Zeronet: CORS errors on browsers that trim HTTP referer value
Environment
- ZeroNet version: 0.6.5
- Operating system: Linux
- Web browser: Firefox/Tor Browser
- Tor status: available
- Opened port: no
Description
Recently browsers like Firefox (and since forever the Tor Browser) have been trimming everything except the host from their HTTP referer fields, meaning a referer such as:
http://127.0.0.1:43110/mysite.bit/?/&wrapper_nonce=473ca0c6827a489696f5bc40b29d1ea3ce148d793754e049eed82e1349087052
becomes:
http://127.0.0.1:43110/
While this is a win for privacy in general, it causes some issues with ZeroNet, which uses the HTTP referer to determine whether a site can make a CORS to itself:
The regex code will in fact return False when the referer is http://127.0.0.1:43110/, as we can't easily determine from which ZeroNet site the request came from (and thus can't be sure that this isn't another site trying request site files from us).
So, we need some way to correctly authenticate a CORS request from browsers who trim their HTTP referer headers.
For the record this is currently the cause of some sites having their icon fonts broken in certain browsers.
All 7 comments
Because of this, many sites cannot be shown correctly.
Relevant update in firefox:
https://blog.mozilla.org/security/2018/01/31/preventing-data-leaks-by-stripping-path-information-in-http-referrers/
Now, the referer can not be used in zeronet for cors.
Thanks for reporting I was able to reproduce in FF private mode and added a modification that allows the origin-only referrer: https://github.com/HelloZeroNet/ZeroNet/commit/350adeb52d54830422e3413e4bc1119691ed4b99
Can confirm the fix works :tada:
I'm getting another CORS issue in chrome and tor browser... not sure if this is related, but it shows that origin in 'null' in the error message:
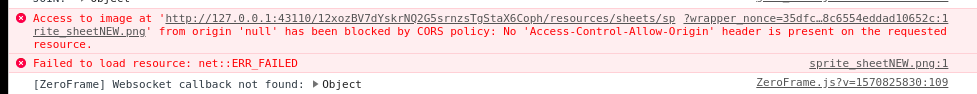
And here's the headers:
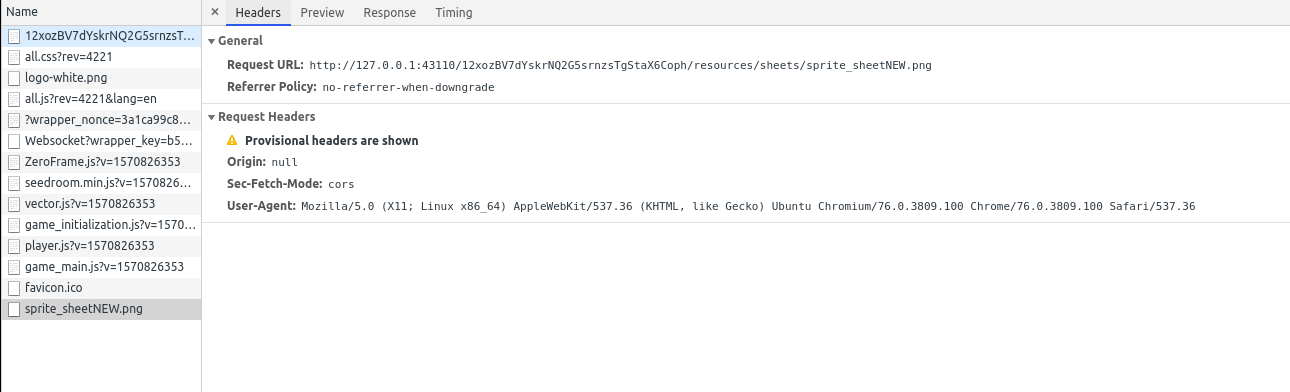
Here's the zite: http://127.0.0.1:43110/12xozBV7dYskrNQ2G5srnzsTgStaX6Coph/
(note, it uses PeerMessage for multiplayer - but single-player doesn't need that plugin)
Edit: Ok, nvm. I needed to get the ajax key from "wrapperGetAjaxKey" ZeroFrame command, then add "?ajax_key=" to the end of the URL when I do "new Image()" in javascript.
I just tested a zite in Firefix private mode... the bug is now there again even though it was fixed previously.
Thanks for reporting this should be fixed by https://github.com/HelloZeroNet/ZeroNet/commit/270f3e9ffdf45ac402aee5d8e714290af209402a in Rev4250