V8-archive: [SECURITY] Weak Password Policy
Feature Request
About audited Directus version.
It has been cloned from suite repo.
Latest commit https://github.com/directus/directus/commit/1d151a9034514e3f2ec1c80001e7c5fffdef2d4e
Description:
The application does not enforce an efficient password policy on the password and security questions. As a result, it increases the chances that users select simple passwords, which could be easily enumerated in credential enumeration attacks (such as brute force and dictionary attacks).
Business risk:
An attacker can easily guess weak password with brute force attack.
Technical details:
The application does not enforce an efficient password policy on its users and enables them to select simple password combinations which could be easily enumerated.
The flaws in the policy enforcement originate from the following reasons:
- Users are not required to select passwords with enough character variations.
- Users are not required to select passwords that differentiate from the rest of their credentials.
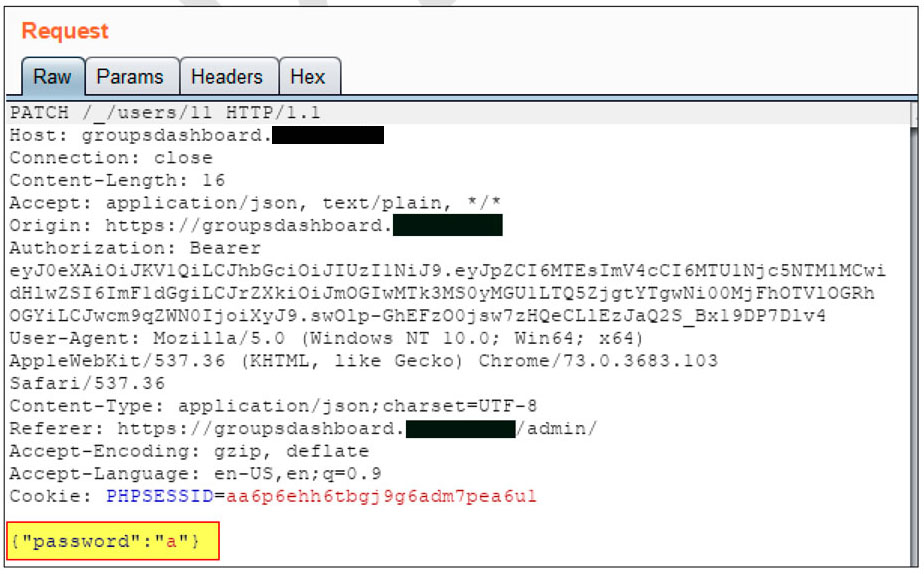
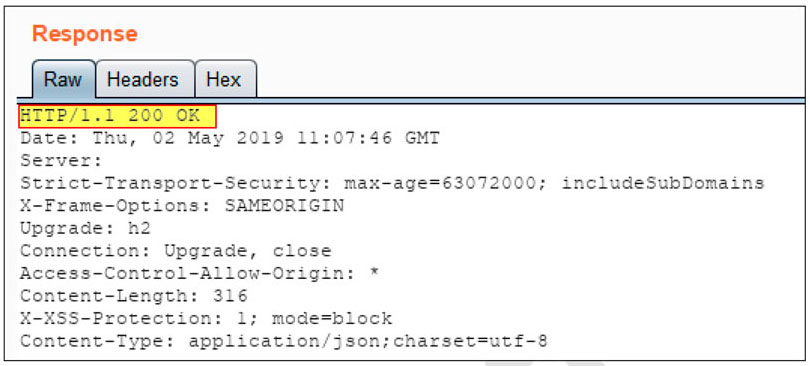
- The password policy is not enforced in the reset password mechanism. During the test, we were able to change a user password to
a:
What problem does this feature solve?
Fixes security hole.
How do you think this should be implemented?
The application should enforce an efficient password policy, which is suitable to the application sensitivity level. The password policy should be enforced according to the following guidelines:
- Set a minimum length of 8 characters for passwords.
- Each password must contain three different types of characters. It is recommended to limit the selection to uppercase and lowercase letters, and digits.
- The password must be different from the username, user ID or any other user credential.
- Enforce multi-factor authentication registration.
- The password policy must be enforced in any phase that enables password selection or alteration, including the user creation phase, the user registration phase, the password initialization phase and the password alteration phase.
- Enforce users to change their password once every quarter.
Would you be willing to work on this?
Maybe, with help/guidance from Directus team.
All 10 comments
@OscBacon sent a PR for 2FA #1031
@hemratna, our security department are more interested in these enhancements:
- Set a minimum length of 8 characters for passwords.
- Each password must contain three different types of characters. It is recommended to limit the selection to uppercase and lowercase letters, and digits.
- The password must be different from the username, user ID or any other user credential.
- Enforce users to change their password once every quarter.
I am not a big fan of software forcing certain password requirements, but am 100% on-board if this is configurable. For dev/local/whatever, sometimes it's convenient to have simple/insecure/short passwords that are human typable.
I would recommend that we create global settings to allow admins to choose their own password policy. The first option is more granular and the second is a bit easier to setup.
password_min_lengthpassword_strengthpassword_no_matchpassword_change_frequency
_These are working keys, not final names._
or...
password_policy
_This would be a slider with several "nodes", each representing a different security level. Example nodes:_- Three character minimum
- Eight character minimum
- Must contain at least three types of characters (numbers, upper/lowercase, symbols)
- Can not match name, user key, or any other user credentials
- Must be changed every 90 days
@benhaynes Can we use regex for password policy like https://stackoverflow.com/a/5142164?
We will provide a setting in admin panel to allow admin to add regex.
Perfect! That works for me.
@rijkvanzanten — we can use/make a drop-down interface that lets users easily select from a few predefined regex values, but also supports an other option that displays an input for manual entry.
RE: business risk
An attacker can easily guess weak password with brute force attack.
that's where rate limiting + 2fa comes in too.
Setting all these options up individually might become a bit tedious for the end user. I vote for the option where we have 1 field that stores a "level" of security (eg none / weak / strong) that in turn controls the other options.
Yeah, we're combining this all into one field (RegEx), and will make that more user friendly by adding a few predefined options... and an other override if they need something specific.
We will give a select field in admin setting as below listed options.
- None: No Regex
- Weak: Regex for min length validation
- Strong: Regex for min length + combination of special character + Capital and small character
The default value will be None.
Based on the user selection we will store the regex in directus_settings and validate while creating/updating password.
@rijkvanzanten Do we have support for dependent/conditionally fields in APP?
As @benhaynes suggested when user select other we need to show one additional textbox in admin setting.
Thanks @hemratna! What you described is perfect for 1-3, later we can add additional options for (_Can not match name, user key, or any other user credentials_ and _Must be changed every 90 days_).
Also, no need for a conditional field here, we will extend the core dropdown interface component to have an option for allow_other which will convert the dropdown into a text-input.
Thanks, @benhaynes for clarification. We will use the allow_other.
Most helpful comment
I am not a big fan of software forcing certain password requirements, but am 100% on-board if this is configurable. For dev/local/whatever, sometimes it's convenient to have simple/insecure/short passwords that are human typable.
I would recommend that we create global settings to allow admins to choose their own password policy. The first option is more granular and the second is a bit easier to setup.
password_min_lengthpassword_strengthpassword_no_matchpassword_change_frequency_These are working keys, not final names._
or...
password_policy_This would be a slider with several "nodes", each representing a different security level. Example nodes:_