Uassets: [Request for block] Crypto Miners
I would love to see ublock start blocking the crypto miners that people have started to embed on their pages (or fetch)
URL(s) where the issue occurs
Warning, these link will end up consuming over 80% of your CPU
https://gus.host
https://spoopy.link/facebook.com
https://thepiratebay.org/search/Some%20Movie/0/99/0
Describe the issue
This page requests this: https://gus.host/coins.js via a script tag, which in turn runs a fetch to grab this script: https://coin-hive.com/lib/coinhive.min.js. This script then hammers your CPU cores.
All 111 comments
Script was removed from page, but description should give enough information
i think the focus should be on blocking coinhive not sites using coinhive 🤔
That is the request
I would love to see ublock start blocking the crypto miners that people have started to embed on their pages (or fetch)
Apparently, pirate-bay is doing it now too: https://betanews.com/2017/09/16/pirate-bay-secret-bitcoin-miner/
Apparently, pirate-bay is doing it now too: https://betanews.com/2017/09/16/pirate-bay-secret-bitcoin-miner/
Anything that abusively auto-opt-in users deserve to be blocked by default. Now the problem I am having is, in which filter lists does this go?
Given this previous issue, and the one here, maybe it's time to create a new filter lists for anti-users auto opt-in abusive behavior. Name? "Dark patterns"?
Yeah, even worse is that you can't opt out of it in some of these cases (like the two i posted), by any means other than blocking.
Dark Patterns sounds good to me.
I wonder if a situation like how https://gus.host works is ok
No...?
in which filter lists does this go?
How about adding it to ublock-badware and renaming the list to something that makes it clear that it includes issues like this one.
Thanks dude! Super fast reply :)
How about adding it to
ublock-badwareand renaming the list to something that makes it clear that it includes issues like this one.
I don't know what to think yet, I will listen to all arguments pro/for. "Dark patterns" and "Badware risks" are both self-explanatory, I suppose "badware risks" is a subset of "dark patterns"?
You could name the list badware risks/dark patterns because I do think that the two issues are related, but a standalone list is fine too.
Off topic: Anybody knows whether a link to the commit not showing in the auto-generated _"gorhill closed this 15 minutes ago"_ above is a temporary GitHub quirk or a new by-design behavior? I kind of relied a lot on the commit being auto-linked in the issue.
I think this behaviour is a quirk, because the link to the commit does not show if you also closed the issue with that commit.
If you commited a fix to an already closed issue, the link to the commit is still there.
Example: https://github.com/uBlockOrigin/uAssets/issues/678
Off-topic:
@gorhill
It does show on mobile, not sure if that's any better:
Shows on email summary sent out by GitHub as well as on mobile so must be a bug?

@gorhill The "_uBlock filters – Badware risks_" filter list should not be renamed. I do not use it as it blocks download.com which I visit.
The list in the end is subjective to how grave the user perceives the risks of the listed blocked sites to be and as it states it is a "risk" but not directly harmful.
Filters such as these should be added to the main "_uBlock filters_" list itself with additional text on why so in the wiki. A new list can be created if need be but things such as a javascript miner are directly harmful to a users machine not to say even more than ads.
@gorhill Also what is meat by "Non-pro-users auto opt-in abusive behavior."?
@aequasi Thanks for opening this issue I was going to myself but thankfully I checked if it was already there. I haven't been going through news lately and I would've definitely not become aware of this if I was not randomly checking out website tech on BuiltWith (a great website).
I was checking this out on:
https://builtwith.com/?http%3a%2f%2fvumoo.li%2fvideos%2fcategory%2ftrending-television
Here I noticed that the website was using _Coinhive_ what was described as a JavaScript miner on BuiltWith, I instantly recognized what it was and went to see the CPU usage of the website I was checking out. These things are designed to kill browser performance.
Went looking for more info and it turns out even TPB is using this. I said enough this needs to be blocked, came here to open an issue but you had already opened one 👍.
