Notepad-plus-plus: Provide GPG signatures
Can you please add for all upcomming releases GPG signatures so we can verify the binarays are realy from you?
Currently only checksums (SHA1 - which is by the way not longer secure!) are available. It would also be nice if you replace the SHA1 with SHA512 checksums to increase the validity.
All 138 comments
There is already an issue for this #2327.
2327 is about SHA256 checksum- even if SHA512 would be better.
I write about GPG files: https://en.wikipedia.org/wiki/GNU_Privacy_Guard
Totally agree! This program is used not only on home PCs or programmers workstations, but also on mission critical servers. Generating secure hash and GPG signature doesn't cost any money, so it is really a matter of author's will.
Both GPG signature and AT LEAST SHA-256 are an must-have in todays sick world. Agree that SHA-512 would be better, and please note, that recent version of Total Commander or Hash Tab also allow to generate SHA-3 hashes - standard which was accepted in October 2012 and on this weird planet will be in general use maybe in 10 years (SHA-2 was accepted in 2001 and we are slowly switching to it since maybe 2015).
I'm glad that Author put hashes also on GitHub, which would require attacker to change hashes both on main project's site and on GitHub. I hope that Author have enabled two-factor authentication here.
And I would also suggets to remove or change _"Check it if you're paranoid."_ label from the website - it is not matter of being "weird" or "geek" to check the hashes, it's a matter of responsibility, that's why such label is really inappropriate.
I would really apreciate such changes. Thank you!
"Check it if you're paranoid."
sounds like an offending joke since the hashes are not signed (so there is no sense to check them) and sha1 and md5 are used which are insecure nowadays
push
Also SHA1 is now unsecure, but no change here.
To the author(s) it might be worth the time- As beerisgood mentioned, SHA-1 is not only no longer secure, but google and CWI have publicly published a paper and a publicly available example of a SHA-1 collision.
At the very least, the updates could be released with the SHA-256 or 512 or SHA-3. Ideally, as mentioned, the author would go with signing the release with a GPG key or something; but saelic pointed out that the site and github both list it and that's better than _nothing_.
push
Probably not GPG but sha256 will be provided in the next release (sha512 will be done as well in the future)
_sha512 will be done as well in the future_
Could you tell us, why not right now, but in the future? What exactly is the problem of creating such hashes? Same question about SHA3.
What about SHA256 Authenticode signature? If you have some sort of problems with DigiCert CA, take your interests in nice offer from Certum CA - they've got special offer for Open Source developers and are also offering SHA256 signing. https://www.certum.eu/certum/cert,offer_en_open_source_cs.xml
And finally, what about "Check it if you're paranoid." label on website?
Greetings
See also this news why SHA1 is shi*:
http://cynosureprime.blogspot.de/2017/08/320-million-hashes-exposed.html
push
@milipili
@donho
push
_push_
I can't believe that such trivial and cheap things are such a big problem in our world. No wonder why we have so many security nightmares.
<conspiracy-theorist-mode>Because the world is ruled by state security agencies and the majority of people are very loyal to them.</conspiracy-theorist-mode> (especially the males who were conscripted, in some states they are the majority of males)
Very interesting point, thank you for it.
I have never got british citizenship (and I'm not going to) and have never been knighted (and I'm not going to) .
I'm sorry, corrected :)
@milipili
@donho
push
More then 1,5 years now. It is realy so hard to create a GPG key, upload it to the GPG server, sign the binarys with the key and give us the .sig(s) with GPG-Fingerprint?
C'mon
push
Can't believe that i still watch this thread.
Also i create now a repository to provide better checksums and a GPG sig (with my key) for x64 installer version. If someone need data for other versions, told me.
I update my repository for new 7.5.8 release (both x86 & x64)
Also you guys should better watch my repo, cause i dont will post here more updates. (thats not the topic here)
Probably not GPG but sha256 will be provided in the next release (sha512 will be done as well in the future)
@donho
Checksums do not protect you from malicious modification. If your site gets hacked and installers modified, the checksums can also be adjusted.
A gpg signature with a private key (a key that's not stored on the site) is needed for this.
@bughit Of course you are totally right about using GPG.
I would also point out, that the installer should be at least dual-signed with SHA-1 and SHA-256.
But the thing in which I'm really interested is: what is the motivation for people like @donho for not providing such checksums right now.
- Free software for doing this exists (for example: md5deep, Power Shell, HashTab or built-in Linux programs).
- It takes seconds to do this.
- It can be automated.
- It doesn't need huge resources.
Mankind puts quadrillions of CPU cycles for idiotic things like Aero, Start screen, themes or forced updates, but when it come to really important stuff, they are almost always lazy, have whole bunch of excuses or even don't have a clue why they are doing something. Same thing with SHA-2 family: provided in 2001, commonly used since maybe 2013 where SHA-3 was available since October 2012. Always looking for things that are "just right" for now, but without setting up an margin for the future. I really don't know what is going on.
GPG sig is now important then ever (Nov 2016!):
https://www.bleepingcomputer.com/news/software/notepad-no-longer-code-signed-dev-wont-support-overpriced-cert-industry/
WTF
@donho I posted the solution in 2017 in this very thread! https://github.com/notepad-plus-plus/notepad-plus-plus/issues/2524#issuecomment-326769068
KeePass is using these cert for example.
installer should be at least dual-signed with SHA-1
SHA1 shouldn't be used for signatures. Though use for MAC is still suitable.
Yes, I know that, and I prefer to use even SHA-512 and totally drop MD5 and SHA1 hashes. I pointed out the "dual-sign" thing with having compatibility with older systems in mind. Windows NT 4.0 through Windows Vista, even if they are no longer supported, they are still used. But then probably the GPG signature would be better.
@beerisgood
I did try GPG signing, and different from Winows' code signing certificate, the signature is detached. So here my question: which API in C++ should I use to verify the signature? Do you have any example about the implementation?
@saelic
WTF
@donho I posted the solution in 2017 in this very thread! #2524 (comment)
Certum? They are my nightmare:
https://notepad-plus-plus.org/community/topic/17184/remove-code-signing-from-notepad
I guess we are talking about totally different things.
- You are talking about validating those files from the application itself.
- We are talking about signing the installer files - exe, zip, 7z.
Certum? They are my nightmare:
https://notepad-plus-plus.org/community/topic/17184/remove-code-signing-from-notepad
Don't know the case, but KeePass is doing fine, I can't remember other projects right now, but I'm sure that I saw them.
@saelic
You are talking about validating those files from the application itself.
We are talking about signing the installer files - exe, zip, 7z.
Maybe I still stay on Microsoft signing system logic and don't get yet GPG usage.
Is there no way to validating the GPG signature of its component inside of Notepad++ ?
@donho
Are you referring to verifying the signature when updating from np++?
https://www.gnupg.org/software/gpgme/index.html
The gpgme dll is part of gpg binary distribution, or you can build it.
LibreSSL should also have such thing.
But the most important thing is to sign the distribution files and sharing the signature files with the installer/archive. Generate your keypair, post on some keyserver (pgp.mit.edu for example) and sign the files. Kleopatra application is your friend.
@saelic @bughit
Thank you for your information.
I will check them and make GPG signature available ASAP in Notepad++.
Thank you very much!
I'm really glad that the problem was noticed by you and if you need assistance I'm ready to help you.
Gosh, now when I'm thinking about the whole case I'm surprised that we could not understand each other. I didn't even think that you were talking about signature validation during runtime (which of course is cool). But I thought that when we were talking for example about removal of the "if you are paranoid" label on the project's website, then it was obvious that we all assume attaching the signature files. I'm really glad that we finally understand each other :)
I didn't even think that you were talking about signature validation during runtime (which of course is cool).
