Parity-ethereum: --jsonrpc-cors parameters
I'm running:
>
- Which Parity version? Parity 1.8.5-beta and following
- Which operating system?: Linux
- How installed?: dpkg
- Are you fully synchronized?: not applicable
- Which network are you connected to?: kovan
- Did you try to restart the node?: yes
Prior to version 1.8.5-beta I was able to run a remote parity node, behind an nginx proxy, which accepts connections to the RPC server from a group of allowed domains.
RPC origins config variable was configured correctly to receive connections from a number of different domains. Apparently such variable is no longer supported on version 1.8.5-beta and following.
The release note states as follows:
Note: The default value of
--jsonrpc-corsoption has been altered to disallow (potentially malicious) websites from accessing the low-sensitivity RPCs (viewing exposed accounts, proposing transactions for signing). Currently domains need to be whitelisted manually. To bring back previous behaviour run with--jsonrpc-corsall or--jsonrpc-cors http://example.com.
1) I have tried to run --jsonrpc-cors all with no results.
2) I have tried to run --jsonrpc-cors URL with no results. Additionally, it seems that --jsonrpc-cors takes only strings, so no way to set a group of URLs.
3) I am unable to understand how to whitelist domains manually.
Please kindly advise.
All 12 comments
Tried again to run it with --jsonrpc-cors all with no results.
My Parity UI is on https://srv03.endpoint.network so I've also tried --jsonrpc-cors https://srv03.endpoint.network but it's not working. I can see from nginx log that the RPC requests are proxied to Parity with origins https://srv03.endpoint.network so everything seems alright.
I've also tried to set the the parameters in Parity config file with:
cors = "https://srv03.endpoint.network"
or
cors = "all"
I've also found this old issue which says that cors takes a comma separated list of URLs:
https://github.com/paritytech/parity/issues/5373
But even cors = "https://srv03.endpoint.network,all" does not work.
Here is the request response:
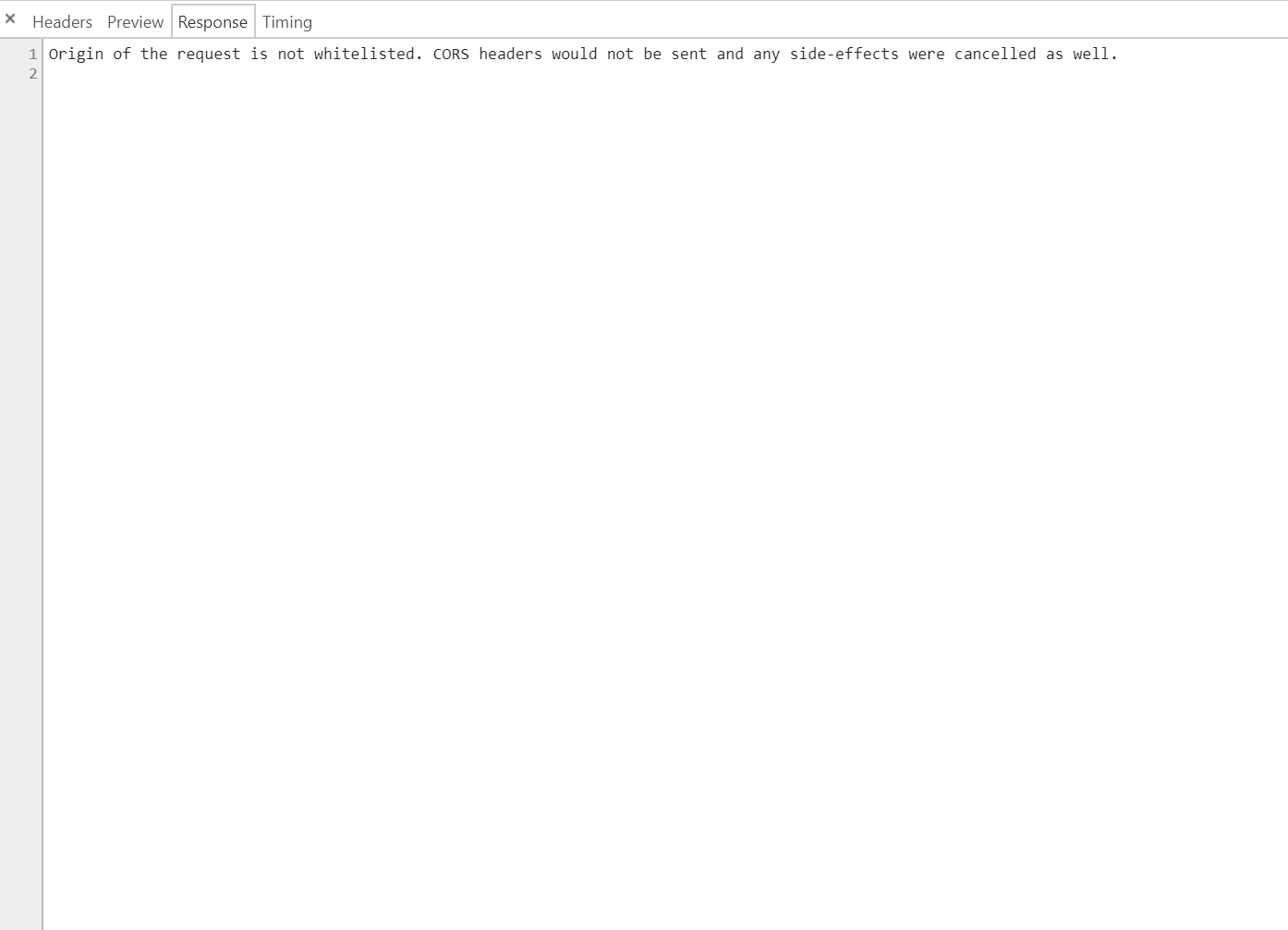
Origin of the request is not whitelisted. CORS headers would not be sent and any side-effects were cancelled as well.