Edit: Also, here is the original report by _TorrentFreak_ about TPB using the cryptominer.
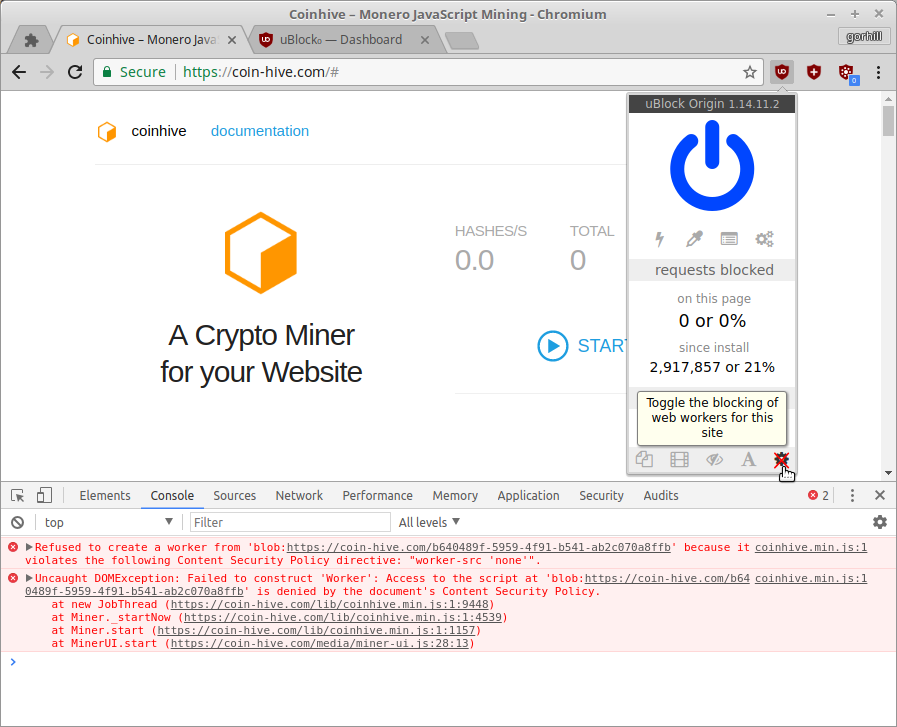
This shit is also trying to connect with WSS after blocking ||coin-hive.com/*:

wss://ws001.coin-hive.com/proxy
wss://ws002.coin-hive.com/proxy
wss://ws003.coin-hive.com/proxy
wss://ws004.coin-hive.com/proxy
wss://ws005.coin-hive.com/proxy
wss://ws006.coin-hive.com/proxy
I think that we should not mix ads and on-site cryptocurrency mining. Examples like @devsnek have an opt-out option and show transparency.
Mining cryptocurrencies on-site could be a nice way to get rid of ads. IMO, you have rushed. How cool would it be if you had an option to block ads and another option to block mining on the uBlock Origin panel? Thanks in advance.
@gangsthub FYI, @gorhill has put out a separate list for these incidents: https://github.com/uBlockOrigin/uAssets/blob/master/filters/dark-patterns.txt
It is different from the ads filter, nothing has been rushed.
Just an open source project open to ideas :)
I'd say a single quite verifiable crypto-miner during short exposures absolutely isn't worse than malicious ads. It definetly isn't badware per se, it would be a badware if injected maliciously into websites. It's another adware.
@avamander I don't see any problem in putting these filters in a special filters list (as has been done) or the main ads filter as you suggest.
I did comment above that these filters be put in the main filter but I do see now why people may have problems with this as these are not ads per say but I am all go for putting them in a different list and I think it should be a default one as well.
The main issue here is of user consent which is non existent and that fits the definiton of putting a block on it.
@gotitbro Fair enough, but how many ads ask for consent though? I would like to see them in a different list, just that people would have a choice now.