It's part of stuff I pay attention now thanks to CIA:
https://notepad-plus-plus.org/news/notepad-7.3.3-fix-cia-hacking-issue.html
I know, that's why I said it is cool ;)
i've noticed a popular key hosting network with interesting features targeting devs that you may be interested in at least posting your keys on their site linked via https://github.com/keybase and thanks for a very useful notepad adaption for windows folks.
i've noticed a popular key hosting network with interesting features targeting devs that you may be interested in at least posting your keys on their site linked via https://github.com/keybase and thanks for a very useful notepad adaption for windows folks.
No please not keybase. Didn't they have security problems in the past?
Just use the official GPG key server.
keybase
centralised service
No, thanks.
Back to the Certum thing: why you don't want to just give them your name? Then the CN would look like "Open Source Developer, Don Ho".
Look how KeePass done this. Download executable from here and look up the _Digital signature_ tab.
About GPG: I suggest you to use the 4096 bit key, just like PuTTY does.
Look how KeePass done this. Download executable from here and look up the _Digital signature_ tab.
Official site is: https://keepass.info/download.html
No please not keybase. Didn't they have security problems in the past?
Just use the official GPG key server.
please cite sources about security problems, or it didn't happen (edit: but really, everyone has had a security problem at some point, so the relevant point is what it overly obvious and high severity or not, since they do the proper thing of publishing security advisories).
also, afaik no such thing as "official gpg key server", otherwise that makes it a "centralized service", which is generally frowned upon by people interested in open source freedom.
(edit: oh now i remember there is something about network of key servers that mirror each other https://sks-keyservers.net/overview-of-pools.php and so i suppose that is what you may be referring to, but still, no reason not to add other mirror venues.)
keybase
centralised service
No, thanks.
https://keybase.io/docs can just be used as yet another place to retrieve a public key and optionally associate with other identities for convenience, so there is no reason to dismiss it as just a "centralized service".
public keys are just hosted wherever someone feels like it, and do not have to be hosted in a single location, so there is no reason not to share the public key on keybase as well as whatever other various hosting sites that are trendy.
in any case, as long as there are multiple pointers to the public key locations making them easy to find and verify, then that is the important thing, as i have come across a few projects that provide signatures but forgot to provide obvious pointers on where to find the public key to verify them with, lolz.
Official site + GitHub + MIT Keyserver for start should be enough.
Official site + GitHub + MIT Keyserver for start should be enough.
in this case then those 3 are sufficient.
the other project i was thinking of (that i referred to mirror on keybase for easy searchability by name) is on sourceforge (which either does not facilitate or make it obvious how author should share public keys in profile).
Back to the Certum thing: why you don't want to just give them your name? Then the CN would look like "Open Source Developer, Don Ho".
The thing is, Don Ho is not even my official name (on my passport). The CN name is hard coded in the source code for the certificate verification of inter-component. And I don't want to people be able to dig my personal info so easily.
So that's not exactly a problem with Certum from the beginning. Issuing a certificate for some "body" that officially doesn't exist is a straight way to lose ability to issue trusted certificates and their motivation is totally understandable.
So we ended up in this: distribution files will be signed with GPG, which is all that we wanted.
You said that you don't care about "unverified publisher" UAC prompt
_"Too bad for ugly yellow-orange UAC popup while installation"_.
This problem is wider than just installation.
- Imagine that someone needs to run Notepad++ as administrator - he also gets the same message.
- You implemented the runtime validation of the components. But when the main executable is not signed, then it can be modified without notice, for example to modify hashes of modules to match the tampered ones. The whole concept of runtime validation is losing it's sense.
- Keep in mind that people who are using some kind of software execution control (like Software Restrictions Policies or AppLocker) with the requirement for valid signature will have problems.
- AntiVirus software also more trust the singed executables and without them the program will probably end up in some kind of "Restricted software" group, which could result for example in some alerts when user wants to read/write some data in his home directory.
We are not in Windows XP SP1 era any more.
I understand that you want to protect your privacy as a person - that's totally fine. But keep in mind that you produce software that is used by a lot (millions?) of people, so it really would be a good idea to add some level of credibility and trust. Again, KeePass, PuTTY, Notepad2, WinSCP, Total Commander authors do it.
I don't want to force you to do anything, but really trying to resolve the situation. Even if there are people who can sponsor the certificate, then nobody conscious will sign it using his name - after all, you are producing the binaries.
If you really don't want to share your identity, then maybe ask DigiCert to donate the certificate again and in repay you will put their logo on the site with some kind of "Thank you to our sponsor" page.
Issuing a certificate for some "body" that officially doesn't exist is a straight way to lose ability to issue trusted certificates and their motivation is totally understandable.
The body exists. It is CA system flawed.
Imagine that someone needs to run Notepad++ as administrator - he also gets the same message.
Not a problem. A powerful malicious entity can get a valid cert for any name it wants. Also a just malicious entity can find a homeless person, wash him, pay him for changing his legal name to Don Ho and pay him for getting a valid cert in a completely official way. How can you be sure that Don Ho is the person you mean, not another person with the same name? The only way to ensure this is to get public key personally from a person whoose traits you know well enough to spot the fake. Or public key fingerprint, if you assumme that the hash function is secure, but IMHO it is far more secure and nearly as easy to get the key directly.
So the only security we have when using software by unknown persons from the internet is Trust on First Use. You know what the public key is used to be and watch the changes in it. And you hope that the time you have acquired it first it was by the right person, not CIA. Surely it will fail in the world where everyone is mitmed with high probability, but we don't live in such a world, otherwise it would have been already spotted.
I agree with everything you said about CA flaws. The only thing left for us is something like DNS CAA where we assume, that the CA of choice will not make it easy to issue a certificate for already existing body.
Also a just malicious entity can find a homeless person, wash him, pay him for changing his legal name to Don Ho and pay him for getting a valid cert in a completely official way.
That's a brilliant idea! Thank you @KOLANICH :P
So I just created a GPG key pair (RSA 2048) with Notepad++ & don.[email protected] attached (I suppose it's the certificate). I did the key pair backup and did a revoke certificate. So what's the next step?
How do I sign my binaries and how do I verify the signatures with the signed binaries?
RSA 2048
4096 is minimum.
@KOLANICH 4096 is not minimum but maximum in Kleopatra's option.
Regenerated. So what should I do now?
So what's the next step?
Go to https://keyserver.ubuntu.com/ and paste there your public key. Also add it into your GitHub profile and NPP website and sign and push some tags/commits using this keypair into NPP repo. Also you would need some of your friends you personally know, who are well-known devs, to sign your public key (offline, meeting them personally!), and then publish the public key with their signatures.
- Right click on EXE/ZIP -> Kleopatra (or More GPGex options) -> Sign
- Publish your public key on site/github/keyserver
- Publish created signatures.
- Remove MD5 and SHA-1 hashes - they are useless. Instead post SHA-256 and maybe SHA-512.
- I suggest to remove the "check if you are paranoid" label - it's not helping in increasing security and awareness.
@KOLANICH :
Go to https://keyserver.ubuntu.com/ and paste there your public key.
In Kleopatra there's a command Publish on server... - is it the same thing?
who are well-known devs, to sign your public key (offline, meeting them personally!)
I don't know any well-known-devs. Is this part is mandatory?
@saelic
How people under windows verify the signature with signed notepad++.exe ?
remove the "check if you are paranoid" label
Done, it will take effect in few hours.
In Kleopatra there's a command
Publish on server...- is it the same thing?
Yes.
I would suggest to use primarily the pgp.mit.edu since it is one of the oldest and well-known key server.
I don't know any well-known-devs. Is this part is mandatory?
Well, to validate key authenticity people are organizing events named _Key Signing Party_ where participants validates each-other's key hashes. When you don't have such network of people who can reliably confirm that your key is really yours, then I suggest to do the following steps:
- Export your public key to the .asc file.
