Terminal: add Azure Tenant ID for Cloud Shell
In my org, we cannot log into Azure without specifying the tenant id. I don't know how that is being done or why it's the case, but even for Powershell, I have to pass the tenant ID for "connect-azaccount" for it to work.
I get this error when opening the Cloud Shell in Terminal (and the same when I try to use powershell without the tenant):
AADSTS500021: Access to 'Microsoft Services' tenant is denied.
Trace ID: 7856d209-60c6-484b-bb16-4cca8f436f00
Correlation ID: 0175f86a-10f3-4983-826c-dd0d42c9efd5
Timestamp: 2020-11-18 16:51:42Z
[process exited with code 1]
Is there some way in the config file that I can set the tenant that I want to connect to? I see info that you can usually pick your tenant after signing in, and then storing it somehow. I just don't know how that gets stored or if I can maybe bypass that method and just create the connection files myself?
All 12 comments
Hi, thank you for reporting this!
I'd like some clarification on your issue:
- Could you send a screenshot of your terminal window showing what happens after you go through the device authentication? (that's the procedure where you need to open up a browser and input a code to authenticate)
- Are you able to use the Cloud Shell at https://shell.azure.com/?
I'm gonna close this one out as a /dupe of #5311. Not because I think that it's the same _request_, but because I think they have the same solution.
5311 proposes that we allow the you to put the tenant ID in your settings file :smile: which would also help with this.
I'll put the -Bug tag on that one as well.
Hi! We've identified this issue as a duplicate of another one that already exists on this Issue Tracker. This specific instance is being closed in favor of tracking the concern over on the referenced thread. Thanks for your report!
@DHowett - I am not convinced that the problem in this case is with tenant ID. The error here is a generic AAD authentication failure. It might happen in AzConnect because of the restrictions on the default tenant. However we don't try to connect to a default tenant in terminal (unless I missed - need to review), instead we present a tenant selection, which didn't occur in this case.
I think it is worthy to see the screen capture to be sure in which stage it happened.
I guess we cannot file a support case to AAD on the tenant's behalf, which is quite annoying, but probably if @chlsmith submits a feedback with a tenant id included we can somehow try to check the correlation id with AAD folks in CSS (unless the tenant is not premier and we are screwed)
Screen shot of the error is attached. I think we have some kind of conditional access configured on our outbound proxy that stops us from being able to hit that auth tenant. But if we could set the tenant in the json, that probably would fix it.
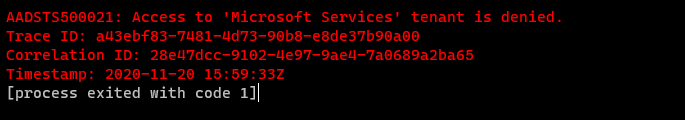
@chlsmith - is this the only text you have in terminal when opening the shell? Even before you get a device code challenge?
Conditional access is the feature of AAD, rather than of outbound proxy. The message you get is an authentication failure response from AAD which means that it wasn't blocked by the proxy.
Correct. I never get the prompt for device code challenge. The same thing happens when I try "connect-azaccount" in powershell without passing the tenant.
This is both interesting and weird. I am definitely missing something:
- If no prompt was shown in the terminal, it means that there were neither challenge nor refresh of stored tokens
- Yet we get a failure from AAD
- The only message we could send to AAD is a post to
https://login.microsoftonline.com/common/oauth2/devicecode - However this post is not even associated with specific organization yet, so no policy can block it on AAD side
- And since we got a message from AAD it means that we were not blocked by some proxy.
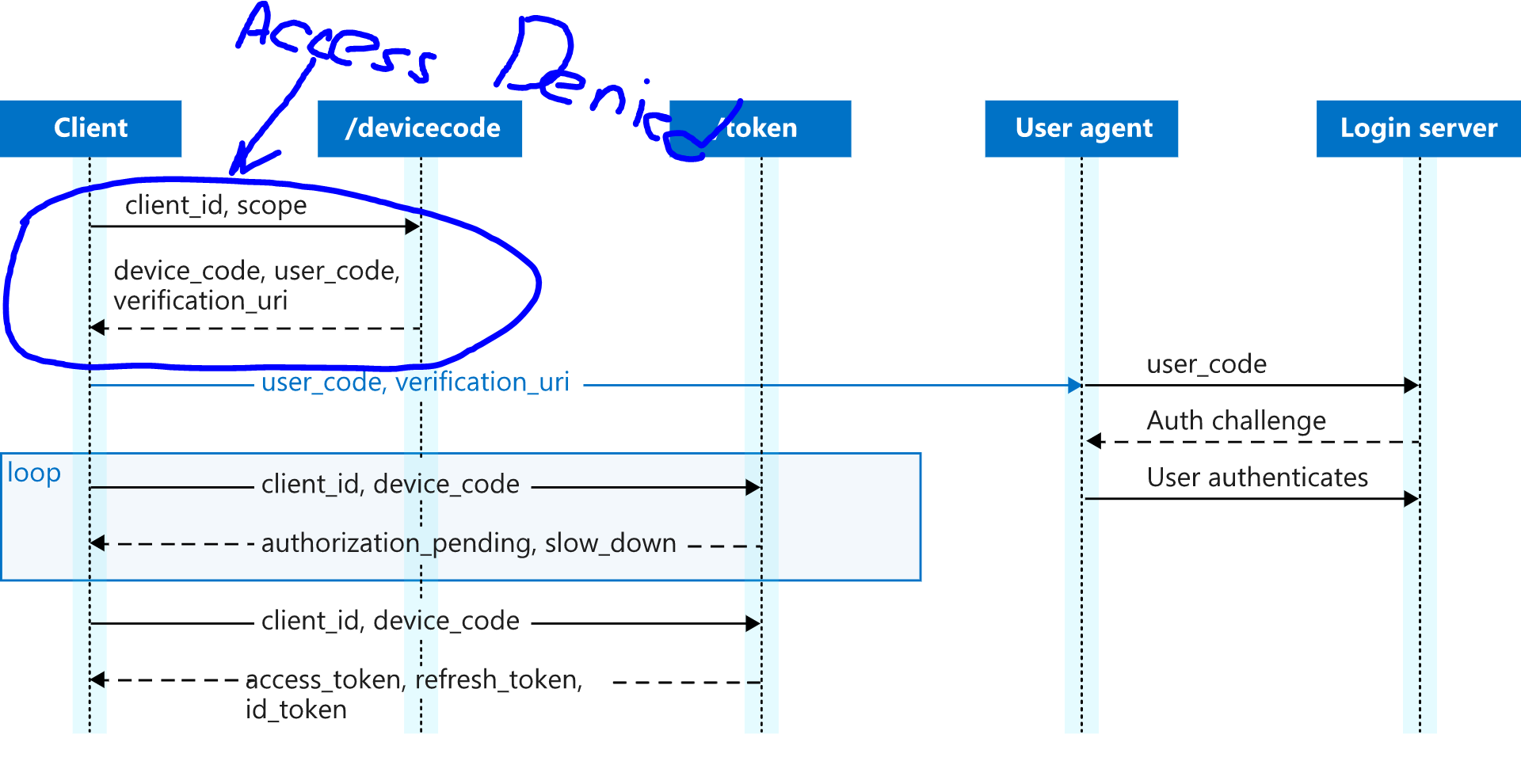
So what causes this request that is not associated to org to fail?
I wish I could capture more info from the communication but I don't have anything on this locked-down laptop. Is there an endpoint I could try to hit with Chrome instead so I could see it with Developer Tools?
Wondering if you have an ssl terminating proxy that alters something.
Can you please browse to login.microsoftonline.com in incognito browser and show how the certificate looks like? Like this:
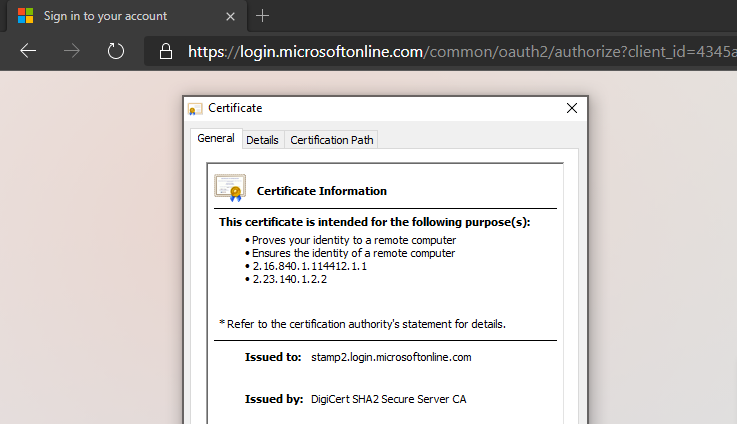
Yep, there ya go. Yes, my corporate ZScaler is the "Issued By".
Now I see. I didn't assume that your proxy intercepts SSL, especially on AAD domains .
So you are right, we need to make the login domain configurable.
@DHowett - not sure how to do it because of azconnection bridge. But it is worth checking as it is also a blocker for gov clouds.