Webpacker: Update documentation on Rails 5.2 security policy
Original issue from Rails repo: https://github.com/rails/rails/issues/31754#event-1434257847
I think that update needed in the documentation of Webpacker. Right now if you read docs, you will think that for React everything works out of the box.
You can see info about 5.2 security updates only on Vue and Angular topics.
Plus nothing there about web sockets (they should work by default with Webpacker to do a hot reload)
Also I wonder if Rails 5.2 with Webpacker gem should pre-generate right security policy for dev mode?
All 15 comments
Thanks @savroff Please feel free to make a PR to update documentation.
Also I wonder if Rails 5.2 with Webpacker gem should pre-generate right security policy for dev mode?
Sounds like a great idea 👍
Also I wonder if Rails 5.2 with Webpacker gem should pre-generate right security policy for dev mode?
Is a good idea implementing this on Rails side but it's hard to do on Webpacker side.
I tried to do it but isn't trivial to do since we must deal not only with default generated CSP config but also with potential changes done by users to the file.
I have several ideas, wanna try them
Plus nothing there about web sockets (they should work by default with Webpacker to do a hot reload)
We have docs about connect-src in the README but maybe it isn't clear/visible enough (See Note in Development section: https://github.com/rails/webpacker#development)
Right now if you read docs, you will think that for React everything works out of the box.
Does React requires unsafe_eval or do we need it for Hot Module Reloading?
I totally missed this line.
@guilleiguaran I think we need someone who using react here :)))) I'm using vue
I totally missed this line.
Yup, I think it isn't visible enough in the docs right now, maybe it's a better idea to add a new section about CSP to the docs.
@guilleiguaran We can rewrite CSP like this:
Rails.application.config.content_security_policy do |p|
p.font_src :self, :https, :data
p.img_src :self, :https, :data
p.object_src :none
p.style_src :self, :https, :unsafe_inline
p.script_src :self, :https
p.default_src :self, :https
# Specify URI for violation reports
# p.report_uri "/csp-violation-report-endpoint"
# standard until this moment
if Rails.env.development?
p.script_src :self, :https, :unsafe_eval
p.connect_src :self, :https, 'http://localhost:3035', 'ws://localhost:3035'
end
end
This case is no issues and it just overrides prev settings. Because people will need to do it in 99% of cases.
The problem that I found trying to automatize this was that the user might already have a p.connect_src already defined (e.g for Action Cable):
Rails.application.config.content_security_policy do |p|
p.font_src :self, :https, :data
p.img_src :self, :https, :data
p.object_src :none
p.style_src :self, :https, :unsafe_inline
p.script_src :self, :https
p.default_src :self, :https
if Rails.env.development?
p.connect_src :self, :https, 'ws://localhost:3000'
end
# Specify URI for violation reports
# p.report_uri "/csp-violation-report-endpoint"
# standard until this moment
if Rails.env.development?
p.script_src :self, :https, :unsafe_eval
p.connect_src :self, :https, 'http://localhost:3035', 'ws://localhost:3035'
end
end
Not sure about what definition of p.connect_src wins in this case.
I tried to detect if the if Rails.env.development? was already in the file and use it as insertion point but it won't work if the users do something like this:
p.connect_src :self, :https, 'ws://localhost:3000' if Rails.env.development?
Yeah I guess documenting this properly makes more sense or may be a message for user indicating to add that line if using Rails 5.2 when running installer?
@savroff React works out the box except connect_src for websockets.
Yeah I guess documenting this properly makes more sense or may be a message for user indicating to add that line if using Rails 5.2 when running installer?
That sounds like a good idea
@guilleiguaran by the way for action cable, we can check if it's installed and do this:
if Rails.env.development?
p.script_src :self, :https, :unsafe_eval
p.connect_src :self, :https, 'http://localhost:3035',
'ws://localhost:3035',
'ws://localhost:3000'
end
Tested, works fine!
@guilleiguaran @gauravtiwari
Hey guys, what you think of this type of message via installing with Rails 5.2 or higher
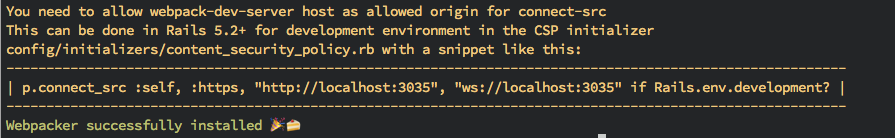
Pull request at least notify people now. I think I can close this issue.