@avamander As I said above they already are in a different list: https://github.com/uBlockOrigin/uAssets/issues/690#issuecomment-330035260
What seems to be the issue here?
Shameless plug here. I wrote a tiny extension specifically for blocking coin miners (which works using a domain blacklist): https://github.com/keraf/NoCoin
I have plans to add a white list feature to temporarily allow a certain domain to use coin miners, for example if you need to pass one of these coin-hive Captchas.
@keraf I saw your extension mentioned somewhere else as well. I am not sure if I will use a separate extension for this but I have a few concerns that I just came upon for you and @gorhill.
Coinhive also has recaptchas and URL shorteners using the same CPU hashes to verify them. Here are some examples:
https://cnhv.co/6fq (Shortlink)
https://coin-hive.com/account/signup (Captcha)
Here blocking the Coinhive domain also blocks the URL shortener redirection. What to do here?
More info:
https://hackernoon.com/monetise-with-your-users-cpu-power-def05a66fff3
https://coin-hive.com/
What to do here?
Just disable uBO if the site informs you of what it's trying to do and you agree.
The reality is that despite all the ostensible wishful thinking by the authors of those miners and other schemes using user resources (bandwidth, CPU), those miners and other resource-eating approaches will be used against users _by default_ without their consent, the ones playing nice will be the exception -- this is what advertising/tracking/data mining has shown.
@AL3x3y0
This shit is also trying to connect with WSS after blocking
||coin-hive.com/*:
WebSocket connections can be blocked by uBO and a modern browser. What is your browser/version, and do you have repro steps? (looks like thepiratebay stopped using coinhive).
@gotitbro I don't know uBO well enough to suggest anything here but this is a problem I am aiming to solve in the extension I wrote with the white listing of domains (cnhv.co in this case) and replacing the Captcha by a similar size image that can be clicked to allow it to load temporarily.
do you have repro steps? (looks like thepiratebay stopped using coinhive).
@gorhill The website used by @AL3x3y0 seems to be https://gus.host.
will be abused by default
I don't think protecting yourself from non-consensual mining is abusing them in any way :/
Just disable uBO if the site informs you of what it's trying to do and you agree.
If only they would be doing that...
@gotitbro You misunderstood what I was saying. I rephrased, hopefully this is more clear.
@gorhill Oh, thanks for clarifying I thought you meant the "users" previously :)
Well I don't get it how far are users willing to go to condone radical behavior such as this to support a website. Just look at the comments on the TorrentFreak article supporting TPB: https://torrentfreak.com/the-pirate-bay-website-runs-a-cryptocurrency-miner-170916/#disqus_thread
While I understand users support for the website but how can you support uncommunicated user CPU hogging for crypto mining. I don't get it.
@gotitbro Because the alternative is worse, 3rd party malicious ads.
@Avamander Never looked at it like, you're right :)
The guys at ESET put the functioning of this in the best way possible:
Even if it can be considered as an alternative to traditional ads, this behavior is unwanted when there is no user consent. The New Jersey Division of Consumer Affairs considered that mining bitcoins on a user’s machine without consent is equivalent to gaining access to the computer.
While they are talking about crypto mining through malvertising the behavior is the same, i.e., mining without user consent though the website owners in this case are not running these miners themselves.
They also mention this:
Finally, users can protect themselves against this kind of threat by having a well-configured ad blocker or script blocker add-on installed in their browser(s).
This makes one thing clear, today adblockers are considered the first line of defense against malware, really makes one wonder of what ads have come to.
No website host is going to ask for consent of ads and by that argument every ad can be classified as malware because it's using my CPU and GPU to render itself. I do not agree with ESET's classification, a known CPU hogger is better than random javascript/image from random source.
@Avamander Well we have to keep in mind that they are talking about the ones loaded from malvertising here.
While ads do not ask for permission to load at least when they do I know they are ads not like a silent js miner running without my knowledge.
Anything that abusively auto-opt-in users deserve to be blocked by default. Now the problem I am having is, in which filter lists does this go?
