Terraform-provider-azurerm: Problem with IP Restriction rules in azurerm_app_service resource
Hi,
We stepped into the strange problem while working with "IP Restriction" azurerm_app_service resource functionality. There is a need to manage this IP Restriction rules externally by using PowerShell script and not with Terraform. Below are detailed steps we followed:
1) We successfully applied needed restriction rules via script.
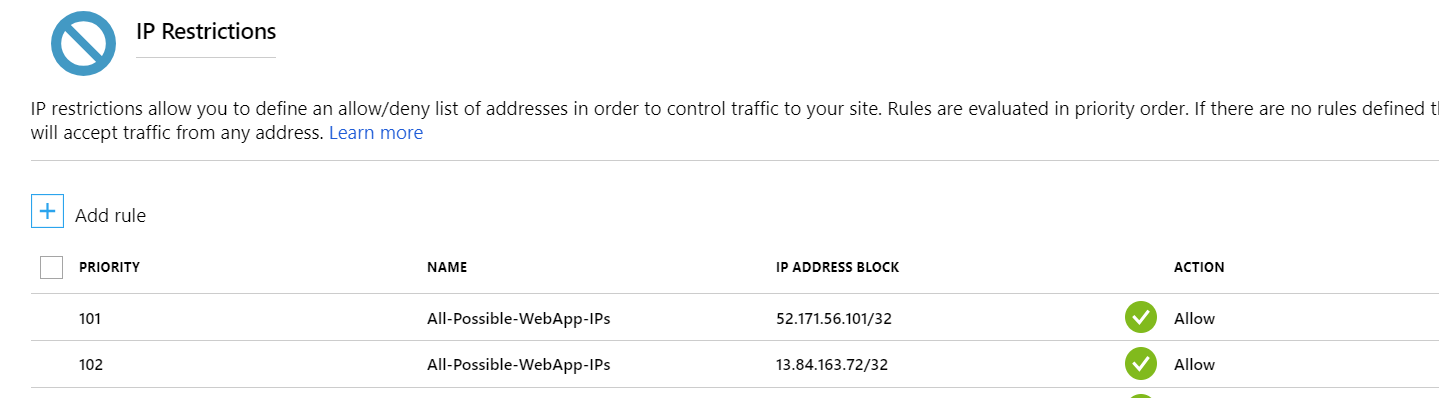
2) Then we decided to change tags (basically any change) for app_service resource via TF. After that rules became broken and we see this:
3) I've tried to add IP Restriction list to Lifecycle->Ignore Changes part of the app_service resource, like this:
lifecycle {
ignore_changes = [
"site_config.0.scm_type",
"site_config.0.ip_restriction"
]
}
But this does not help whenever we change IP restriction rules externally and then apply TF, rules became broken.
4) At the same time, looks like, current implementation of azurerm_app_service resource IP Restriction part is using old Azure API 2016-08-01 instead of 2018-02-01 (https://docs.microsoft.com/en-us/azure/app-service/app-service-ip-restrictions). In old API you need just to specify 2 parameters: ip_address and subnet_mask. But for new API ip_restriction consists of the next parameters:
{
"ipAddress": "131.107.159.0/24",
"action": "Allow",
"tag": "Default",
"priority": 100,
"name": "allowed access"
}
So basically when TF Apply run against app_service resource it is using old API and this just break IP Restriction rules at all.
So I have two questions:
1) How can we ignore changes for IP Restriction rules applied externally?
2) What is the best way to handle such case?
Community Note
- Please vote on this issue by adding a 👍 reaction to the original issue to help the community and maintainers prioritize this request
- Please do not leave "+1" or "me too" comments, they generate extra noise for issue followers and do not help prioritize the request
- If you are interested in working on this issue or have submitted a pull request, please leave a comment
Terraform (and AzureRM Provider) Version
Terraform v0.11.7
- provider.azurerm v1.19.0
- provider.random v2.0.0
- provider.template v1.0.0
Affected Resource(s)
- azurerm_app_service
Terraform Configuration Files
# Copy-paste your Terraform configurations here - for large Terraform configs,
# please use a service like Dropbox and share a link to the ZIP file. For
# security, you can also encrypt the files using our GPG public key: https://keybase.io/hashicorp
Debug Output
Panic Output
Expected Behavior
Actual Behavior
Steps to Reproduce
terraform apply
Important Factoids
References
- #0000
All 16 comments
Up until last week this was a nuisance but today when I logged in to check a azure web app in the portal the iprestrictions blade is broken because of this. The gui fails because of a null reference when trying to apply "tolower" to a property which makes me suspect the name property of the rule. If I use https://resources.azure.com/ to find the ip restriction rule in the app and add a name property to the rule the iprestrictions blade loads normally.