cc @tomusdrw
@wnz99 can you please post a full list of CLI arguments (or config file) you are using on the node?
Also what ports are you trying to access? Is https://srv03.endpoint.network proxying to http://localhost:8180?
Could you also open Chrome Dev Tools on the "Network" tab, refresh the UI and post a screenshot here?
@tomusdrw sure.
This is the configuration which works with Parity/v1.8.4-beta-c74c8c1-20171211/x86_64-linux-gnu/rustc1.22.1:
[parity]
chain = "kovan"
base_path = "/home/rigoblock/.parity"
keys_path = "/home/rigoblock/cluster/parity-config/keys-dev"
[network]
min_peers = 50
max_peers = 250
snapshot_peers = 25
[dapps]
path = "/home/rigoblock/cluster/parity-config/dapps"
[ui]
interface = "127.0.0.1"
path = "/home/rigoblock/cluster/parity-config/signer"
hosts = ["all"]
[rpc]
interface = "127.0.0.1"
origins = ["chrome-extension://*", "https://srv03.endpoint.network"]
apis = ["web3", "eth", "net", "parity", "traces", "rpc", "secretstore", "pubsub"]
[websockets]
interface = "127.0.0.1"
origins = ["chrome-extension://*", "https://srv03.endpoint.network", "https://srv03.endpoint.network:8545"]
hosts = ["all"]
apis = ["web3", "eth", "net", "parity", "traces", "rpc", "secretstore", "pubsub"]
[misc]
log_file = "/home/rigoblock/logs/parity.log"
This is the conf for Parity/v1.8.6-beta-2d051e4-20180109/x86_64-linux-gnu/rustc1.22.1:
[parity]
chain = "kovan"
base_path = "/home/rigoblock/.parity"
keys_path = "/home/rigoblock/cluster/parity-config/keys-dev"
[network]
min_peers = 50
max_peers = 250
snapshot_peers = 25
[dapps]
path = "/home/rigoblock/cluster/parity-config/dapps"
[ui]
interface = "127.0.0.1"
path = "/home/rigoblock/cluster/parity-config/signer"
hosts = ["all"]
[rpc]
interface = "127.0.0.1"
cors= "all, https://srv03.endpoint.network"
apis = ["web3", "eth", "net", "parity", "traces", "rpc", "secretstore", "pubsub"]
[websockets]
interface = "127.0.0.1"
origins = ["chrome-extension://*", "https://srv03.endpoint.network", "https://srv03.endpoint.network:8545"]
hosts = ["all"]
apis = ["web3", "eth", "net", "parity", "traces", "rpc", "secretstore", "pubsub"]
[misc]
log_file = "/home/rigoblock/logs/parity.log"
Requests are proxied with openresty. Here are the relevant config sections for UI and RPC servers:
server {
#RPC SERVER
listen 139.162.238.183:8545;
server_name srv03.endpoint.network;
# Logging
access_log /home/rigoblock/openresty/logs/rpc-access.log kovan;
error_log /home/rigoblock/openresty/logs/rpc-error.log;
# SSL Server
ssl on;
ssl_certificate /etc/nginx/ssl/endpoint.network/ssl-bundle.crt;
ssl_certificate_key /etc/nginx/ssl/endpoint.network/star.endpoint.network.key;
ssl_prefer_server_ciphers on;
more_set_headers "Content-Security-Policy: connect-src http: https: ws: wss:;frame-src 'self' http: https:;child-src 'self' http: https:;img-src 'self' 'unsafe-inline' data: blob: http: https:;style-src 'self' 'unsafe-inline' data: blob: https:;font-src 'self' data: https:;script-src 'self' 'unsafe-inline' 'unsafe-eval';worker-src 'self' 'unsafe-inline' 'unsafe-eval' blob: ;default-src 'self';sandbox allow-same-origin allow-forms allow-modals allow-popups allow-presentation allow-scripts;form-action 'none';block-all-mixed-content;frame-ancestors 127.0.0.1:8180 *.web3.site:8180 home.web3.site localhost:8180 rigo.network:8180 rigo.network:443 rigo.network kovan.endpoint.network:443 kovan.endpoint.network kovan03.endpoint.network:443 kovan03.endpoint.network srv03.endpoint.network srv03.endpoint.network:3000 appdev.endpoint.network appdev.endpoint.network:443";
more_set_headers "Access-Control-Allow-Origin: *"
more_set_headers "Access-Control-Allow-Headers: Origin, X-Requested-With, Content-Type, Accept"
more_set_headers "Server: srv03.endpoint.network";
location / {
#AUTH
auth_basic off;
sub_filter "127.0.0.1" srv03.endpoint.network;
sub_filter_once off;
sub_filter_types *;
set $jsonrpc_blacklist '';
access_by_lua_file '/home/rigoblock/openresty/conf/conf.d/eth-jsonrpc-access.lua';
proxy_pass http://127.0.0.1:8545;
}
}
server {
listen 139.162.238.183:443;
server_name srv03.endpoint.network;
# Logging
access_log /home/rigoblock/openresty/logs/ui-access.log kovan;
error_log /home/rigoblock/openresty/logs/ui-error.log;
# SSL Server
ssl on;
ssl_certificate /etc/nginx/ssl/endpoint.network/ssl-bundle.crt;
ssl_certificate_key /etc/nginx/ssl/endpoint.network/star.endpoint.network.key;
ssl_prefer_server_ciphers on;
more_set_headers "Access-Control-Allow-Origin: *"
more_set_headers "Access-Control-Allow-Headers: Origin, X-Requested-With, Content-Type, Accept"
more_set_headers "Content-Security-Policy: connect-src http: https: ws: wss:;frame-src 'self' http: https:;child-src 'self' http: https:;img-src 'self' 'unsafe-inline' data: blob: http: https:;style-src 'self' 'unsafe-inline' data: blob: https:;font-src 'self' data: https:;script-src 'self' 'unsafe-inline' 'unsafe-eval';worker-src 'self' 'unsafe-inline' 'unsafe-eval' blob: ;default-src 'self';sandbox allow-same-origin allow-forms allow-modals allow-popups allow-presentation allow-scripts;form-action 'none';block-all-mixed-content;frame-ancestors 127.0.0.1:8180 *.web3.site:8180 home.web3.site localhost:8180 rigo.network:8180 rigo.network:443 rigo.network kovan.endpoint.network:443 kovan.endpoint.network kovan03.endpoint.network:443 kovan03.endpoint.network srv03.endpoint.network srv03.endpoint.network:443 srv03.endpoint.network:3000 appdev.endpoint.network appdev.endpoint.network:443";
more_set_headers "Server: srv03.endpoint.network";
location /rpc {
#AUTH
auth_basic off;
sub_filter "127.0.0.1" srv03.endpoint.network;
sub_filter_once off;
sub_filter_types *;
proxy_pass http://127.0.0.1:8180;
access_log /home/rigoblock/openresty/logs/api_logging.log upstream_logging;
}
location /api {
#AUTH
auth_basic off;
sub_filter "127.0.0.1" srv03.endpoint.network;
sub_filter_once off;
sub_filter_types *;
proxy_pass http://127.0.0.1:8180;
}
location / {
#AUTH
auth_basic "Please enter username and password";
auth_basic_user_file /home/rigoblock/openresty/conf/.htpasswd;
sub_filter "127.0.0.1" srv03.endpoint.network;
sub_filter_once off;
sub_filter_types *;
proxy_pass http://127.0.0.1:8180;
}
Dev console screenshot:
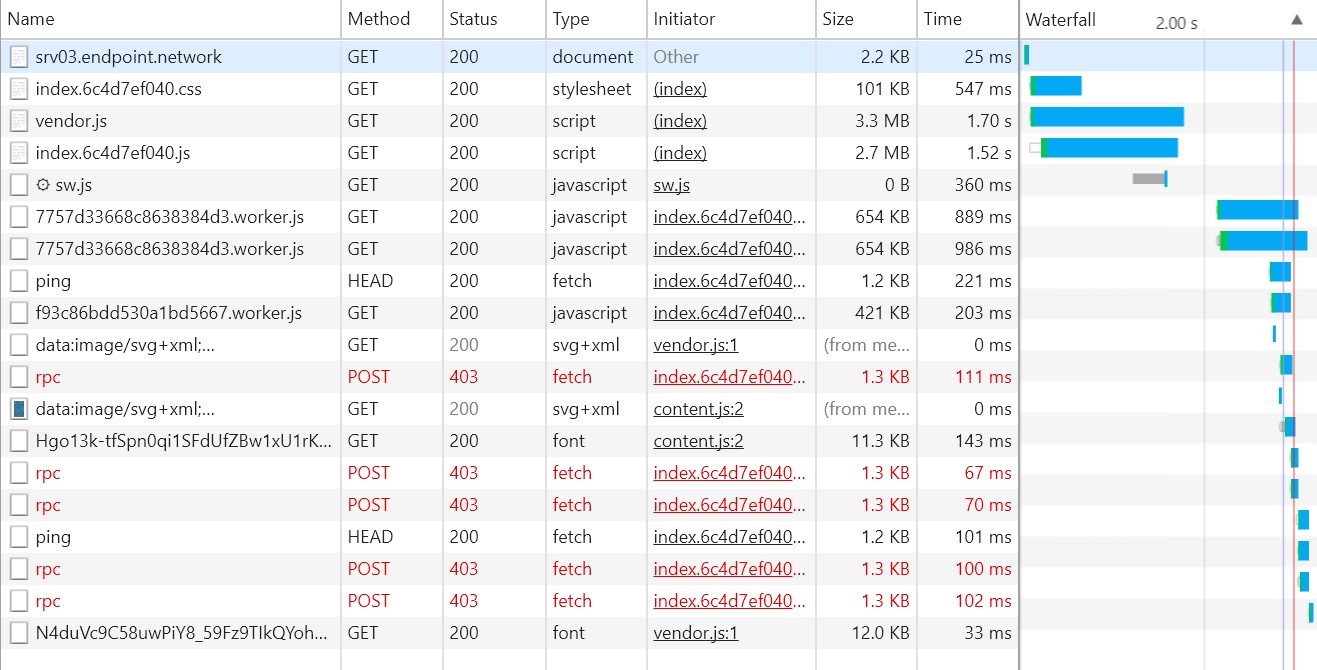
I have also tried to pass --jsonrpc-cors all via command line with no results. Everything works fine with Parity/v1.8.4-beta-c74c8c1-20171211/x86_64-linux-gnu/rustc1.22.1.
@wnz99 Can you show the details of first failed POST rpc? Seems that the response is just 403, so it's not a CORS issue at all.
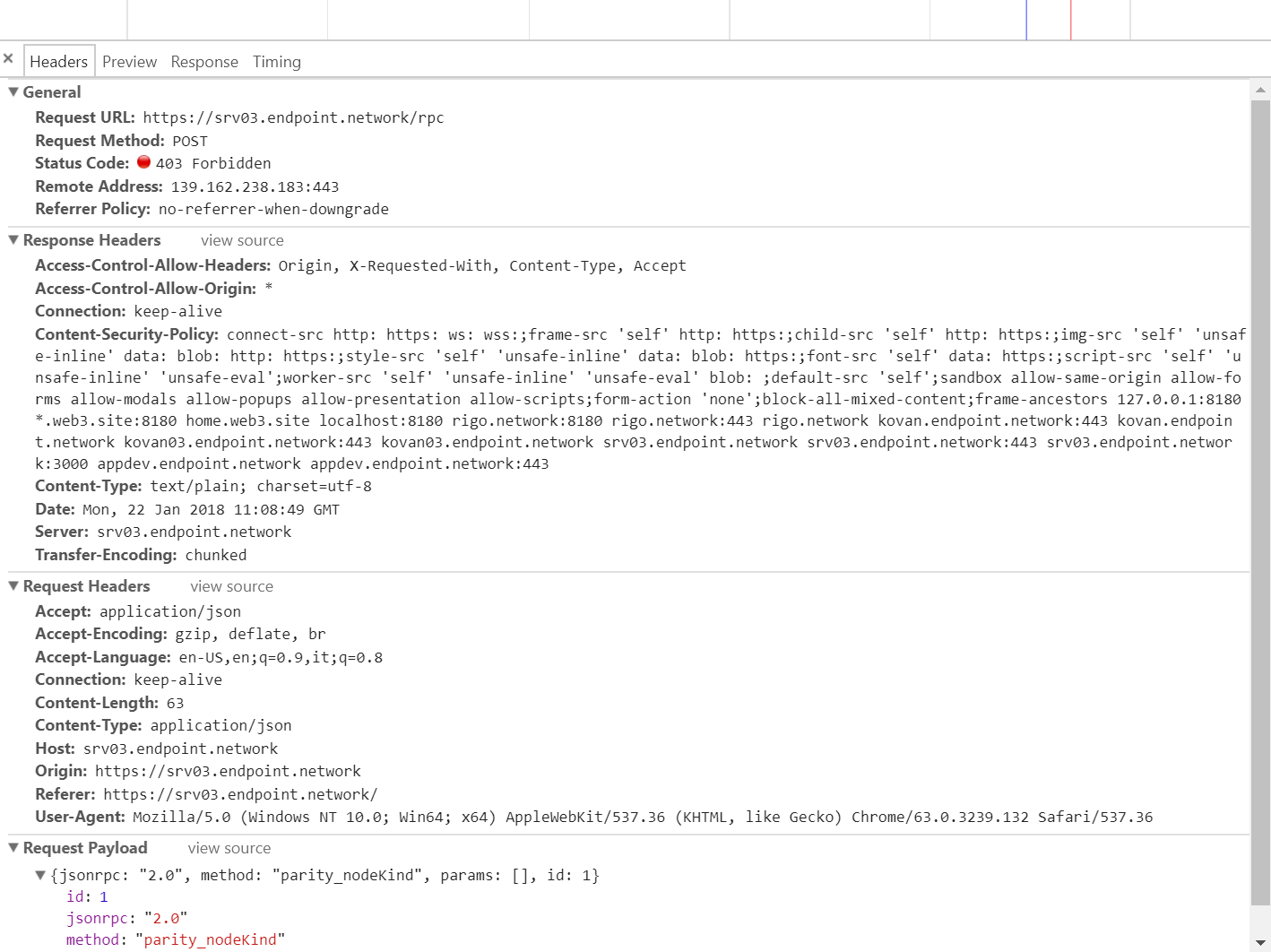
@tomusdrw
Here's the headers and response:
@tomusdrw were you able to reproduce this issue? It's quite blocking for us. We are setting up our own cluster of Parity clients and are not able to upgrade to the latest releases.
Sorry lost a notification for that one somehow.
Could you please run with -lhyper=trace? We need to figure out what headers exactly reach your client.
Are you passing the CORS parameter via command line or a config file?
Also seems that /rpc is actually routed to :8180. That port is not affected by --jsonrpc-cors=all (actually it doesn't send cors headers at all), it should go to 8545 instead.