Given this previous issue, and the one here, maybe it's time to create a new filter lists for non-pro-users auto opt-in abusive behavior. Name? "Dark patterns"?
Your writeup about this _pervious issue_ is still in the works?
Abstained from commenting on this further because of it, initially..
Anyway, before we get into full-blown debates about "consent" again, I just wanted to add that I believe this comparison to be a bit unfair, in my opinion, because stealthy background consumption of CPU resources is not on the same level of "evilness" as bandwidth.
Here is why, connection bandwidth can be used in a "transparent" way, i.e. without any degradation of the experience on the users' side. I'm not saying that this is always the case, definitely not, because it still can be done in wrong ways or in an abusive manner, but still, there is a "right" way possible, or let's say less harmful or minimally harmful or obtrusive way.
This is not true for cryptocurrency mining on the CPU, because this is only viable if done greedily, aggressively using as many cycles as possible (As reported herein, 80% CPU usage and maybe more). And this now is actually a degradation on the side of the user.
But as others here already pointed out, this might be a worthwhile alternative to the advertising we now have on the web, and it's issues (Potentially malicious scripts from untrusted 3rd-party sources). So we'll see how this proceeds in the future, I merely suggest to be willing to listen and to actually engage with any serious arguments brought up.
Because please don't forget this little fact that cannot be argued away: It is advertising that sustains a large part of the Internet that we have today.
it also depends on the user. I would rather have high cpu usage while reading a single article on wsj instead of a paywall, but others would say that's horrible
But as others here already pointed out, this might be a worthwhile alternative to the advertising we now have on the web
The task I impose upon myself here is to create a content blocker which work as best as possible on behalf of users who made the choice to install it, not to worry about whatever business plan of whatever entities out there.
Whoever has specific preferences regarding how businesses should generate revenues, bring this to them, here is not the place.
Please don't get me wrong, I'm perfectly aware of this. I know where we are.
This was not meant as some sort of call to action or something, or trying to instigate a discussion (certainly not here), just a simple reminder, or rather an appeal, to not just blindly or reflexively shut down any raised argument that might counter any preconceived notions about this topic.
Always mind the perspective, and don't just consider any short-term solutions or stopgap measures as definitive answers, because myopic thinking is rarely beneficial in the long run, so I merely suggest to keep in the back of your mind how this situation might play out in the future.
And don't be mistaken, I firmly believe that it is the user who should always have the last word.
to not just blindly or reflexively shut down any raised argument that might counter any preconceived notions about this topic.
@Hrxn If you look at the discuusion on this thread you will see that it has been fairly open and reciprocative of both sides of the argument. The decision which has been made is pretty clear.
And that is beauty of open source isn't it we can see exactly what happened and why.
No short term thinking is being done here. While you may say a new source of revenue is not being appreciated this specific source does not respect user choice nor does it make the user aware of the lack thereof.
Is there an easy way to turn this blocking off? I would prefer to support sites that use crypto mining as opposed to ads and I don't think that this should be blindly blocked.
Add
@@||coin-hive.com^$domain=example.com|example1.com|etc.
to support sites who ask you to allow crypto mining, or atleast inform you about it.
@okiehsch I mean globally but I think I got it, "@@||coin-hive.com" seems to have unblocked it. I want to support this revenue stream for websites, silent or not. If they abuse it I will blacklist them but I want site owners to have this option while still being able to use ublock to block ads and other misbehaving elements.
