Terraform-provider-azurerm: azurerm_postgresql_virtual_network_rule - FeatureSwitchNotEnabled
Community Note
- Please vote on this issue by adding a 👍 reaction to the original issue to help the community and maintainers prioritize this request
- Please do not leave "+1" or "me too" comments, they generate extra noise for issue followers and do not help prioritize the request
- If you are interested in working on this issue or have submitted a pull request, please leave a comment
Terraform (and AzureRM Provider) Version
Terraform v0.12.24
- provider.azurerm v2.27.0
- provider.random v2.3.0
- provider.tls v2.2.0
Affected Resource(s)
azurerm_postgresql_virtual_network_rule
Terraform Configuration Files
resource "azurerm_virtual_network" "hub" {
name = local.vnet_hub_name
location = azurerm_resource_group.hub.location
resource_group_name = azurerm_resource_group.hub.name
address_space = [local.vnet_hub_iprange]
ddos_protection_plan {
id = azurerm_network_ddos_protection_plan.hub.id
enable = true
}
}
resource "azurerm_subnet" "jump" {
name = local.jump_subnet
resource_group_name = azurerm_resource_group.hub.name
virtual_network_name = azurerm_virtual_network.hub.name
address_prefixes = [local.jump_subnet_iprange]
service_endpoints = [ "Microsoft.Sql" ]
}
resource "azurerm_virtual_network" "spoke" {
name = local.vnet_spoke_name
location = azurerm_resource_group.spoke.location
resource_group_name = azurerm_resource_group.spoke.name
address_space = [local.vnet_spoke_iprange]
}
resource "azurerm_subnet" "aks" {
name = local.aks_subnet
resource_group_name = azurerm_resource_group.spoke.name
virtual_network_name = azurerm_virtual_network.spoke.name
address_prefixes = [local.aks_subnet_iprange]
enforce_private_link_endpoint_network_policies = true
service_endpoints = [ "Microsoft.Sql" ]
}
resource "azurerm_subnet" "sql" {
name = local.sql_subnet
resource_group_name = azurerm_resource_group.spoke.name
virtual_network_name = azurerm_virtual_network.spoke.name
address_prefixes = [local.sql_subnet_iprange]
service_endpoints = [ "Microsoft.Sql" ]
enforce_private_link_endpoint_network_policies = true
}
resource "azurerm_virtual_network_peering" "hubtospoke" {
name = local.hub_to_spoke_vnet_peer
resource_group_name = azurerm_resource_group.hub.name
virtual_network_name = azurerm_virtual_network.hub.name
remote_virtual_network_id = azurerm_virtual_network.spoke.id
allow_gateway_transit = true
}
resource "azurerm_virtual_network_peering" "spoketohub" {
name = local.spoke_to_hub_vnet_peer
resource_group_name = azurerm_resource_group.spoke.name
virtual_network_name = azurerm_virtual_network.spoke.name
remote_virtual_network_id = azurerm_virtual_network.hub.id
use_remote_gateways = true
allow_forwarded_traffic = true
depends_on = [
azurerm_virtual_network_gateway.vpn,
]
}
resource "random_password" "postgres_password" {
keepers = {
resource_group = azurerm_resource_group.spoke.name
}
length = 32
special = true
override_special = "_%@"
}
resource "azurerm_postgresql_server" "postgres" {
name = local.postgresql_name
location = azurerm_resource_group.spoke.location
resource_group_name = azurerm_resource_group.spoke.name
sku_name = "GP_Gen5_2"
storage_mb = 25600
backup_retention_days = 7
geo_redundant_backup_enabled = false
auto_grow_enabled = true
administrator_login = var.postgresUsername
administrator_login_password = random_password.postgres_password.result
version = "11"
ssl_enforcement_enabled = true
public_network_access_enabled = false
ssl_minimal_tls_version_enforced = "TLS1_2"
threat_detection_policy {
enabled = true
email_account_admins = true
email_addresses = [local.database_email_alerts]
retention_days = 10
storage_endpoint = azurerm_storage_account.sql_backup.primary_blob_endpoint
storage_account_access_key = azurerm_storage_account.sql_backup.primary_access_key
}
}
resource "azurerm_postgresql_database" "camunda" {
name = "camunda"
resource_group_name = azurerm_resource_group.spoke.name
server_name = azurerm_postgresql_server.postgres.name
charset = "UTF8"
collation = "English_United Kingdom.1252"
}
resource "azurerm_private_endpoint" "sql_postgres" {
name = local.postgresql_private_endpoint
location = azurerm_resource_group.spoke.location
resource_group_name = azurerm_resource_group.spoke.name
subnet_id = azurerm_subnet.sql.id
private_service_connection {
name = local.postgresql_private_link
private_connection_resource_id = azurerm_postgresql_server.postgres.id
is_manual_connection = false
subresource_names = [ "postgresqlServer" ]
}
}
resource "azurerm_postgresql_virtual_network_rule" "allow_aks" {
name = local.postgres_firewall_allow_aks_subnet
resource_group_name = azurerm_resource_group.spoke.name
server_name = azurerm_postgresql_server.postgres.name
subnet_id = azurerm_subnet.aks.id
}
resource "azurerm_postgresql_virtual_network_rule" "allow_vpn" {
name = local.postgres_firewall_allow_vpn_subnet
resource_group_name = azurerm_resource_group.spoke.name
server_name = azurerm_postgresql_server.postgres.name
subnet_id = azurerm_subnet.vpn.id
}
resource "azurerm_postgresql_virtual_network_rule" "allow_jump" {
name = local.postgres_firewall_allow_jump_subnet
resource_group_name = azurerm_resource_group.spoke.name
server_name = azurerm_postgresql_server.postgres.name
subnet_id = azurerm_subnet.jump.id
}
Expected Behavior
I should have a vnet rule created for each of the three networks allowing access to postgres.
