Test-infra: [prow] GitHub Check Runs API support
What happened:
We're using prow and travis-ci.com combination in our repo, to make tide manage PR auto-merging, we add the following branch-protection configuration to config.yam to make sure travis jobs success before auto-merging.
tide:
...
context_options:
# Use branch protection options to define required and optional contexts
from-branch-protection: true
# Treat unknown contexts as optional
skip-unknown-contexts: true
branch-protection:
orgs:
XXX:
repos:
xxxxx:
protect: true
exclude:
- "^revert-" # don't protect revert branches
- "^dependabot/" # don't protect branches created by dependabot
- "^greenkeeper/" # don't protect branches created by greenkeeper
required_status_checks:
contexts:
- "Travis CI - Pull Request"
However, the PR is always pending for the reason of Not mergeable. Job Travis CI - Pull Request has not succeed...:
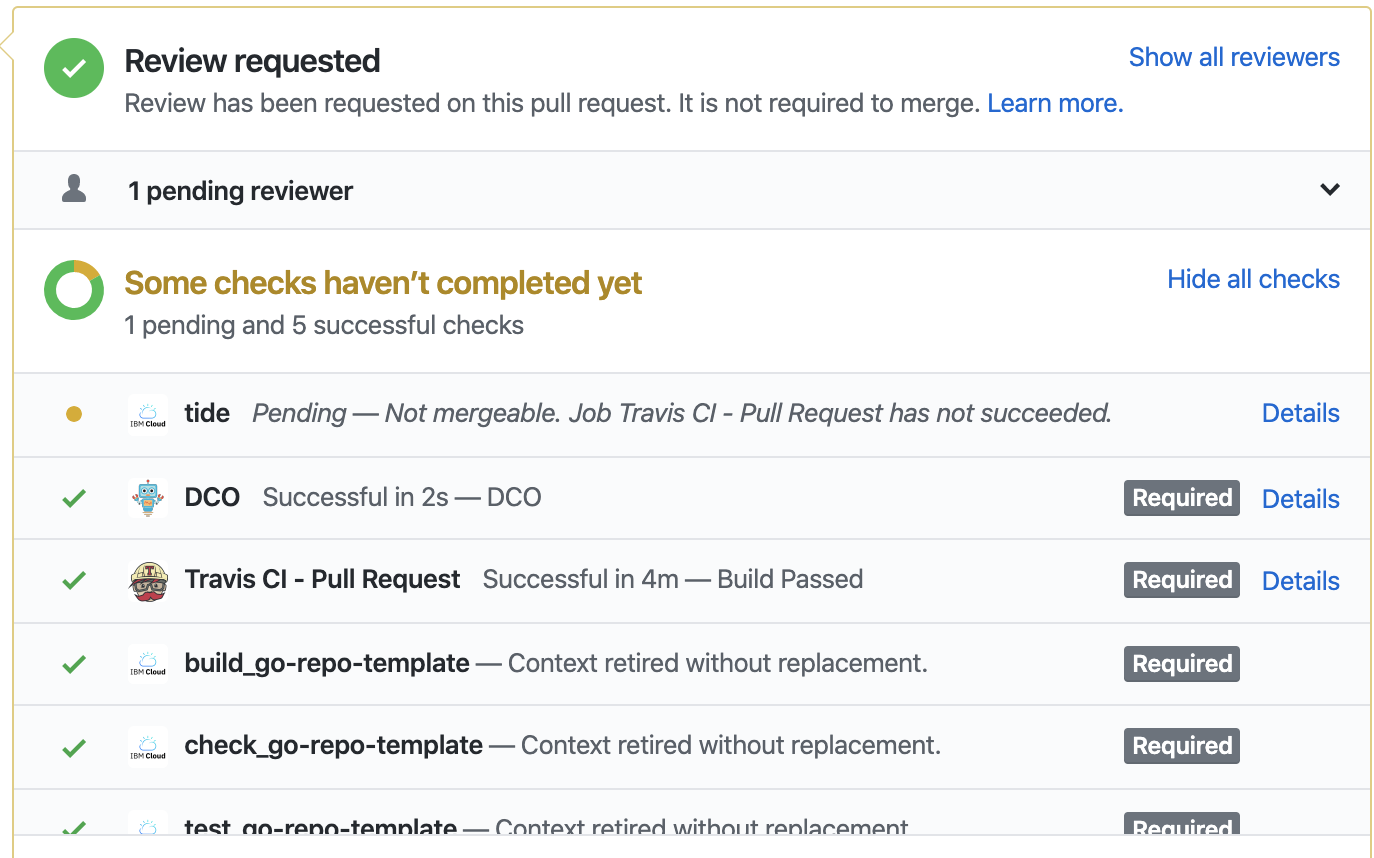
After investigation, the travis-ci.com has deprecated Github status check API, instead, all the repos managed by travis-ci.com update status report with the new GitHub Check Runs API, see: https://blog.travis-ci.com/2018-09-27-deprecating-github-commit-status-api-for-github-apps-managed-repositories
As a result, tide can't get the status of travis jobs from travis-ci.com, that should be the reason of pending PR.