We are experiencing the same issues.
This bug do our use of Terraform terrible. Without possible to add priority and name, our app service, would not work. This bug cause us to must add a manual step, where we must remember config this in portal after apply.
In cases like this we usually use Powershell script.
Has this issue been fixed yet?
@turjachaudhuri, unfortunately no, it has to be fixed in next release (1.23) but it was moved to 1.25 release...
Has this issue been fixed ? in Azure provider 1.25 version ? Or in any later version ? Can somebody let me know.
No it hasn't which is annoying as it would be really useful to label the IP addresses in the portal.
While we wait for this to be updated the following code using azurerm templates can set the IpSecurityRestrictions and scmIpSecurityRestrictions properties on the site config on every terraform apply if added in addition to an existing app service resource deployment.
resource "azurerm_template_deployment" "ipwhitelist" {
name = "${var.application}-ipwhitelist"
resource_group_name = var.resource_group_name
template_body = <<JSON
{
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"variables": {
"_force_terraform_to_always_redeploy": "${timestamp()}"
},
"resources": [{
"type":"Microsoft.Web/sites/config",
"apiVersion":"2018-11-01",
"name":"${azurerm_app_service.app_service.name}/web",
"location":"[resourceGroup().location]",
"properties":{
"IpSecurityRestrictions":[
{
"ipAddress":"${local.some_address_to_allow}",
"action":"Allow",
"tag":"Default",
"priority":300,
"name":"Allow_My_Proxy",
"description":"useful info"
}
],
"scmIpSecurityRestrictions":[
{
"ipAddress":"${local.some_address_to_allow}",
"action":"Allow",
"tag":"Default",
"priority":300,
"name":"Allow_My_Proxy",
"description":"useful info"
}
]
}
}
]
}
JSON
deployment_mode = "Incremental"
}
Is there a way to use ip_restriction with Type as 'Virtual Network' using Terraform?
To add it as VNet restriction you use virtual_network_subnet_id:
ip_restriction {
virtual_network_subnet_id = "${data.azurerm_subnet.app_gateway_subnet.id}"
}
But was there any progress on adding names and priorities?
@JleruOHeP yes, there is just now an open PR for names and priorities :) https://github.com/terraform-providers/terraform-provider-azurerm/pull/6705
I am facing the same issue, was this fixed ?
I'm pretty sure that this now works, other than some issues with changing between ip and subnet.
ip_restriction {
ip_address = 10.0.0.0/8
priority = 1000
name = "InternalAppSubnet"
action = "Allow"
virtual_network_subnet_id = null
subnet_id = null
}
or
ip_restriction {
ip_address = null
priority = 1000
name = "InternalAppSubnet"
action = "Allow"
virtual_network_subnet_id = var.connected_subnet_id
subnet_id = var.connected_subnet_id
}
Note setting both virtual_network_subnet_id and subnet_id to the same value
Hi @martinjt ,
What about working with "Service Tag" Access Restrictions?
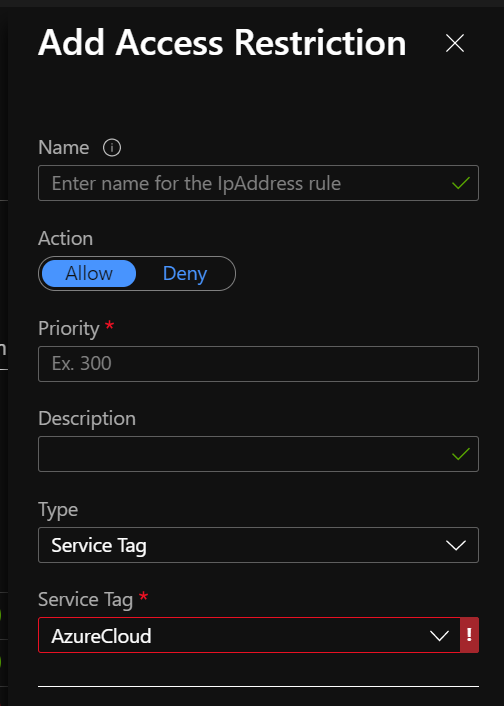
Seems those rules are not supported yet. I'm right?
I've not seen that in the terraform docs.
Most helpful comment
Is there a way to use ip_restriction with Type as 'Virtual Network' using Terraform?