- Export your public key to the keyserver.
- Put the ASC file on the Notepad++ website.
- Put the content of the file (that's your public key) in GitHub profile.
- Put the content of the file in reply to this topic.
That way, you will publish it in four different places. If you have Twitter for example, then you can also publish it there (or just hash of it, but make sure that it is a SHA-256 hash and you need to also post the key ID).
When somebody wants your key, then he will be able to validate it from those sources. After he imports it to his keyring, he no longer needs to download it again and now is able to validate signatures against your key, which he already has in his local key database (keyring). That's why it is far superior method to just providing checksums - attacker can't change the content of user's local keyring (and if he wants to "tamper the signature", then he will be forced to break into all user's computers which have the key - that's obviously infeasible).
How people under windows verify the signature with signed notepad++.exe ?
After user imports your public key for the first time, he need to add some level of trust to it - based on his level of being sure that the key belongs to you. After that he can just simply double-click the signature file - which you provide with every distribution file of the Notepad++ release - and Kleopatra (or GPG or some other PGP-like program) will tell if the signature is correct. This proves that the file has not been tampered since you signed it.
Keep in mind, that you are not forced to sign every single distribution file. When you for example make checksum files (separate for SHA-256 and SHA-512) then you can only sing those checksum files. When the signature for the checksum file is correct, then we can assume that the file holds values for original (not tampered) distribution file. This is why you need to use the best available, long-term hashes. Their security is crucial to the whole process, especially when we are talking about small chunks of data.
This approach is used for example by Debian GNU/Linux distribution, you can see how it's done here.
This process can be easily automated and you will be asked for a passphrase to your private key only once during the process.
Also keep in mind, that source code packages should also be checksummed and signed.
It is also a good idea to use SHA-3 hashes, which we have for almost 7 years.
Just for the sake of making it clear:
SHA-2 and SHA-3 are the family of functions. So in point of fact:
SHA-256 is the SHA-2 256-bit variant which produces the 256-bit long hash.
SHA-512 is the SHA-2 512-bit variant which produces the 512-bit long hash.
So it would be better to call SHA-256 really an SHA-2-256 and SHA-512 the SHA-2-512.
SHA-3 is exactly the same schema:
SHA-3-256 variant produces the 256-bit long hash.
SHA-3-512 variant produces the 256-bit long hash.
Done, it will take effect in few hours.
Thank you.
By the way:
- Which signature algorithm/hash you've selected for your key?
- Are you using some good antivirus program on your build machine?
- Are you looking towards making builds reproducible?
Done, it will take effect in few hours.
Effect: _Check it to verify the authenticity of your Notepad++ download._
Not authenticity, but integrity. Authentication can only be verified with digital signature.
@saelic
Thank you for your very detailed info.
Just sign my commit on git with a beautiful verified :
https://github.com/notepad-plus-plus/notepad-plus-plus/commit/5356f648c21a1bc6fc96dcb9078bddce9dadcc37
Not authenticity, but integrity. Authentication can only be verified with digital signature.
Makes sense. Modified.
Which signature algorithm/hash you've selected for your key?
RSA
Are you using some good antivirus program on your build machine?
Which one do you suggest?
Are you looking towards making builds reproducible?
I don't really get your question, could you elaborate it?
BTW, here's my public key:
-----BEGIN PGP PUBLIC KEY BLOCK-----
Comment: User-ID: Notepad++ don.h@free.fr
Comment: Created: 3/11/2019 10:16 PM
Comment: Expires: 3/11/2021 12:00 PM
Comment: Type: 4096-bit RSA (secret key available)
Comment: Usage: Signing, Encryption, Certifying User-IDs
Comment: Fingerprint: 14BCE4362749B2B51F8C71226C429F1D8D84F46E
mQINBFyG0B4BEACrgYc13VSS1UNXz88cGDmTSSZsMHC9516jahXBERZYNAPSCONe
1XFEFpp33rNByz89v5sojyL0V+PM5HOeKovRcGNULGQmy2qiX+67J+3vc7znva4d
kDERhajJtax3830efAHJ3Zvbz/0V5waG8oPSJcPCcYhkmQa5N1aSk8QGKdMd3cUb
v8Mmw0KWGP7GFkGeIZ0/Dfkzn75T7goAP29aRZiidApRGVsjKIDuv+XyHn+hpGPP
SNDs3Lgai8lIAYNuXYbR5SenKWQ4a5M+cQLeAPcd5dLrRBO/sYBgIrs+GSYzZv/S
/gi3o2I9V36c2U+iKuqvan1X7h3Y1/LuiJGT+5yIStEogVaCNJkLB+OK6rETIUvu
BM0efk5BN+owUlZCfm5O3MMzkq0ib50QdrSdxLOYq5j+TVqWJd3FwXOR8GkB7JvI
s6viWsCRl/lOtmEl/5MQXtYUCcZtANEGsn5Vclfmj7gtYD4FvNAnE71GczobbZJw
b4TEb8yXQNWB11G4ynCRMtlwUlXXScBRHokW2RY43XOQ//tf0REI0F1P6TWBK9lE
1OSGVL4OnqBExb/OzYdA3iZaCkP1KTPTIm9AA6XA5L6SiPW0hjU75Zjm3SWZ58Jc
xoTlebiGmrsqSTkwEmyR87YkyhCaSchKfCDN9Rb9zVppAcGzo7MXz4oLgQARAQAB
tBlOb3RlcGFkKysgPGRvbi5oQGZyZWUuZnI+iQJUBBMBCAA+FiEEFLzkNidJsrUf
jHEibEKfHY2E9G4FAlyG0B4CGwMFCQPDKBIFCwkIBwIGFQoJCAsCBBYCAwECHgEC
F4AACgkQbEKfHY2E9G4GfxAAlCQpZ7g+GEPmMvZGQ+klaJKaenT33yIq0dHsIr2O
witP9CFjtU5QTMAtvXc85GKiUfHUtiOV357GyBh7xebTVX26i1xd0ZMkbjl10AN+
RN0lhtY7Q+WFNVFmNM7NsYL/cTQRCcrSi48YGLmmDYwRWVRGTR+W7salv01/gOrA
rzSqqlaUhtUU3eApiHTCsQpKNHNxl1ToVIofUFCJ5eKczCFOhDstHFlIRr9LI+Vt
IlOn9nCVs/acNeePQCGxJ3aDV6MK/y582YckzxhjJcpnVfkNPGwOgy9Xe+D9Op8e
AhaOtrwbZfcsvgmZPI1S7aJBID7rSP6hn3DCDN0uNqkKfLEcLj8JbJGuAFxqjCSe
fgDNEC1Mqh+PQPyMEfKl1v5jGsWzMt9dRk7pPivjlf9ZLMUvEKlB2J2mYLuPa+c8
hzQ4Uc5AKiPglfdV0QbkzInLclqEv/Mj/+2u9A4erQs9pgGiZY3e7azMjbNQNJ7Z
vGiKmbauKlp5JtUJJnfhD7QGKJw8vwh5ozC0gRnVEWu7s+qU9p0uCFwgivPWi8C1
/s++EMgTWYwHP+Ih5nqfT/jdWEblC2enu/ouatp4oggy1vUOFBpAZj4ZFgTewFyP
skOvT3Qscm1W8wzNaA+vGwFfnVUooxnefJVt2BlG9+nvCPrqcxoGDqUxAEoPuNve
Cwq5Ag0EXIbQHgEQAN+jWJhz2zZArBONKtsk0Vp8xhJOyG0/lyS80EHC1c2A8+9p
zsR9t+azjk7CmiSAZMx2/vs9KlE7SpTnEgyg13N3gDgsS4oWXL/3hf/9U75w+++v
5xWLvq+3OHILdm8BhFLgqhL/McUz1ARQtE1lsvWYrRziidY+oXQh1qzH4LAKRReq
MxWqMAJd9bgSf2drf0pAxmcz5e8qoOVOBBBjQ9ZowPx6cLwulDEcJNcwY0tjvmIh
sq8GVfKYNhVS06tVtWB78ngauvsNesPbL4vjxCr6XLeEYadW3gQYNVaPm0ajyXgH
LuJb3YDpd95ORdQ7Wg0DE4ZX7zgTdUdU+wgERO8FpeTT3mnueE/KYrQHZWxgo70l
H7YIqX6c/aFLc6k90XxukawQPe/ECuQhy4iOt1o//PoEfcewyGlXOHSz4lm8/A9o
Hk6MyofogbS9sEMQe+EuiroGJ3WZ2bMc5syE1O3XUYGPVDpTzRVS8Fa3DRxWYt9v
r/XC8ZWU8dcmOtqYQFCoR7odPXKIib4xkz3XIRF+gqy0Z+1z8xSacrfHefmRl5Q6
1PcQra8LQ6wSWijud2gp3xCfXfIuyL1JfASFykPIVFrY8TxjecUjxfUlthO+B1mI
k6sF2kEpZQQHL9a+at6ax0vk2UrDglTcGzZUk+VdCAaZWdhf5EWq1yFTrp2pABEB
AAGJAjwEGAEIACYWIQQUvOQ2J0mytR+McSJsQp8djYT0bgUCXIbQHgIbDAUJA8Mo
EgAKCRBsQp8djYT0bkOoEACOf/AQOOJ7LPfwZosdn7nzwrM21idjyvnIZLo3aec3
yu7zNn3XS5DM2+3Vv1Ra8t8f4BWWKvCiga5Ksqq2NhTt6IrE8FZ3H8I/8WksgAx8
4axWKFpAi/Wvf+H63/EvdmvY97SYTxTh5EXy0lu4TIQZaVAxO4gI86vNUuWmB5Be
I9OFfEjy64iHyMk9m4qZXzDgHBkXzVQ1WrHVRXAMjHn8C+zw878a656PfJzOMwAD
prCC65LpHZ9CO6jyHAlb8E6PYra4LWp+XMIXCqE7TRIZCnZYnzCUgnLRN/8JW/bJ
y2R/A3yNSZQkwQkEEsOByD4a/rYpmgDQl0cuQvcD4ONcl9XrRQUbaiIxz4gWoZSc
S1ykh/6xZ5rnuj2/WTmzYnmGQFED5sxNdTW/rjx3Q6o9Pf0KviWCi3WeBXLm76n0
WE0kts/fCcQxmgr5sLFvb3gNPNle90I2XIUWmBD6O3DQAeL4Wk2yYCKsSq6LCwgZ
+Imn3KUrk7Z8DG4DWUbuLmw245R2khdtcoZ3EdfiyAteJbSlhwLPhVt3NWGq5CGk
h6OnmWtlAbf+Flaej9vo1O8MUzfNtVavmfGwan3Z9FNQ6gm3u/2WcJVVCiDEC5iF
w1PnQAgdlZBOn+8diM0qpq/VI0RheGJMiPg55rvtnUJ3cOWvE5gPuK2C9YTnhk/a
Lg==
=x8Cx
-----END PGP PUBLIC KEY BLOCK-----
That way, you will publish it in four different places.
All of which are under either NSA or GCHQ jurisdiction.
I would suggest to use primarily the pgp.mit.edu
I used to use it, but it has heen down for some time, so I have switched to Ubuntu one.
Are you using some good antivirus program on your build machine?
Which one do you suggest?
There is ain't no such a thing, as a good AV. They are mostly based on signatures, signatures need to be reguoarily updated because there exist such a tool as packer, defeating signature analysis. A malware that rooted your system can install a kernel module protecting it from being removed and/or detected. It is called rootkit. Though they can be detected by a class of tools called "red pills" using unforgeable timer, but this is heavy artillery. For better persistence malware can create a bios/uefi module and flash it into bios. For extreme persistence malware can infect peripherials firmwares too. And this technique has been used by malicious actors, according to Kaspersky Lab.
You shouldn't use AV, you should use isolation; you should not allow any unapproved code to gain access to your private key, source code in process or before build and the built binaries before signing. And I feel that backdoors may be problems here, you should not keep your private keys on machines backdoored by hardware or software vendors.
To protect your key you can use a hardware security module. They generate keypairs inside of it and then you use software to send data to the module and module signs the data and returns you the signature. You can upgrade your key by signing new public key with old private key, prooving your ownership of the old key, then start using tue new key, and after some time enough revoke the old key.
Please hote that not all HSMs are really HSMs. There were some devices marketed as hsms, but in fact the researchers found that private keys were extractable.
Which signature algorithm/hash you've selected for your key?
RSA
Maybe I wasn't that clear: I was asking about signature hash algorithm - SHA-256/SHA-512 etc. I see from the attached key that it is SHA-512 and that's nice.
Are you using some good antivirus program on your build machine?
Which one do you suggest?
I would suggest Kaspersky products. It should be enough to say that leaked presentations from GHCQ say that those programs are a pain even for them and also Kevin Mitnick said the same in his presentation here.
They are mostly based on signatures, signatures need to be reguoarily updated because there exist such a tool as packer, defeating signature analysis.
That was true till about 1995. Norton AntiVirus 5.0 had Bloodhound technology in 1996, which was one of the first technologies which allowed to detect unknown viruses. Since early 2000-s we've got behavioural detection of malware which analyses what software is trying to do on the system.
You shouldn't use AV, you should use isolation
AV technologies prevented many infections like ransomware, so I would never say that you don't need AV or AV is dead. Now we also have white-list technologies, which when properly implemented are really difficult to bypass.
you should not allow any unapproved code to gain access to your private key, source code in process or before build and the built binaries before signing. And I feel that backdoors may be problems here, you should not keep your private keys on machines backdoored by hardware or software vendors.
Problem is wider. There are viruses which search for source code files on developer machines and are attaching themselves to those sources, so the resulting binary is infected. Building software for a lot of users is a very complicated task - there should be a dedicated server with ECC memory, private key for signing stored elsewhere, restricted network connection and many, many more rules. Programs like Notepad++ are used not only on home or developer computers, but also on servers, so a problem in such program can have massive consequences.
A malware that rooted your system can install a kernel module protecting it from being removed and/or detected. It is called rootkit. Though they can be detected by a class of tools called "red pills" using unforgeable timer, but this is heavy artillery.
That's why it is critical to not allow such installation and it can be done with mechanisms built in operating system, as well as antivirus behavioral detection. Antivirus should be installed as the first program after system installation to prohibit such situations.
For better persistence malware can create a bios/uefi module and flash it into bios. For extreme persistence malware can infect peripherials firmwares too. And this technique has been used by malicious actors, according to Kaspersky Lab.
That's true and that's a new problem we have.
That way, you will publish it in four different places.
All of which are under either NSA or GCHQ jurisdiction.
Good point. I don't know where the hosting server lies, but indeed GitHub, MIT and Twitter are under their jurisdiction.
Are you looking towards making builds reproducible?
I don't really get your question, could you elaborate it?
We are living in times where multiprocessing is used on the global scale. That's why the underlying mechanisms of doing the same things may differ. It is especially seen in the software build labs where the same binary could be different even if build on the same machine using the same source code. This is not really a new problem, but it has been noticed on a wider scale not long ago. For more information see this site
@KOLANICH :
Go to https://keyserver.ubuntu.com/ and paste there your public key.
When I paste the public key I posted above then submitted it, I've got the following message:
Error handling request
Error handling request. Exception raised.
whereas on pgp.mit.edu, I've got:
Service Temporarily Unavailable
The server is temporarily unable to service your request due to maintenance downtime or capacity problems. Please try again later.
All of which are under either NSA or GCHQ jurisdiction.
Not for Notepad++ website & its binaries - they are hosted in France.
Not for Notepad++ website & its binaries - they are hosted in France.
Well, now when I'm thinking of it, the jurisdiction of NSA and GHCQ is... the whole world :)
Since early 2000-s we've got behavioural detection of malware
Which works damn bad and giving lots of false positives.
There are viruses which search for source code files on developer machines and are attaching themselves to those sources, so the resulting binary is infected.
On needs not to have any active malware on the machine.
It is especially seen in the software build labs where the same binary could be different even if build on the same machine using the same source code.
I wonder what prevents modifying compilers and linkers the way making the builds reproducible? Everything is needed to make the build reproducible is a predictable RNG, non-writing any additional metainformation got from FS, system clock and static libraries built reproducibly. Why do people create virtual environments with the tools like gitian rather than to just patch the toolchains to do the work?
Not for Notepad++ website & its binaries - they are hosted in France.
France has own intelligence agencies, France is a member of NATO and France can do favour to their US ally. There were multiple cases of Russian citizens captured in Europe and deported to US, including the ones doing legal business in Russia, which was outlawed by US. I am mean Alexander Vinnick - a person related to russian cryptocurrency exchange BTCe not complying to US KYC laws. He was captured in Greece and deported into US.
One must understand that if something is beneficial to both states (in the case of Vinnik - US and Greece, though we don;t know the benefit of Greece), they will make an aggreement. For example, if US can promise France to install their backdoors too, France can help US in their espionage. This is mutually beneficial for them.
There are also such things as business interests. If one business can be affected by a foreign state a lot, for example access to their servers can be blocked in that state, it will comply. An example of that is Russia forcing Google and Amazon to implement anti-meek countermeasures in order not to be blocked. Or Google creating a censored version of their search engine.
IMHO if Snowden gone to France, he would be already deported to US and prosecuted.
@saelic
How can I know about signature hash algorithm from kleopatra or gpg comes with git?
I would suggest Kaspersky products.
I've installed Kaspersky (free version?) long time ago, and I had some performance issue due to it. I'll give it a try again.
We are living in times where multiprocessing is used on the global scale. That's why the underlying mechanisms of doing the same things may differ.
Thank you for the info!
BTW, I'm preparing the next release : All packages will be signed with the private key I generated.
I will provide the signature (a detached gpg file) for each released package, and also my public key in asc format on download page. Am I missing somethings ?
How can I know about signature hash algorithm from kleopatra or gpg comes with git?
It should be in key properties. Can't check this right now.
I had some performance issue due to it. I'll give it a try again.
You should exclude scanning of the Notepad++ build directory and also put it to the "personal data" category to prohibit unauthorized changes to files in it. Those features are in paid version, I would recommend the "Internet Security" variant.
All packages will be signed with the private key I generated. I will provide the signature (a detached gpg file) for each released package, and also my public key in asc format on download page. Am I missing somethings ?
That's fine. In addition:
- Remove the MD5 and SHA1 checksums and replace them with SHA-256 and SHA-512. Put them in two separate files - checksums.sha256 and checksums.sha512 - it's easier to validate them. Then put them on the site and GitHub.
- Sign the checksum files (checksums.sha256 and checksums.sha512).
- Sign source code package.
I also recommend to:
- Enable two-factor authentication on your GitHub profile (if you didn't do that already).
- Make "big" announcement on site about changed policy regarding packages authentication.
I also suggest to:
- Redesign the download site and put links to the table - it will remove "label redundancy" and make them look simpler. You can also use the drop-down list or the group of them.
- Move the "Release notes" out of the download site.
For example:
32-bit | Installer ; Sig | ZIP ; Sig | 7z ; Sig | Minimalist ; Sig | Checksums ; Sig |
64-bit | Installer ; Sig | ZIP ; Sig | 7z ; Sig | Minimalist ; Sig | Checksums ; Sig |
The above public key has been submitted in the following keyservers:
http://keys.gnupg.net/
https://keyserver.ubuntu.com/
https://pgp.mit.edu/
https://zimmermann.mayfirst.org/
The above public key has been submitted in the following keyservers:
A key uploaded into 1 keyserver is automatically synced to other ones.
Here's a signature test on my old release. Could you guys tell me if everything is OK on this page?
(Verifying of signatures & checksums, the terms used in the content, etc...)
If everything is OK, I will use it as template for the future release.
https://notepad-plus-plus.org/download/v7.5.5.html
OK, I checked them.
You haven't signed the packages, you encrypted or probably signed and encrypted them. That's why the resulting files are huge in size. Keep in mind that the digital signature is a small file, often an longer ASCII string, which can be attached to a text document. The resulting file should have .asc or .sig extension. Remember that GPG isn't the only one PGP-like program, so we need to keep compatibility also.
About the download site:
- I would change the Authenticity/Integrity label to Integrity & Authenticity validation. For the sake of order of things.
- There are no SHA-512 checksums.
- There is no signature for source code package.
- Keep in mind that you can also sign release notes as text - it's common practice for example in mailling lists, for example here. As you can see, the signature is attached to the end of the message as ASCII string.
- Please try the arrangement using table - look how nicely it looks for example here.
Aside from the signatures stuff (which has been fascinating reading, BTW...)...
Regarding a table, wouldn't the following (mockup) look great on the download site (and clear up long-standing confusion users have had about where to find the "portable" version)?:
Description 64-bit 32-bit
Installer npp.7.5.5.Installer.x64.exe npp.7.5.5.Installer.x64.exe
Portable npp.7.5.5.bin.x64.zip npp.7.5.5.bin.zip
npp.7.5.5.bin.x64.7z npp.7.5.5.bin.7z
Portable npp.7.5.5.bin.minimalist.x64.7z npp.7.5.5.bin.minimalist.7z
(Minimalist)
@saelic Thank you for your verification.
You haven't signed the packages, you encrypted or probably signed and encrypted them.
Fixed.
I would change the Authenticity/Integrity label to Integrity & Authenticity validation. For the sake of order of things.
Indeed it's better. Done.
There are no SHA-512 checksums.
It'll be added in the future. Currently, we do without it.
There is no signature for source code package.
The source package is downloadable in release page of github. It's OK to me if we can do it on github in an automatic way. Otherwise I don't make more charge in release process.
Keep in mind that you can also sign release notes as text - it's common practice for example in mailling lists, for example here. As you can see, the signature is attached to the end of the message as ASCII string.
Maybe I'm wrong, but In Windows people prefer see the text less "encrypted". So I prefer to keep the signature detached.
Please try the arrangement using table - look how nicely.
Hmm... let's keep the old way for the moment.
@sasumner _(which has been fascinating reading, BTW...)_
Thank you for this. It's really nice to hear any appreciation when security people do their stuff. It's really hard and sad when nobody notice what has been done, people are often in doubt if what they are doing makes any sense. I'm sure that if more kind words would be said in such situations, then we would feel much more supported and appreciated, which would result in being motivated and more effective.
@donho
I've downloaded and checked all of the signatures and everything looks fine.
I would add are the links to your public key on:
- GitHub
- one of the keyservers
Also I think it's good idea to put package with source code on the main server, together with binaries. It's the integral part of the project, so I think it should be in one place. And then you can also provide signature for it.
It's really nice to hear any appreciation when security people do their stuff. It's really hard and sad when nobody notice what has been done, people are often in doubt if what they are doing makes any sense.
There's no doubt to me for sure. The problem is the devs want their codes work quickly, and while everything works fine, the security experts are the balls breakers who impose a lot of restriction to make their implementation (in the naïve and easy to be maintained way) harder, until their software get hacked...
Thank you (and others) very much for the help. I'm kind lucky to get all the assistance from you.
I would add are the links to your public key on:
GitHub
Do you see my public key for signing the commit? If yes, could you provide me the link? Otherwise how can I publish it on github?
Is it a good way to push it in the repository as a file:
https://github.com/notepad-plus-plus/notepad-plus-plus/blob/master/npp.gpg.pub.key
so it can be published as:
https://github.com/notepad-plus-plus/notepad-plus-plus/blob/master/CONTRIBUTING.md
?
Also I think it's good idea to put package with source code on the main server, together with binaries. It's the integral part of the project, so I think it should be in one place. And then you can also provide signature for it.
I will consider it.
may be useful to show the key fingerprint on the site and github readme, (highlighting the key id portion of it )
14BCE4362749B2B51F8C71226C429F1D8D84F46E
Download Notepad++ source code of current version and/or check sha-256 digests for binary packages on GitHub
SHA256 digests computed by GH and signature validation done by GH is untrusted. Everyone should do own one.
may be useful to show the key fingerprint on the site and github readme, (highlighting the key id portion of it )
@donho plese notice that short fingerprints are insecure, one should always use full ones if he uses fingerprints.
@donho after checking the template, i noticed maybe autocorrect typo "the integrality of" > "the integrity of"
i also like the @saelic suggested table format example they gave earlier. though i'm sure i've seen sites use this style... i cannot remember a good example site right now.
| 32-bit | Installer ; Sig | Portable 7z ; Sig | Minimalist 7z ; Sig | Checksums ; Sig |
| 64-bit | Installer ; Sig | Portable 7z ; Sig | Minimalist 7z ; Sig | Checksums ; Sig |
also, it is time to let Zip die, because 7z has been around for 20 years, so if somebody is "advanced enough" to want something other than an automated installer, then they already have (or can go find) tools to work with 7z files.
the pgp.mit.edu server seems a bit buggy for me as well as keyserver.ubuntu.com lately, so i think that is why i had suggested someone use keybase.io until i remembered the https://sks-keyservers.net/status network to find properly functional servers (which does not list mit and says ubuntu is disqualified somehow).
also http://keys.gnupg.net security weirdness side note: i dunno where that sketchy looking (or just horribly configured) site came from, but it doesn't have valid SSL setup, and just loads "functionally" once... and then NoScript shows it runs weird 3rd party scripts that auto-forward to another domain for me in Fx but not GC browser.
http://keys.gnupg.net seems like it may be an alternate domain for https://pgpkeys.co.uk site which is actually listed on keyserver status page (and doesn't load weird 3rd party scripts), so maybe just stick to using sites from the status page (because no telling what other weird ways the site is compromised or trying to compromise you).
anyway, this has been a good educational refresher to follow.
it is time to let Zip die, because 7z has been around for 20 years
Is there data that says the 7z format is more "popular" than the zip format?
and then NoScript shows it runs weird 3rd party scripts that auto-forward to another domain for me in Fx but not GC browser.
Deserves some investigation.
Is there data that says the 7z format is more "popular" than the zip format?
On almost every computer I have seen either 7zip or WinRar is installed. I prefer 7z + LZMA + 9 (lzma is single threaded, but compresses better than lzma2, though usually it is fast enough not to bother about it being single threaded) over rar or rar5 because of its better compression.
it is time to let Zip die, because 7z has been around for 20 years
Is there data that says the 7z format is more "popular" than the zip format?
i'm never really as concerned about "popular" because look at what "popular" gets us, right?
especially in terms of technology we're stagnating under inferior technology of 1990s:
- jpg instead of jpg2000 (or webp or whatever better open image codecs)
- zip instead of 7z (or slightly newer open compression systems)
- mp3 instead of opus (and other more task appropriate open codecs)
- hashing with MD5 and SHA2-256 (instead of SHA3-512)
- crypto without using SCRYPT, ChaCha20, Argon2 (probably forgetting others from a 2018 report)
with the one exception seeming to be video (at least on BD and computer streaming) because those things are big enough that people actually try to do something about it instead of saying, "meh good enough who cares about a little inefficiency?"
so yeah, let 20 year old tech die when there are superior replacements, and "be the change you want to see" etc.
and back on topic, PGP is still hanging in there due at least being able to change with the times a little and increase key size to 4k as computers got more powerful.
@donho
Thank you (and others) very much for the help. I'm kind lucky to get all the assistance from you.
Glad I could help, you can always ask me in the future.
If yes, could you provide me the link
I think that the only solution is what @bughit suggested.
The problem is the devs want their codes work quickly, and while everything works fine, the security experts are the balls breakers who impose a lot of restriction to make their implementation
Well, that's the problem in general. I don't work with devs very often, but situation is the same. The point is that things should be done right, not fast - especially in the open source software development.
That's why I liked when Debian always released new version _"when it was ready"_. That's also why systems like OpenBSD are so secure - correctness is the priority. You can be surprised, but it is also true for Windows Kernel - just familiarize yourself with it's developers point of view.
I wonder, how you reacted to the CIA issue some time ago.
@jmichael2497
after checking the template, i noticed maybe autocorrect typo "the integrality of" > "the integrity of"
That's news for me. I didn't use any auto-correct, but I've always seen the "integrity" rather than the other. According to the dictionary, the two of them are correct.
i'm never really as concerned about "popular"
Very good point about popular standards and great examples. But keep in mind that ZIP packages are important for cases when you are for example on an clean system and need to quickly extract packages using mechanisms built in the operating system.
(probably forgetting others from a 2018 report)
Could you point me to the report from 2018 which you mentioned? I've always looked to the ENISA reports, but the last one is probably from 2014.
Anyway, have you noticed that we are on the probably longest issue - in terms of comments - in the whole project's GitHub history? :)
(probably forgetting others from a 2018 report)
Could you point me to the report from 2018 which you mentioned? I've always looked to the ENISA reports, but the last one is probably from 2014.
Anyway, have you noticed that we are on the probably longest issue - in terms of comments - in the whole project's GitHub history? :)
https://www.keylength.com/en/compare in the bibliography at the bottom see third item
"D5.4 Algorithms, Key Size and Protocols Report (2018)"
http://www.ecrypt.eu.org/csa/documents/D5.4-FinalAlgKeySizeProt.pdf (2018-02)
and yeah i've been hesitant to post from maybe straying off-topic, but sources are good, hehe, here you go, under 150 pages of mind bending information (i understood some of it).
@saelic @bughit
Just added it:
https://github.com/notepad-plus-plus/notepad-plus-plus/blob/master/README.md
You should add the key ID too
But thanks and thanks to all who help
Key ID and key description I would say.
I suggest to make the following changes:
Change the title:
from: Notepad++ GPG Certificate Public Key Fingerprint
to: Notepad++ Release Key
Attach info like:
_Since the release of version 7.6.5 Notepad++ is signed using GPG with the following key:_
Signer: Notepad++
E-mail: don.[email protected]
Key ID: 0x8D84F46E
Key fingerprint: 14BC E436 2749 B2B5 1F8C 7122 6C42 9F1D 8D84 F46E
Key type: RSA 4096/4096
Created: 2019-03-11
Expiries: 2021-03-10
_BTW:_
On the weekend I was watching some security related videos on YouTube and look what I came across: https://youtu.be/qKCEQ8XWks4?t=158
What a coincidence ;)
@saelic
Good suggestion. Done.
On the weekend I was watching some security related videos on YouTube and look what I came across:
Awesome, thanx!
I wish Notepad++ could be in this famous hacking scene of Swordfish:
https://www.youtube.com/watch?v=mWqGJ613M5Y
;)
@beerisgood
Thank you for the suggestion.
Thank you especially for creating this issue.
But, wineisbetter :)
Hello guys, here's the v7.6.5 release note, the announcement regarding the GPG signature part:
From the version 7.6.5 Notepad++ downloadable packages are signed with GnuPG (GNU Privacy Guard). GnuPG is an Open Source alternative to the well-known Pretty Good Privacy (PGP). Most Linux distributions ship with GnuPG installed by default. Under Windows, you can get Gpg4win (https://www.gpg4win.org/) to check authenticity and integrity of Notepad++ packages you download.
To verify the signature for a specific package, you first need to obtain a copy of our public GPG build key:
https://github.com/notepad-plus-plus/notepad-plus-plus/blob/master/README.md#notepad-release-key
Import it to the key store, then download the package and its signature for verifying with imported key.
In the case that you use Gpg4win, you can get Key ID from the above page,
then search the key in the key server via Kleopatra. Once the key has been found from the server and listed, import it into Kleopatra. Now you can download the package you need and its signature.
Double clicked on signature for checking downloaded binary with the imported public key. The result should be displayed in green - if it's in red, your downloaded binary is not authentic.
Please let me know if there are somethings I forgot.
@beerisgood , I see some signature on the key naming your nickname. Is it your signature? Have you met @donho IRL and have you made that person give you a bulletproof proof that he is @donho ?
@KOLANICH Even @beerisgood met me in person, how can he be sure the guy he met IRL is Don HO who maintains this repository?
BTW, how did you see the signatures of my public key?
BTW, how did you see the signatures of my public key?
OK, got it !
I would say it like this:
Since version 7.6.5 of Notepad++, the distributive packages are signed with digital signature. This allows users to reliably validate authenticity and integrity of Notepad++ packages. Software used is GnuPG (GNU Privacy Guard) which is Free Software and Open Source alternative to the well-known PGP (Pretty Good Privacy).
On Windows you can use native GnuPG (https://gnupg.org) which works under the command line, or use Gpg4win (https://www.gpg4win.org) which is based on GnuPG and has a nice GUI. Of course you can also use PGP Desktop, which now days is provided by Symantec.
Most Linux distributions ship with GnuPG installed by default. If you don't have it then install it using package management system present in your distribution.
Release Key
Notepad++ packages and GitHub commits are signed using the Release Key, which has the following characteristics:
Signer: Notepad++
E-mail: don.[email protected]
Key ID: 0x8D84F46E
Key fingerprint: 14BC E436 2749 B2B5 1F8C 7122 6C42 9F1D 8D84 F46E
Key type: RSA 4096/4096
Created: 2019-03-11
Expiries: 2021-03-10
Obtaining and validating Release Key
To make signature verification possible, you need to obtain a copy of our Release Key:
https://github.com/notepad-plus-plus/notepad-plus-plus/blob/master/README.md#notepad-release-key
You should compare it against other copies downloaded from keyserver to minimize the risk of obtaining the malicious key. To do this, you can use one of the following key servers:
http://keys.gnupg.net
https://keyserver.ubuntu.com
https://pgp.mit.edu
https://zimmermann.mayfirst.org
In case of Gpg4win you can also search for key on the key server via Kleopatra. PGP Desktop also has such function.
After making sure that the downloaded key match with the key downloaded from the key server, you can import it to your key store. Double click on the file with the Release Key, validate it's characteristics and make sure that all of them are exactly the same as provided ones. Then sign the Release Key with your private key and set the level of trust which you like.
Validating Digital Signature
To validate the Digital Signature (and thus the file authenticity and integrity) you need to download the signature file for the package you've obtained. Link to the signature file (.sig) is located near the package download link.
After download make sure that both files (i.e. package and .sig file) are located in the same location. Then double click on signature to start validation process.
The result should say that file was signed by
- When using Kleopatra, make sure that label has green background. If it's in red, then the package is tampered or broken and should be deleted immediately.
- When using PGP Desktop, make sure that the result has green check mark. Otherwise get rid of the package.
In case of invalid signature please don't panic, but contact us immediately, because there is a possibility that the malicious file was somehow put on our server. Your response will help us in investigation of the problem and in taking appropriate actions.
@saelic
Wow! That's a very detail quality tutorial.
"Thank you" cannot even express my gratitude!
Believe me that "thank you" in this area of interests is heard very rarely.
Generally nobody knows and cares what I'm talking about.
@KOLANICH Even @beerisgood met me in person, how can he be sure the guy he met IRL is Don HO who maintains this repository?
He might be your friend who have been knowing you personally for a long time. Otherwise putting signatures on other people keys is compromising the Web of trust. When one puts own signature on others public key he pledges that the key belongs to that person. If he cannot pledge it, he shouldn't put own signature on that key.
how can he be sure the guy he met IRL is Don HO who maintains this repository?
Just login to your GitHub account or FTP server of your site and put some string of his will. Eventually you can do this with him staying next to you :)
Otherwise putting signatures on other people keys is compromising the Web of trust.
I must clearly say, that this and the whole @KOLANICH post is critical point.
Just login to your GitHub account or FTP server of your site and put some string of his will. Eventually you can do this with him staying next to you :)
It is not a good proof - an agent backed by a powerful law enforcement agency can do the same, making the services (hoster, github, etc) involved or their emploees to cooperate with a subpoena. For example Australian citizens temporarily working for GH and wishing to return to Australia somewhen may be blackmailed this way (Australia has passed a law in 2018 requiring its citizens and companies to cooperate to their intelligence agencies, including removing security features, inserting backdoors and nondisclosure of the cooperation).
I really like your way of thinking :)
Another suggestion: use different keys for signing packages (Release Key) and for source commits (Development Key). It's common and good practice to use different keys for different things. If you will to do this, then you must repeat the procedure of publishing and describing your new public key.
hi, i did not have much interest in GnuPG until i read @KOLANICH 's concern about @beerisgood named in the notepad++ signature.
this was followed by reading @saelic 's excellent tutorial, which provided enough information to get me from zero knowledge up to date in a few minutes, to check what is seen by any entity or person which follows the tutorial.
a verifying and checking entity will expect don.[email protected] to be the signer.
quote:
The result should say that file was signed by
but the check result will say selfsigned by beerisgood !!!
instead of uid: Notepad++ don.h@free.fr and (self)sig: Notepad++ don.h@free.fr.
for not so humorous corporate people, and anyone who did not follow this github topic, it will look like either the authors like to drink beer while writing security features for notepad++ (which is not the case, as it would then rather say wineisbetter 😉), or ... most probably ... think that notepad++ or the github project site got compromised by someone who likes beer.
full result:
Search results for '0x8d84f46e'
Type bits/keyID cr. time exp time key expir
pub 4096R/8D84F46E 2019-03-11
Fingerprint=14BC E436 2749 B2B5 1F8C 7122 6C42 9F1D 8D84 F46E
uid Notepad++ <[email protected]>
sig sig3 8D84F46E 2019-03-11 __________ 2021-03-11 [selfsig]
sig sig 620F071D 2019-03-21 __________ __________ beerisgood <[email protected]>
sub 4096R/DFABBC55 2019-03-11
sig sbind 8D84F46E 2019-03-11 __________ 2021-03-11 []
@donho will this stay that way for now ?
if it stays that way for now, it would be best to skip any kind of verification tutorial, to minimise the amount of user requests at the issue tracker and the community.
(self protection, as the current community goal is, not to leave a single unanswered question or issue request behind, and, if possible, to answer with satisfaction for the requesting author)
note: i personally would prefer to keep @saelic 's tutorial or similar, and re-sign with donho don.h@free.fr, or Notepad++ don.h@free.fr if possible, or at least any possible name/email combination that doesn't look like a prank.
many thanks and greetings
metachuh
@KOLANICH Even @beerisgood met me in person, how can he be sure the guy he met IRL is Don HO who maintains this repository?