The question is that do we have plugins that support *travis-ci.com check run API?*
Looks like Travis recommend to use travis-ci.com for new users and projects (both private and public).
What you expected to happen:
How to reproduce it (as minimally and precisely as possible):
Please provide links to example occurrences, if any:
Anything else we need to know?:
/cc @gyliu513 @clyang82
All 16 comments
@BenTheElder Any insight for this?
/assign
/area prow
hey @morvencao , thanks for raising the issue. It is a problem we are aware of and I thought we already had an issue for it, but I cant find it :thinking:
I am not sure what the current plan is, as the checkruns api is in developer preview and may change without advance notice.
Also, to my knowledge Ben is not currently involved with Prow development anymore so wont know much here. @stevekuznetsov or @fejta might know more.
@alculquicondor Thanks for quick response. I found a similar issue about the new DCO which also moved to Github check run API, see: https://github.com/kubernetes/test-infra/issues/9187
Looks like that we need to implement the internal plugin to make this work.
Unsubscribing as it seems that I was summoned by mistake.
Issues go stale after 90d of inactivity.
Mark the issue as fresh with /remove-lifecycle stale.
Stale issues rot after an additional 30d of inactivity and eventually close.
If this issue is safe to close now please do so with /close.
Send feedback to sig-testing, kubernetes/test-infra and/or fejta.
/lifecycle stale
Stale issues rot after 30d of inactivity.
Mark the issue as fresh with /remove-lifecycle rotten.
Rotten issues close after an additional 30d of inactivity.
If this issue is safe to close now please do so with /close.
Send feedback to sig-testing, kubernetes/test-infra and/or fejta.
/lifecycle rotten
Rotten issues close after 30d of inactivity.
Reopen the issue with /reopen.
Mark the issue as fresh with /remove-lifecycle rotten.
Send feedback to sig-testing, kubernetes/test-infra and/or fejta.
/close
@fejta-bot: Closing this issue.
In response to this:
Rotten issues close after 30d of inactivity.
Reopen the issue with/reopen.
Mark the issue as fresh with/remove-lifecycle rotten.Send feedback to sig-testing, kubernetes/test-infra and/or fejta.
/close
Instructions for interacting with me using PR comments are available here. If you have questions or suggestions related to my behavior, please file an issue against the kubernetes/test-infra repository.
/reopen
@alvaroaleman: Reopened this issue.
In response to this:
/reopen
Instructions for interacting with me using PR comments are available here. If you have questions or suggestions related to my behavior, please file an issue against the kubernetes/test-infra repository.
~I somehow thought this would require a github app, but it works perfectly fine with a personal access token, just tested that.~
Listing check runs via a personal access token seems to work, but creations fail and mention that this requires a github app:
curl -XPOST -H "Content-Type: application/json" -H "Accept: application/vnd.github.antiope-preview+json" -H "Authorization: Bearer $TOKEN" https://api.github.com/repos/alvaro-bot-prow/test-repo/check-runs --data '{"name":"alvaro-test-check","head_sha":"8091623c4f05a60ffb85255104dd2f7f8368681b","status":"completed"}'
{
"message": "You must authenticate via a GitHub App.",
"documentation_url": "https://docs.github.com/rest/reference/checks#create-a-check-run"
}
Hi @alvaroaleman, is there any way or plan to solve this problem?
@Rustin-Liu I believe this could be fixed by making Tide List and check the gitbub check runs in addition to the normal statuses
/remove-lifecycle rotten
/lifecycle frozen
to keep this around as a known issue
/assign
Most helpful comment
~I somehow thought this would require a github app, but it works perfectly fine with a personal access token, just tested that.~
Listing check runs via a personal access token seems to work, but creations fail and mention that this requires a github app: