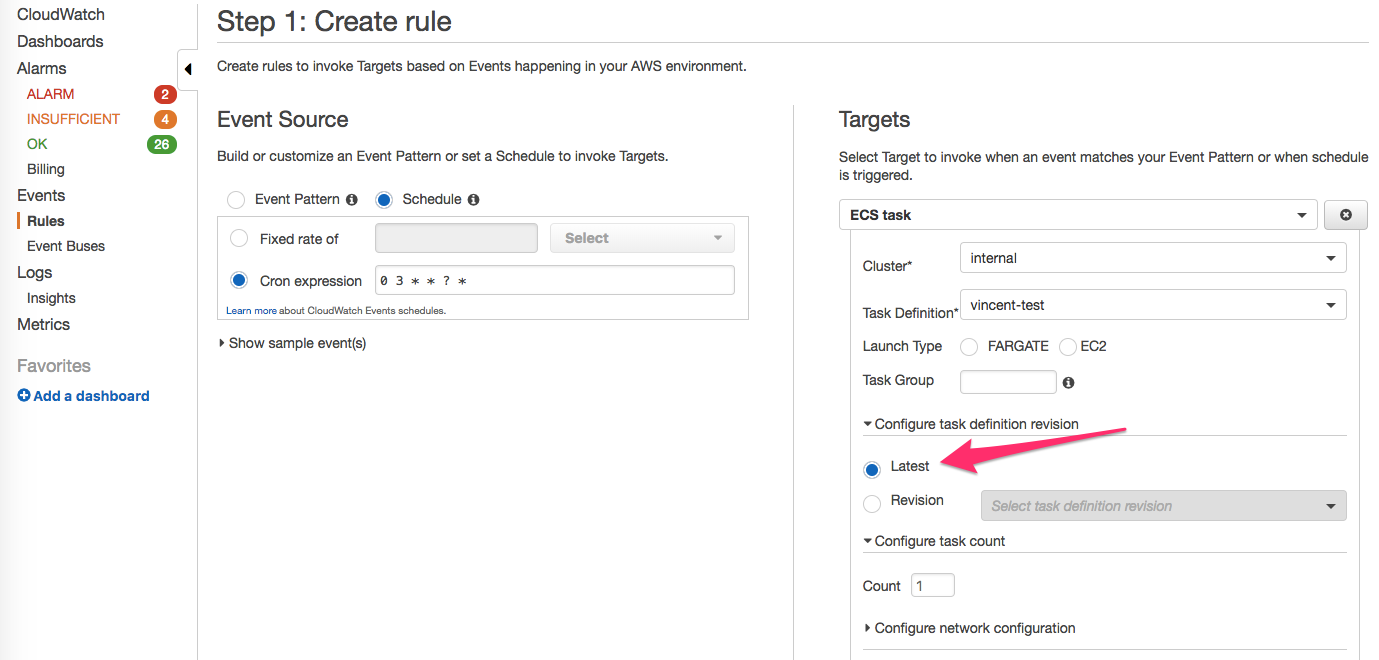
Terraform-provider-aws: Missing latest task definition revision in events target option for aws_cloudwatch_event_target
Found in AWS console. Seems it may help getting the latest revision automatically. Cannot see any config in https://www.terraform.io/docs/providers/aws/r/cloudwatch_event_target.html#ecs_target
Guess it is missing, right?
All 9 comments
@vincentkwok does it work if you leave off the revision in the task_definition_arn? The CloudWatch Events API Reference doesn't note it specifically, but if its like the ECS CreateService API then:
taskDefinition
The family and revision (family:revision) or full ARN of the task definition to run in your service. If a revision is not specified, the latest ACTIVE revision is used.
Thanks. Found the key point is in ecs_target task_definition_arn option.
My workaround
resource "aws_caller_identity" "current" {}
locals {
task_definition_arn_only = "arn:aws:ecs:${var.aws_region}:${data.aws_caller_identity.current.account_id}:task-definition/${aws_ecs_task_definition.ecs_cron_task_definition.family}" // no revision
}
resource "aws_cloudwatch_event_target" "cron_target" {
rule = "${aws_cloudwatch_event_rule.cron_rule.name}"
arn = "${aws_ecs_cluster.ecs_app.arn}"
ecs_target {
/* Not work, since aws_ecs_task_definition.arn consists of revision
task_definition_arn = "${aws_ecs_task_definition.ecs_cron_task_definition.arn}"
*/
task_definition_arn = "${local.task_definition_arn_only}"
task_count = 1
}
role_arn = "${aws_iam_role.ecs_events_role.arn}"
}
Suggestion: it would be helpful if resource aws_ecs_task_definition has an arn attribute without revision.
I think this issue may close now.
Any update on this issue ?
@vincentkwok I tried you solution but I have FailedInvocations since the update with task definition without revision. Have you got some feedback ?
No such problem for me.
Does the resource apply properly? i.e. the console configuration like this
@vincentkwok Yes the resource apply properly but with this modification all invocations are in failed status
the latest ACTIVE revision is used.
Probably this will be the latest in the timing you applied.
Now we need to run terraform apply each time the task definition is updated.
@Orkin I also failed to invocation if without revision.
But that was the problem with the CloudWatch Events IAM role for target.
"Resource": [
"arn:aws:ecs:${var.region}:${var.account_id}:task-definition/task_name:*"
]
I solved this when I removed :* from the end of the Resource ARN in role policy.
@orfx True story.
@Orkin Also, need to ensure iam:PassRole https://docs.aws.amazon.com/AmazonECS/latest/developerguide/CWE_IAM_role.html
// Slightly modify the IAM created in aws console cloudwatch event
data "aws_iam_policy_document" "ecs_events_role_policy_document" {
statement {
effect = "Allow"
actions = [
"ecs:RunTask"
]
resources = [
"${local.cron_task_definition_arn}", // !!! Do NOT add :* or cron cannot use latest task definition
"${local.cron_task_definition_arn}:*" // Not useful as this moment. Just to allow any revision, if really need for some cases
]
condition {
test = "ArnLike"
variable = "ecs:cluster"
values = ["${aws_ecs_cluster.ecs_app.arn}"]
}
}
statement {
effect = "Allow"
actions = [
"iam:PassRole"
]
resources = ["*"]
condition {
test = "StringLike"
variable = "iam:PassedToService"
values = ["ecs-tasks.amazonaws.com"]
}
}
}
For whom it may concern. This:
resource "aws_caller_identity" "current" {}
locals {
task_definition_arn_only = "arn:aws:ecs:${var.aws_region}:${data.aws_caller_identity.current.account_id}:task-definition/${aws_ecs_task_definition.ecs_cron_task_definition.family}" // no revision
}
can be made simpler:
locals {
task_definition_arn_only = replace(aws_ecs_task_definition.ecs_cron_task_definition.arn, "/:\\d+$/", "")
}
Most helpful comment
@Orkin I also failed to invocation if without revision.
But that was the problem with the CloudWatch Events IAM role for target.
I solved this when I removed
:*from the end of the Resource ARN in role policy.