If you use @@||coin-hive.com^ just remember that to block it for a site that, in your opinion,
abuses crypto-mining you have to include the important option to override the exception filter.
||coin-hive.com^$important,domain=example.com
@Dagamant The easy way to turn it off is to not enable the Dark patterns (iirc) filter in the first place :P
Throwing another idea on how to deal with the issue here and #659 -- they have in common that they use web workers:
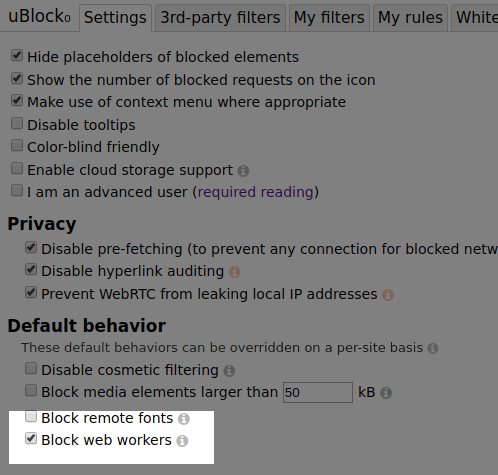
Random notes:
- Blocking would not be switched on by default, web workers have legitimate uses.
- Users decide whether to use an opt in or opt out approach with the global default behavior.
- However, just like blocking some javascript can break a site, blocking web workers can break a site, so users have to be ready to deal with this if they block web workers globally.
- Currently Firefox does not support
worker-srcCSP. It supportschild-src, but that would also blockiframetags. - Not sure if I can find a clean way to report whether a page uses web worker(s) as a badge on the web worker switch icon in the popup panel.
- That part is rather important, whether a site uses web workers is key information in deciding if the switch needs to be used.
The filter approach is not optimal, it's easy to work around a filter. However the per-site switch likely can't be worked around, and is really an easy opt-in or opt-out point-and-click solution for all users to decide for themselves, no filter list maintainers required.
These are not equivalent to ads, and people suggesting that seem to misunderstand the fundamental issue behind these crypto miners.
In any case, if the user is shown what the website wants to do, and gives consent to the website, then who cares. The user is ok with it. However, in the cases i originally submitted this issue with, and such cases i've seen since, the user is not told what is happening, or the potential harm it may cause their device. They have all been opt-in by default, and many have not (until recently) had a way to even disable. This is, by all intents and purposes, theft. You are using someone else's hardware to mine for you, without their consent. This is malicious.
and @Dagamant if you want to support a website, and their revenue stream, then unblock their website. Nothing about how that works has changed.
Is there an easy way to turn this blocking off?
Well, there's this big blue uBlock power button, I think this is still supposed to work like usual?
I hope so, manually adding some exception filters, please no, good lord..
Or did you try to achieve something different here?
you have to include the important option to override the exception filter.
||coin-hive.com^$important,domain=example.com
Can't we use a domain exclusion on this as well?
@@||coin-hive.com^$domain=~example.com
This is, by all intents and purposes, theft. You are using someone else's hardware to mine for you, without their consent. This is malicious.
@aequasi I completely agree with your comment but here is a counter argument (which I do not support) couldn't blocking website advertising be seen as theft as well?
Kinda sad to see that the miner on my own project site stopped randomly today and threw me some errors that it couldn't establish a connection to the scripts / servers.
I completely understand it though with all the current controversy around it.
TPB's approach was bullshit, I do agree on that. They implemented it without even telling anyone about it.
My approach, albeit in a small testing group, was that it was opt-in by default but the users were told about it the first time they visited the site, after which they could turn it off on a page and then it was... well, disabled. Until they would want to enable it again, obviously.
To sum the whole "let's just do it opt-in by default and not tell anyone about it" stuff up in a single picture:

And no, I'm not here to shit-talk or attack anyone personally. I fully respect all of your guys opinions on this choice.
As a couple people already said, it's possible to disable uBlock on certain websites anyway if the user wants to support them. (Although I am not sure if that could be done for only the miners? As in, if there's perhaps a website that does both, but I only want the miner to run and not the ads to show?)
And no, I'm not here to shit-talk or attack anyone personally.
Users can easily opt-in to the respectful implementation (disabling uBO for the site/page), they can't easily opt-out of the abusive implementation -- hence the only safe approach is to block known miners by default.
As in, if there's perhaps a website that does both, but I only want the miner to run and not the ads to show?
