Rocket.chat: Info Page Small Security Issue
Description:
Non-admin users can see some server info and I think we need remove this.
Steps to reproduce:
- Create non-admin user
- Go to an admin url like http://localhost:3000/admin/Layout then you automatically redirect to: http://localhost:3000/admin/info
- Click on
info, now you can see some info about server like RC version. If a hacker know this info can use known issues to attack to the RC instance.
Expected behavior:
Prevent access to */admin at all for non-admin users.
Actual behavior:
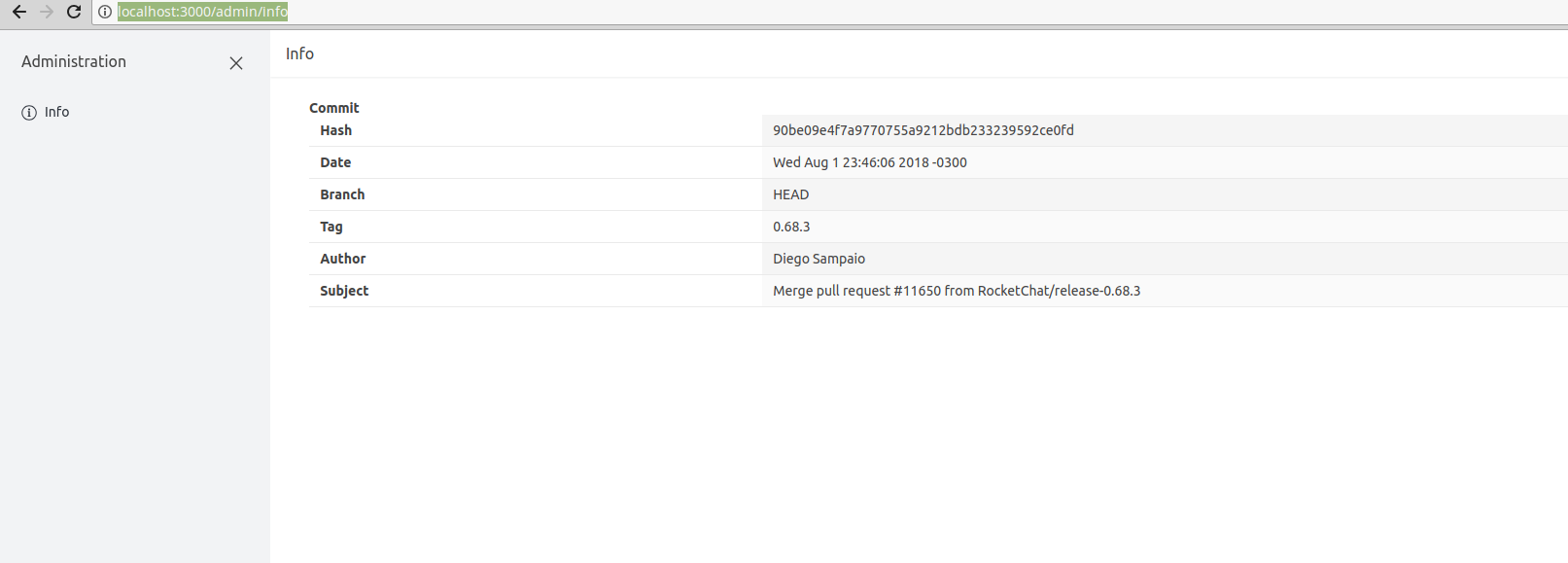
Server Setup Information:
- Version of Rocket.Chat Server: 0.68.3
- Operating System: Linux
- Deployment Method: docker (based on this)
- Number of Running Instances: 1
- DB Replicaset Oplog: true
- NodeJS Version: like official docker image
- MongoDB Version: 3.2
Additional context
Relevant logs:
All 12 comments
I can reproduce the Issue on my Rocketchat 0.68.3 Source/Tar instance. It's just a small information disclosure but could be fixed.
Any news about this?
This practically only exposes the version of Rocket.Chat Server running ー accessible through /api/v1/info anyway.
I agree with @vynmera I will put this bug on my list, but its not so important I think.
@vynmera , @ggazzo Yes I agree that it's not so critical (If it' critical I reported this by email) but it's useful for hackers because RC is a open source project and anyone can see each version bugs and known issue.
If some RC instance not be up-to-date hackers can start attacking by find RC version and use know bugs for attack RC instance.
It's also important because some people want to use RC as a communication channel for Cryptocurrency Communities (#8284)
So I think it's better to fix this in next release.
@mnlbox Android and iOS apps uses these informations too. There is no way to hide them, at least in API.
@piotrkochan :thinking:
How we can get RC server version from Android or iOS app?
By http request: https://your-server/api/v1/info
@piotrkochan So maybe we need also some changes there. :thinking:
Thanks for this note.
Probably could require auth for the api info.
The mobile apps should be able to auth and then grab the version if needed. It would be nice to be able to hide any Rocket.Chat versioning from the public eye without being authed.
Is there any legitimate or functional reason why a non authenticated user needs to see the version info? This is a good tool for attackers as found vulnerabilities are not disclosed to RocketChat users and people run vulnerable versions without knowing the danger.
https://github.com/RocketChat/Rocket.Chat/issues/10795
https://github.com/RocketChat/Rocket.Chat/pull/14160
Logged in regular users can also see the list of all existing invites. This exposes private groups using invites to all users.
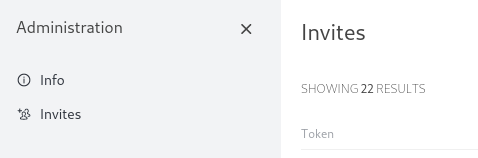
Edit and correction:
Luckily there was more involved in this. Above issue required that the user had a custom role that had create-invite-links permission assigned to it. Normally only the roles admin, moderator and owner have this permission. Moderator and owner are specific to certain channels alone, and don't seem to give the privilege to the users.
When applied to a custom role, the permission behaves like it does for the admin role, and exposes invites via /admin/ path.
This behaviour is likely to be by design. Invite links are not exposed unless admin confuses the create-invite-links permission with regular user privileges.
Most helpful comment
This practically only exposes the version of Rocket.Chat Server running ー accessible through
/api/v1/infoanyway.