@tomusdrw it was the port, thank you. I cannot remember why I had that in the conf and not sure why it had been working so far. I will carry out a few more tests in the following days just to make sure everything is alright.
Last question, is there any specific reasons why the config parameters cors takes a string, while origins (and others) takes an array? It can be confusing.
@wnz99 I believe it should be fixed in latest versions of Parity: https://github.com/paritytech/parity/commit/26e4fc68#diff-54d6bbd5addb7a0d39c647e4e33e6990R1055
Same here. I have parity behind nginx.
startup confing
parity daemon /dev/shm/parity.pid --log-file /var/log/parity.log --jsonrpc-apis "all" --jsonrpc-cors "'*'" --jsonrpc-hosts "all" --jsonrpc-interface "all"
nginx config - I've made separate location for /rpc calls as said here
Also seems that /rpc is actually routed to :8180. That port is not affected by --jsonrpc-cors=all (actually it doesn't send cors headers at all), it should go to 8545 instead.
```
server {
listen *:8181;
location / {
client_max_body_size 5m;
proxy_busy_buffers_size 1024k;
proxy_buffer_size 64k;
proxy_buffers 32 64k;
proxy_redirect off;
proxy_hide_header Host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_http_version 1.1;
proxy_ssl_session_reuse on;
proxy_pass_request_headers on;
proxy_pass_header "X-Cache-Time";
proxy_pass http://127.0.0.1:8180;
}
location /rpc {
client_max_body_size 5m;
proxy_busy_buffers_size 1024k;
proxy_buffer_size 64k;
proxy_buffers 32 64k;
proxy_redirect off;
proxy_hide_header Host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_http_version 1.1;
proxy_ssl_session_reuse on;
proxy_pass_request_headers on;
proxy_pass_header "X-Cache-Time";
proxy_pass http://127.0.0.1:8545;
}
}
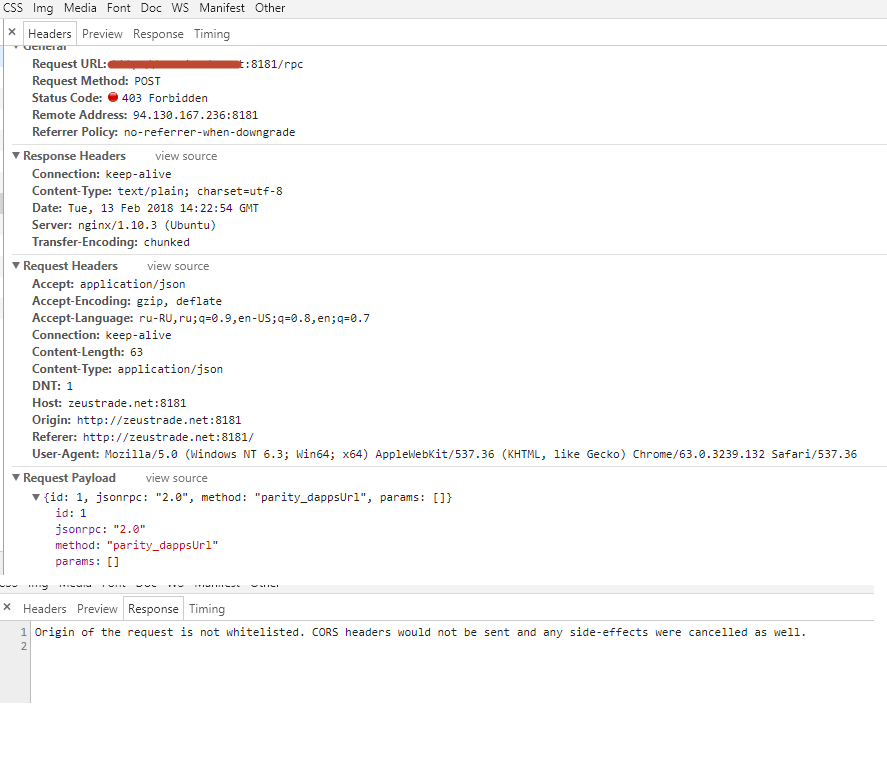
fixed with --jsonrpc-cors all option
Most helpful comment
fixed with
--jsonrpc-cors alloption