V8-archive: [SECURITY] Directory Enumeration by HTTP Response Code
Feature Request
About audited Directus version.
It has been cloned from suite repo.
Latest commit https://github.com/directus/directus/commit/1d151a9034514e3f2ec1c80001e7c5fffdef2d4e
Description:
A possible sensitive directory has been found. This directory is not directly linked from the website. This check looks for common sensitive resources like backup directories, database dumps, administration pages, temporary directories. Each one of these directories could help an attacker to learn more about his target.
Business risk:
An attacker can enumerate and learn about the files of the web server and based on this information to plan an efficient attack.
Technical details:
During the test, we have found that we could distinguish an available directory from an unavailable directory based on the HTTP response.
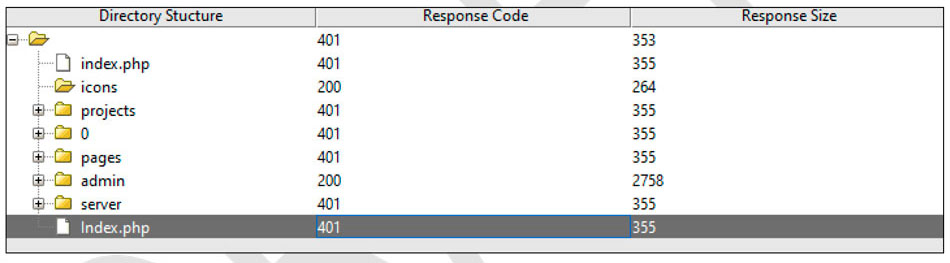
These pictures represent a difference between two requests, the 1st is for an existence directory, and the 2nd not.
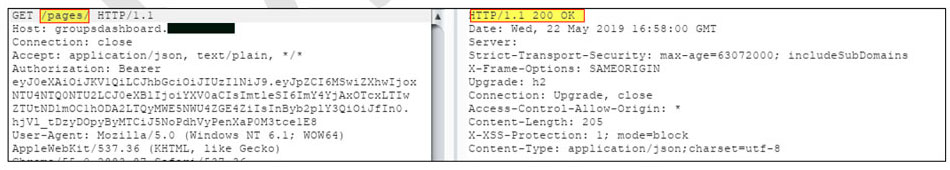
In this picture the system returns 200 OK on trying to get /pages/ directory:
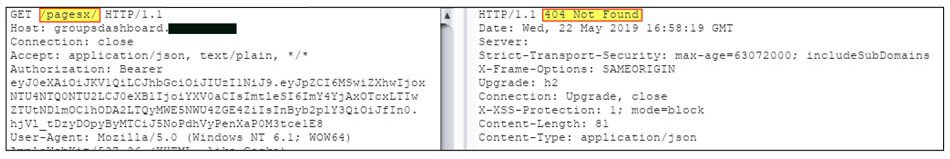
In this picture, the system returns 404 not found while trying to get /pagesx/ directory:
What problem does this feature solve?
Fixes security hole.
How do you think this should be implemented?
- It is recommended not to disclose information about the existence or non-existence of folders on the server.
- In an attempt to access a folder on the server, a generic response must be returned in a case of folder exists or does not exist on the server.
Would you be willing to work on this?
Maybe, with help/guidance from Directus team.
All 13 comments
@ybelenko I feel like this might be a server config problem, just like #985. The webserver returns info on the folders, the API isn't even used in that case.
I would close this as WONTFIX. There's no information that can be found by directory enumeration that isn't public already. And if people add custom folders that can be enumerated, they are introducing the information disclosure vulnerability themselves.
Yeah I agree. I'm also 95% sure this is not something we can fix in Directus itself in the first place, as it's a webserver config problem.
Yeah I agree. I'm also 95% sure this is not something we can fix in Directus itself in the first place, as it's a webserver config problem.
@rijkvanzanten, can you define precise config files related to that issue, beside .htaccess? Talking about Apache, certainly.
This might be of use
@rijkvanzanten, following the link provided above this issue can be solved by editing .htaccess or httpd.conf. Why you think it's better to use httpd.conf and keep same https://github.com/directus/api/blob/ddb040facaf9c7ab4652460c2a1114a09db4185a/public/.htaccess#L11-L21
No reason in particular. I think we should be able to add this to the .htaccess file as well.
@directus/api-team
As this is server related configuration, I am suggesting, as @benhaynes planned, Let's created a sperate git repo and list out all the different configurations.
We already have a htaccess file in the repo, and Apache is our officially supported server. Can't we add this in there @hemratna?
RewriteCond %{REQUEST_FILENAME} -d
RewriteRule . - [R=404]
By adding above these two lines in the .htaccess, The server returns 404 for directory regardless of whether the directory is available or not.
For example, We have the uploads directory in public folder
When we have above two lines in the
.htaccess, It will return

When we don't have above two lines in the
.htaccess, It will return

As these lines modifying the default behavior of the server, I am suggesting not to include in the Directus .htaccess.
We can add this info in Server config repo and leave on the user to use it or not.
@rijkvanzanten @ybelenko Please share your thought. I will proceed further.
I'm not .htaccess guru, as far as I remember we cannot use any conditions in it's syntax. If it's correct and we cannot use ENV or other configs(with $security_level = 'high'; for example) to set explicitly RewriteRule . - [R=404], then I'm agree with @hemratna.
So, is there any way to customize .htaccess without overwriting it?
@ybelenko I am suggesting this is a personal preference for the user and not the part of Directus.
If the user needed such a security measurement, then Directus only guide how to achieve it? by adding the steps in docs.
I am suggesting let's add this details in server config repo.
@hemratna Yeah, personal preference. I can modify .htaccess in my build for sure. The major inconvience is when I need to update Directus version with git pull origin master --ff-only I have to solve merge conflicts in .htaccess file every time. It's annoying. And I cannot add .htaccess to .gitignore because then I need to solve MCs in .gitignore every update.
UPD: That's why I don't like modify source files of 3-d party packages, because I cannot upgrade easily.
Most helpful comment
@ybelenko I feel like this might be a server config problem, just like #985. The webserver returns info on the folders, the API isn't even used in that case.