Having ads served along with the miner kind of defeat the rationale of having the miner, which is being marketed as a way to monetize without resorting to ads. In any case, you are free to design your web sites as you wish, and users of uBO are free to opt-in to whatever you serve them. Talk to your users, they are the one making the decision, uBO is just a tool they use to get back the ability to decide.
Anyway, yea. My plans for implementing this would be on one single page that users could have open in the background (kind of the approach that the Coin-Hive team did on the "real world use case" website).
They can then later on even redeem it to stuff.
That'd be a win/win situation, effectively.
//EDIT: Reason being as to why I would want to do it this way is because I want to give people the opportunity to do it. Not force them to do it.
I wouldn't want this to happen to me either. I, too, would be pissed if my CPU would suddenly be at 80% and I wouldn't know why.
If I would however know why it is at 80%, I would at least understand it. Granted, 80% is obviously too high, but you should get my point.
@Lordmau5 I don't understand what the issue even is here?
I would like to have per-site cryptominer toggle indeed, I'd really rather not start maintaining my own list of rules to exclude some sites and then forget that I've enabled some specific cryptominer etc.
@Lordmau5 @Avamander Both of your points are addressed by the fact that anew list for such issues has been created for people who would want to block stuff such as this.
In regards to allowing some sites that depends on whether the new filter list will be enabled by default and warrant such action.
@gotitbro no, blocking ads cannot be considered as theft. You are not illegally (or even legally) taking someone's property or services without their consent.
@Lordmau5 the purpose of ublock is to block ads and the like. If you dont want something to be blocked, then turn it off for that site. Thats how ublock has always worked, and i see absolutely no reason for that to change now.
@gorhill https://load.jsecoin.com/* should also get blocked - also web based mining.
@aequasi That's definetly debatable, they expect you to watch ads in exchange of content, how is that different from expecting you to use your CPU in exchange of content. Same thing.
Not debatable. Take that to a judge please.
Can laugh all you want @Avamander, but this is how the law works.
https://load.jsecoin.com/*should also get blocked - also web based mining.
Given this previous issue, and the one here, maybe it's time to create a new filter lists for anti-users auto opt-in abusive behavior. Name? "Dark patterns"?
@gorhill I recommend name "Resource Abuse" as better description
@nshopik I agree with your suggestion. "Dark patterns" is a way too broad category.
@gorhill I didn't know that names defined the purpose of the script. Well if it does then yes changing the name would be a nice idea.
Why not just make a off-by-default crypto currency miners list? It's unlikely this won't increase in popularity.
Why not just make a off-by-default crypto currency miners list?
https://github.com/uBlockOrigin/uAssets/issues/690#issuecomment-330552749
That doesn't really fly. You are choosing to block something good, because someone decided to abuse it. That's not how life works, you do not punish the innocent. Otherwise, we'd be banning everything.
THen dont use ublock.
Nice A+ logic there batman, back to school with you.
By using uBlock you opt into blocking the things you want. Want to block ads? Use the ad block list. Want to block tracking? Use the tracking list. Don't want to block miners? Oops, sorry, that's forced onto you just because you wanted to block the other two.
Scope is a basic fundamental of project development. It's laughable that you don't know this considering your history.
@funkydude If you had actually read this issue fully you'd know there's a separate list.
@Avamander If you had read the issue you'd have seen the reference to #712
Don't want to block miners? Oops, sorry, that's forced onto you just because you wanted to block the other two.
@funkydude How is it forced if a different list has been created? This list is not blocking crypto miners just for the sake of it. this one was blocked because of no user choice. Other things which abuse user resources are also added to this list such as Edgemesh.
@funkydude "It is already taken care of in uBO as the crypto miner has been blocked in a separate filter list." SEPARATE LIST, enable or disable as you wish.
It seems really difficult for you to open that link and read it. Please do so before further making a fool of yourself. It is blocked with or without this separate list.
