Terraform-provider-aws: Error output hiding underlying problem for aws_iam_role
Getting Resource 'aws_iam_role.main' not found for variable 'aws_iam_role.main.id' for an underlying error that would be more helpful if exposed:
2017/09/18 08:56:35 [ERROR] root.app_service.service.autoscaling.autoscaling_policy: eval: *terraform.EvalValidateResource, err: Warnings: []. Errors: ["name" cannot be longer than 64 characters]
2017/09/18 08:56:35 [ERROR] root.app_service.service.autoscaling.autoscaling_policy: eval: *terraform.EvalSequence, err: Warnings: []. Errors: ["name" cannot be longer than 64 characters]
2017/09/18 08:56:35 [WARN] Output interpolation "role_arn" failed: Resource 'aws_iam_role.main' not found for variable 'aws_iam_role.main.arn'
app_service.module.service.module.autoscaling.aws_appautoscaling_target.main"
2017/09/18 08:56:35 [ERROR] root.app_service.service.autoscaling.autoscaling_policy: eval: *terraform.EvalInterpolate, err: Resource 'aws_iam_role.main' not found for variable 'aws_iam_role.main.id'
2017/09/18 08:56:35 [ERROR] root.app_service.service.autoscaling.autoscaling_policy: eval: *terraform.EvalSequence, err: Resource 'aws_iam_role.main' not found for variable 'aws_iam_role.main.id'
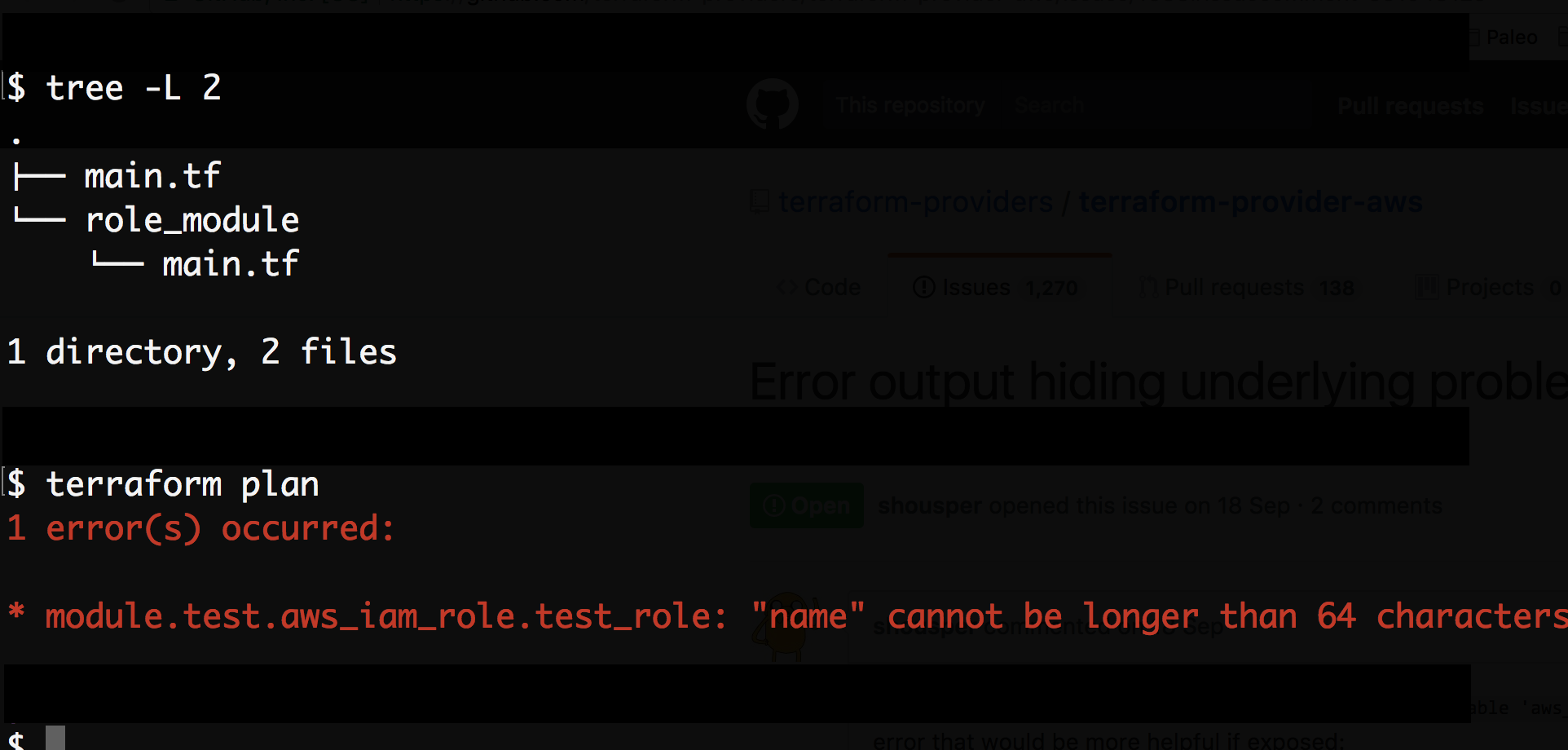
From the log, there is a "name" cannot be longer than 64 characters error that would be great to see in the CLI output. Instead we just get:
Error running plan: 1 error(s) occurred:
* module.app_service.module.service.module.autoscaling.module.autoscaling_policy.aws_iam_role_policy.main: 1 error(s) occurred:
* module.app_service.module.service.module.autoscaling.module.autoscaling_policy.aws_iam_role_policy.main: Resource 'aws_iam_role.main' not found for variable 'aws_iam_role.main.id'
Terraform Version
v0.10.4
Affected Resource(s)
Not sure if there are others, but:
- aws_iam_role
All 10 comments
Hi @shousper
Thanks for reporting this. Just checked with
resource "aws_iam_role" "test_role" {
name = "test_roletest_roletest_roletest_roletest_roletest_roletest_roleee"
assume_role_policy = <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Action": "sts:AssumeRole",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Effect": "Allow",
"Sid": ""
}
]
}
EOF
}
output "role_id" {
value = "${aws_iam_role.test_role.id}"
}
and a terraform plan outputs:
$ terraform plan
1 error(s) occurred:
* aws_iam_role.test_role: "name" cannot be longer than 64 characters
which is the expected behaviour. Can you provide your configuration so that we can replicate this?