Actual Behavior
Error: Error submitting PostgreSQL Virtual Network Rule "postgres-firewall-allow-aks-subnet" (PostgreSQL Server: "postgres", Resource Group: "spoke-rg"): postgresql.VirtualNetworkRulesClient#CreateOrUpdate: Failure sending request: StatusCode=405 -- Original Error: Code="FeatureSwitchNotEnabled" Message="Requested feature is not enabled"
on Terraform/postgres.tf line 91, in resource "azurerm_postgresql_virtual_network_rule" "allow_aks":
91: resource "azurerm_postgresql_virtual_network_rule" "allow_aks" {
Error: Error submitting PostgreSQL Virtual Network Rule "postgres-firewall-allow-gateway-subnet" (PostgreSQL Server: "postgres", Resource Group: "spoke-rg"): postgresql.VirtualNetworkRulesClient#CreateOrUpdate: Failure sending request: StatusCode=405 -- Original Error: Code="FeatureSwitchNotEnabled" Message="Requested feature is not enabled"
on Terraform/postgres.tf line 98, in resource "azurerm_postgresql_virtual_network_rule" "allow_vpn":
98: resource "azurerm_postgresql_virtual_network_rule" "allow_vpn" {
Error: Error submitting PostgreSQL Virtual Network Rule "postgres-firewall-allow-jump-subnet" (PostgreSQL Server: "postgres", Resource Group: "spoke-rg"): postgresql.VirtualNetworkRulesClient#CreateOrUpdate: Failure sending request: StatusCode=405 -- Original Error: Code="FeatureSwitchNotEnabled" Message="Requested feature is not enabled"
on Terraform/postgres.tf line 105, in resource "azurerm_postgresql_virtual_network_rule" "allow_jump":
105: resource "azurerm_postgresql_virtual_network_rule" "allow_jump" {
All 11 comments
Hey @pixie79 thanks for taking the time to open this. I did some digging and it looks like having public_network_access_enabled = false with your server is the source of your problem. I see the same issue when I add that and try and run a basic test.
With that in mind, I'm going to close this down but feel free to reopen it if you still continue to experience issues.
@mbfrahry I do not believe that is true; I have the same set of rules for SQL server and they work fine.
Also the point of these rules is to allow access to the resource from other networks via the private endpoints when public access is disabled. As such it would make no sense to allow public access?
Why is this closed? There should be no public access at all to our SQL server. This should be done by Private Endpoints which I can do in the console.
Ah, I think I found the part we're missing from what @thomasbeauvais called out! It looks like we need a new resource for private endpoint connections. Does this https://github.com/Azure/azure-sdk-for-go/blob/master/services/postgresql/mgmt/2020-01-01/postgresql/privateendpointconnections.go like it'll unlock fix this issue?
i think so
I'm using slightly newer Terraform stack than @pixie79
❯ terraform version
Terraform v0.13.3
+ provider registry.terraform.io/hashicorp/azurerm v2.29.0
but with simpler configuration: single virtual network, single subnet and also observing the same issue:
Error: Error submitting PostgreSQL Virtual Network Rule "rg-ts-pg-kong-vnet-rule" (PostgreSQL Server: "rg-ts-pg-kong", Resource Group: "rg-ts"):
postgresql.VirtualNetworkRulesClient#CreateOrUpdate:
Failure sending request: StatusCode=405
-- Original Error: Code="FeatureSwitchNotEnabled" Message="Requested feature is not enabled"
Is it known which version of the provider is expected to include the fix?
Is https://docs.microsoft.com/en-us/azure/postgresql/howto-manage-vnet-using-cli currently recommended as the workaround?
I have the same error as @mloskot. I don't understand how I'm supposed to create a private link from a VNet to a PostgreSQL Server if this doesn't work. Just firewall in the whole subnet? that's dumb.
So I have this same issue. The discovery I made when trying to do this manually in the portal is this:
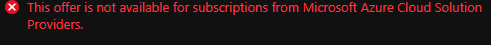
The button to add to an existing VNET is disabled (even though there is a VNET) and when clicking on 'Create new VNET' the above is shown.
Which is... sad. Can anyone confirm this? I'm unable to find any official documentation on this.
Update: I can confirm that it works if public access is enabled (even in a CSP subscription). But as others have said this does not make any sense but is not a Terraform issue.
I have also run into this issue as well.
Most helpful comment
@mbfrahry I do not believe that is true; I have the same set of rules for SQL server and they work fine.
Also the point of these rules is to allow access to the resource from other networks via the private endpoints when public access is disabled. As such it would make no sense to allow public access?