@funkydude What's the issue here? Are you unable to disable lists that you're not satisfied with?
@funkydude I don't know how this is a uBO issue. The site has been blocked in EasyPrivacy and uBO blocks it with a different list.
Maybe try discussing this on the EasyList forums.
@gotitbro EL author has no interest in discussing hacking a bitcoiner miner into his tracking list.
@Avamander It should be whitelisted unless the uBO list is enabled. Further down the line, there should be a toggle option or simply a dedicated miners list.
@funkydude Here is the official EasyList forum: https://forums.lanik.us. You can discuss freely there no qualms.
Also, why should it be whitelisted when it isn't even blocked by default? The list will have to be manually enabled in the first place.
or you could use a simple filter like this:
||coin-hive.com^$third-party,badfilter
@gotitbro you seem to acknowledge that people can abuse a bitcoin miner maliciously, and your solution for this is blocking it for everyone, even if they are not using it maliciously.
However, you don't seem to acknowledge the ability for list authors to abuse the power they have to block whatever they want. You don't think uBO should protect the user from this form of abuse, but it should protect them from the former form of abuse (with a wide ranging block).
Am I understanding this correctly?
I think there are ad networks that aren't evil, I demand that you whitelist the entire network until a specific filter is enabled with a bunch of other stuff you do not want to disable
This will never work. Don't use lists you don't like, it's that simple.
@Avamander Whether an ad is evil or not is irrelevant. People install an [ad] blocking list to block ads, not bitcoin miners.
The same can be said for a dedicated miners list. Whether they are evil or not is irrelevant, they can use the list to block them all, and ONLY them.
This is what I mean by scope.
@funkydude uBO has and always will be about protecting users as they wanted it to when they installed it in the first place. Coinhive is being blocked as it gives no user consent, give me one site which uses Coinhive with user consent maybe then we can take this further.
List authors aren't abusing anything they do what they do in the interest of users and that is what is being done. Open source being the mindset behind it all.
People install an [ad] blocking list to block ads, not bitcoin miners.
And you bring this up again which ad list is blocking the miners btw?
@funkydude so your proposal would be to add
||coin-hive.com^$third-party,badfilter
||jsecoin.com^$third-party,badfilter
to uBO-filter list to deal with the filters in EasyPrivacy, which you think are beyond the scope of that list?
@okiehsch That is what I think is trying to be communicated. But I don't think it should be done.
@okiehsch which could then be overwritten by a dedicated miners list if a user wanted to block miners, evil or not.
I don't think a specific miners list would be created as it is beyond this projects scope.
It doesn't have to be started by this project, you can debate that at will.
I've already seen people linking to lists with only this entry, on various forums and news articles.
Then why is it being debated here in the first place?
I am not talking about the EasyPrivacy issue. I am talking about creating the miners list which as I said seems to be beyond this project's scope and to which you also seem to agree.
I never said I agree that a miners list is beyond the scope of this project, I don't care who wants to do it, I'm stating that's the "proper" way to deal with this situation.
A list dedicated for ads.
A list dedicated for trackers.
A list dedicated for miners.
This entire ticket was debating the bitcoin miner issue, I'm not sure why you think it should not be debated.
Creating a miner list was never the scope of this issue. It was about blocking a specific one that was being abused majorly.
It doesn't need a debate if you want a miners list that badly maybe you can create one. If its good enough it might even become the de facto list for blocking miners.
@funkydude even if one agrees with you that the filters in EasyPrivacy are beyond the scope of that list,
disabling them in uBO-filters via
||coin-hive.com^$third-party,badfilter
||jsecoin.com^$third-party,badfilter
would make dedicated anti crypto-miner lists like
https://github.com/hoshsadiq/adblock-nocoin-list/blob/master/nocoin.txt pointless, because they would be disabled too.
@funkydude And you filter creation debate has already been solved as @okiehsch has provided us with a working example.
@okiehsch I'm open to suggestions. How would one prevent a list author abusing a specific list for blocking something out-of-scope without harming a legitimate list?
