that can be verified by users.
@jumde would this be useful and is it possible to actually get the .asc signature with the tor binary when downloading the extension package?
For posterity I'll comment that it was discussed and for now we're not going to pursue signing the Linux binary.
Hi @jumde I think we are waiting on you to give us 👍on this?
@w0ts0n - we are still waiting to publish the signed binaries to the crx buckets. Will close when that's complete. Should be wrapped up today. cc: @mbacchi
Packaged and released 0.3.5.7.
Most helpful comment
@mbacchi,
I installed both Kaspersky AV on my Windows 7 and 10 machines and ran the signed binary file you provided. Installation went through without issue and I don't see anything flagged in Kaspersky. Note that this was done using Kaspersky "free" -- this is the same version I used to confirm that we were getting flagged when this issue first appeared.
Please let me know if there is any additional information or testing needed on my end.