Terraform-provider-aws: Unable to update tags of ECS service with code deploy
Community Note
- Please vote on this issue by adding a 👍 reaction to the original issue to help the community and maintainers prioritize this request
- Please do not leave "+1" or other comments that do not add relevant new information or questions, they generate extra noise for issue followers and do not help prioritize the request
- If you are interested in working on this issue or have submitted a pull request, please leave a comment
Terraform CLI and Terraform AWS Provider Version
- Terraform v0.12.29
- aws provider v2.69.0
Affected Resource(s)
- aws_ecs_service
Terraform Configuration Files
https://gist.github.com/hitsumabushi/404567895e2336e9f6a733a6388249ea#file-main-tf
At first, run terraform apply with this file, and edit local.tags variable, adding tag or delete tag. After that, run terraform apply again.
No changes except for aws ecs service tags.
Debug Output
https://gist.github.com/hitsumabushi/404567895e2336e9f6a733a6388249ea#file-log
(some information masked)
Expected Behavior
succeed to run terraform apply and aws ecs service tags are updated.
Actual Behavior
failed to apply terraform, and terraform outputs following error.
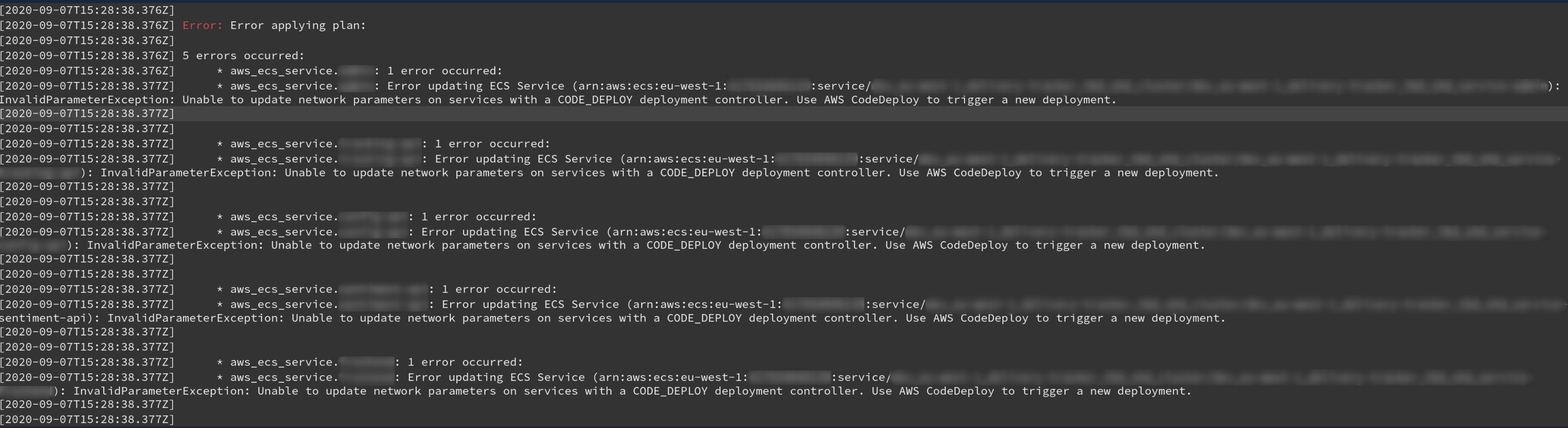
Error: Error updating ECS Service (arn:aws:ecs:us-west-2:XXXXXXXXXXX:service/sample_cluster/ecs-service-terraform-tagging-test): InvalidParameterException: Unable to update network parameters on services with a CODE_DEPLOY deployment controller. Use AWS CodeDeploy to trigger a new deployment.
Steps to Reproduce
terraform apply- edit tags variable
terraform apply
References
- Related to #13658
All 3 comments
I think this is due to the UpdateService API constraints, which is described in this issue, too.
For services using the blue/green (CODE_DEPLOY) deployment controller, only the desired count, deployment configuration, task placement constraints and strategies, and health check grace period can be updated using this API. If the network configuration, platform version, or task definition need to be updated, a new AWS CodeDeploy deployment should be created. For more information, see CreateDeployment in the AWS CodeDeploy API Reference.
No, it is not.
In my case, terraform should not call UpdateService API, because no difference except for tags in plan result.
And, for assigning tags, we use TagResource API.
I think this is a problem related with TypeSet. security_groups, subnets are declared as TypeSet.
TypeSet are includes func values.
- https://github.com/hashicorp/terraform-plugin-sdk/blob/master/helper/schema/set.go#L48
- https://github.com/hashicorp/terraform-plugin-sdk/blob/master/helper/schema/schema.go#L301
And, these values are compared by using reflect.DeepEqual in apply phases.
Func values are deeply equal if both are nil; otherwise they are not deeply equal.
If we change TypeSet to TypeList (TypeList is more simple type than TypeSet), it seems to work well. But, I can't pass acceptance tests.
https://github.com/hitsumabushi/terraform-provider-aws/commit/eb4cc683731fe374053804adadb31c043bcba891
@hitsumabushi I'm facing exactly the same issue using Terraform v0.12.29 and AWS provider v2.70.0, when I try to update tags on a existent resource, something to notice is this issue don't happen if we create new resources only change existent ones, the workaround I'm working on is running the aws-cli in order to change the tags before run Terraform, that way when Terraform look for the diff in the deployed resources against the Terraform code, will identify no changes to apply and later we can remove the workaround.
This workaround proofs one thing, change the tags are possible with no impact or any error from AWS, so I assume this is an error related with the AWS provider, this seems to not handling correctly this particular change.
Most helpful comment
No, it is not.
In my case, terraform should not call UpdateService API, because no difference except for tags in plan result.
And, for assigning tags, we use TagResource API.
I think this is a problem related with TypeSet.
security_groups,subnetsare declared as TypeSet.TypeSet are includes func values.
And, these values are compared by using reflect.DeepEqual in apply phases.
If we change TypeSet to TypeList (TypeList is more simple type than TypeSet), it seems to work well. But, I can't pass acceptance tests.
https://github.com/hitsumabushi/terraform-provider-aws/commit/eb4cc683731fe374053804adadb31c043bcba891