Thanks!
Hi @Ninir,
I'd say the problem relies on the policy resource being separate and depending on the role with a long name and possibly the resources living inside a module. Not sure if it's the module thing or just the separate role policy resource. Can you give this a shot?
role_module/main.tf
resource "aws_iam_role" "test_role" {
name = "test_roletest_roletest_roletest_roletest_roletest_roletest_roleee"
assume_role_policy = <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Action": "sts:AssumeRole",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Effect": "Allow",
"Sid": ""
}
]
}
EOF
}
resource "aws_iam_role_policy" "test_role" {
name = "test_role_policy"
role = "${aws_iam_role.test_role.id}"
policy = <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ecs:DescribeServices",
"ecs:UpdateService"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"cloudwatch:DescribeAlarms"
],
"Resource": "*"
}
]
}
EOF
}
output "role_id" {
value = "${aws_iam_role.test_role.id}"
}
main.tf
module "test" {
source = "./role_module"
}
Cheers.
Hi @shousper
Sorry for taking so long to get back to you.
So I just checked with Terraform 0.10.X and the AWS Provider 1.3.0, and here is the result:
Can you try upgrading both Terraform (to 0.10.8 first) and the AWS Provider (to 1.1.0 or 1.3.0)?
Thanks!
Hi @Ninir
No worries, thanks for following up all the same.
I've confirmed the same with Terraform 0.10.8 and AWS Provider 1.3.1: ✅ Works exactly per your screenshot. Likewise for Terraform 0.11.0.
Looks solved to me. Thanks again!
Cheers.
@shousper I'm seeing this issue in with Terraform 0.11.7 and AWS provider 1.14.1. Regression?
I'm seeing the same apparent regression, using an aws_iam_policy_document data source:
Terraform v0.11.7
AWS Provider v1.14.1
data "aws_iam_policy_document" "batch_service_role_policy" {
statement {
sid = "1"
actions = [
"sts:AssumeRole",
]
principals = {
type = "Service"
identifiers = ["batch.amazonaws.com"]
}
}
}
resource "aws_iam_role" "aws_batch_service_role" {
name = "${var.service_role_name}"
assume_role_policy = "${data.aws_iam_policy_document.batch_service_role_policy.json}"
}
Happening to me too. Taken me days to even find this thread!
Terraform v0.11.7
- provider.aws v1.22.0
@Ninir I'm gonna reopen this one based on the comments.
Hi folks! 👋 Sorry for the unexpected behavior here.
For the original issue (Resource ... not found for variable when it should be returning a validation error), it turns out this is likely an issue upstream in Terraform core, rather than anything to do with the AWS provider specifically. This scenario basically occurs anytime we implement a resource attribute with a ValidateFunc and then that resource is then referenced by another resource. Terraform core, when the first resource is failing that validation, is preferring to return the invalid resource reference message instead of the resource validation error.
We have a few upstream tracking issues relating to this:
- https://github.com/hashicorp/terraform/issues/18129
- https://github.com/hashicorp/terraform/issues/16332
- https://github.com/hashicorp/terraform/issues/14333
I would suggest commenting on and upvoting those for the latest updates on this. 👍
For the folks running into unexpected behavior with the aws_iam_policy_document data source, I would suggest opening a new issue filling in the issue template details so we can properly troubleshoot what is happening in your scenario.
I'm going to lock this issue because it has been closed for _30 days_ ⏳. This helps our maintainers find and focus on the active issues.
If you feel this issue should be reopened, we encourage creating a new issue linking back to this one for added context. Thanks!
Most helpful comment
@shousper I'm seeing this issue in with Terraform 0.11.7 and AWS provider 1.14.1. Regression?