@gotitbro Personal lists are not a solution, sorry. If you're not interested in this debate, stop partaking in it.
@okiehsch , it seems
||coin-hive.com^$third-party,important overwrites ||coin-hive.com^$third-party,badfilter , so only an uBo specific list could fix this "issue".
@mapx- technically it does not overwrite it, it is a different filter, so badfilter does not apply, but you are correct of course, a uBO-"Resource Abuse" list could work arround it, but some third-party lists like
https://github.com/hoshsadiq/adblock-nocoin-list/blob/master/nocoin.txt would have no clue why it does not work.
@funkydude Who said the list has to be personal put it on GitHub. You are just humdrumming the same thing again and again. When provided with alternatives you don't acknowledge them.
As to stopping an author from the abuse of power short answer we can't. But I don't believe anyone is abusing their power or is going to. These projects have been up for years with many supporters.
@gotitbro I'm the one bringing up a valid debate, you're the one moaning that's it happening. Pro tip: leave.
Users that opt into a TRACKING list do not expect to be blocking bitcoin miners. It is a simple abuse of their trust. When you tell a user "this list blocks trackers", don't lie to them. Telling people to "use other lists as a workaround for having your trust abused" is not a viable solution.
We should be debating this and considering all the angles, instead of smacking it down with a giant hammer. You risk killing the potential of a real solution for replacing ads.
The insults you are lashing out with are doing nothing for your side of the argument @funkydude. Try to have a little bit more tact when you are having a "debate", and people might be more apt to work with you.
You risk killing the potential of a real solution for replacing ads.
Good. That's the purpose of ublock. To block stuff that people find annoying.
I find crypto miners in my browser to be annoying. If I find a site that is doing it well enough to not be blocked, then I'll whitelist the site.
The insults you are lashing out with are doing nothing for your side of the argument
You said something dumb and got schooled, not my problem. Also I don't really care what you think of me, as I don't hold you in a high regard either, considering your attitude earlier. If you dismiss valid talking points on the grounds of not liking the person speaking them, that says more about you.
Good. That's the purpose of ublock. To block stuff that people find annoying.
No. The purpose of uBlock is to block what you tell it to block. That can be ads, trackers, miners, or entire websites. "uBlock" not "uSafety". If I've told it to block trackers, it needs to block trackers, not crypto miners.
@gorhill can we lock this. This is quickly going to turn into just snipes and jabs, and i have no interest having my name dragged through the mud.
@funkydude "If I've told it to block trackers, it needs to block trackers, not crypto miners." Yeah, that's not how it works, you can't tell uBlock to "block ads" or "block trackers", you enable lists, and if the list is unsuitable for you then DISABLE IT. Stop complaining here.
@Avamander I honestly don't understand your logic. The lists you choose to install are the very action of you choosing what you want to block. If you don't enable any lists, you won't block anything.
I have to wonder if you'd have the same attitude if it was something being blocked that you didn't want blocked, or if you just have this attitude because you're ok with having miners blocked.
@gorhill websites have started crypto mining using random domains:
https://github.com/jspenguin2017/uBlockProtector/issues/636#issuecomment-334317456
The only practical solution I can come up with, is
oload.info##script:inject(abort-on-property-read.js, WebAssembly)
or
oload.info##script:inject(abort-current-inline-script.js, document.createElement, (/[A-Z0-9]{8}-[A-Z0-9]{4}-[A-Z0-9]{4}/.test(key)
or do you prefer a different fix?
Edit: https://github.com/uBlockOrigin/uAssets/commit/638ad54bc2bcf79e4cee55fd41c256eb3f204d7a
Most helpful comment
Anything that abusively auto-opt-in users deserve to be blocked by default. Now the problem I am having is, in which filter lists does this go?
Given this previous issue, and the one here, maybe it's time to create a new filter lists for anti-users auto opt-in abusive behavior. Name? "Dark patterns"?