He might be your friend who have been knowing you personally for a long time. Otherwise putting signatures on other people keys is compromising the Web of trust. When one puts own signature on others public key he pledges that the key belongs to that person. If he cannot pledge it, he shouldn't put own signature on that key.
I never met @donho, nor i know about him somehing. I only add my key to his, cause its Web of trust and i trust him
That's the whole point. You add your key if you trust it and this strengh they key(s) itself
@MetaChuh
for not so humorous corporate people, and anyone who did not follow this github topic, it will look like either the authors like to drink beer while writing security features for notepad++
Wine, not beer.
Fact: I drink wine often while I code Notepad++ at home. so no beer, thanks.
full result:
Search results for '0x8d84f46e'
Type bits/keyID cr. time exp time key expir
pub 4096R/8D84F46E 2019-03-11
Fingerprint=14BC E436 2749 B2B5 1F8C 7122 6C42 9F1D 8D84 F46E
uid Notepad++ don.h@free.fr
sig sig3 8D84F46E 2019-03-11 __________ 2021-03-11 [selfsig]
sig sig 620F071D 2019-03-21 __________ __________ beerisgood beerisgood.github@protonmail.com
sub 4096R/DFABBC55 2019-03-11
sig sbind 8D84F46E 2019-03-11 __________ 2021-03-11 []
It's the result of found key information on the key server by providing Notepad++ signature's public key ID. I guess It'll list people's signatures on my public key to show their trust on my private key which is used to sign Notepad++ packages. More signatures, more trust rating on the private key.
but the check result will say selfsigned by beerisgood !!!
instead of uid: Notepad++ don.[email protected] and (self)sig: Notepad++ don.[email protected].
That's the result of verification of signature after double clicking on npp.7.5.5.bin.minimalist.7z.sig :
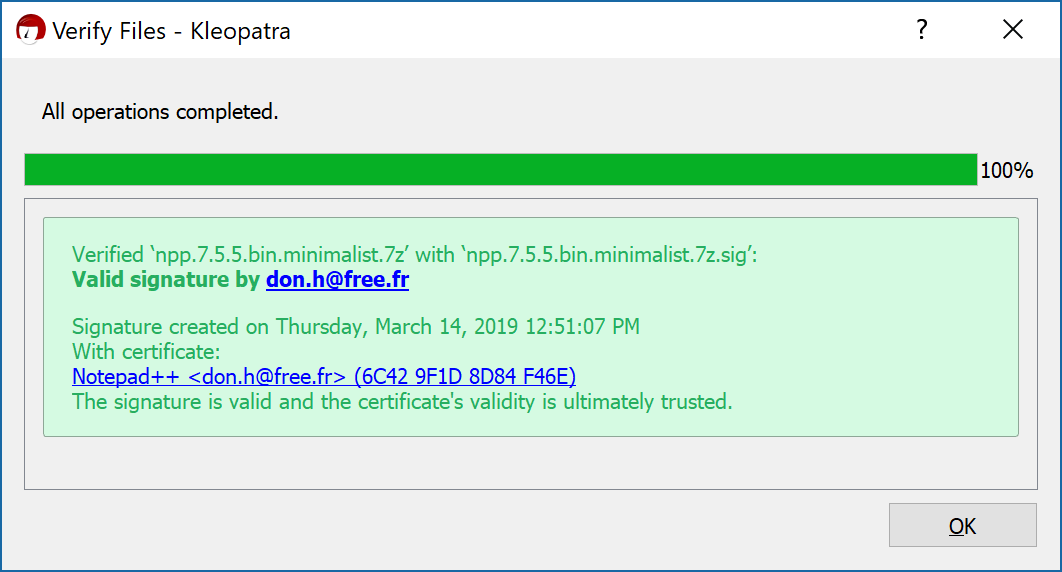
Are you sure we are talking about the same thing?
@MetaChuh I must say that I'm also confused. The result should be exactly as @donho has shown us.
I think that you're talking about countersignatures, which are present under the main key showing who trust this key. We don't have any control of who is signing it. It can be even signed by somebody in .gov domain, because this is the necessary step to make validation possible for this person (as I have pointed in the tutorial). I also signed don.ho key, but not yet synchronized it with key server.
In PGP it also looks fine:
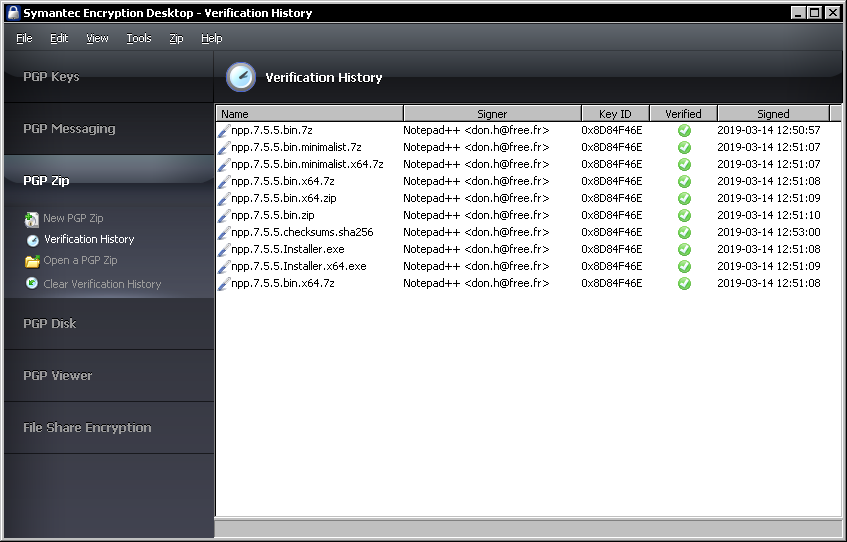
Whole GPG "project" is finished successful, all key infos are available and everything is good.
Thanks to all guys who help to archive this and a big thanks to you, donho.
Also @guys sign donho key with your own to make it stronger and resistant against abusing/ else.
I close this now.
OK @beerisgood I hope you didn't close this issue because you're upset to hear "Wine is better" :)
Anyway, thank you again for making this issue that opens another security enhancement horizon to Notepad++ project.
For people who have talked in this issue, I have created Security category on Notepad++ community:
https://notepad-plus-plus.org/community/category/9/security
You're welcome to post any Notepad++ security issue there.
It's easy to access it, just use your GitHub account then here you go.
I see you guys there.
FYI
Release 7.6.5 is on its way:
https://notepad-plus-plus.org/community/topic/17379/7-6-5-rc2
It'll be released on the 1st April if everything is fine.
I think you should check if the web server has MIME entry for the .sig file, because when I'm downloading them now the browser see them as RAR archive.
Configure web server for the following MIME types:
- application/pgp-encrypted
- application/pgp-signature
- application/pgp-keys
@saelic
because when I'm downloading them now the browser see them as RAR archive.
I have no idea what are you talking about.
I never met @donho, nor i know about him somehing. I only add my key to his, cause its Web of trust and i trust him
That's the whole point. You add your key if you trust it and this strengh they key(s) itself
Couldn't agree more. I feel such system is like blockchain, kind of rating system.
It's for sure that I will never ever go to such "signature party" for 2 reasons -
- Since no one knows me in person, their signatures are meaningless.
- Why should I go to such "club" to ask the contre-signature from ppl I don't know, by knowing the fact that with or without their signatures, I will use my key to sign Notepad++ packages anyway?
@donho I don't know if it's good idea to release a update (with GPG signed now) at 1. April cause April jokes.
Would wait to 2. April
And I also don't close this issue because of you like wine more then beer :D
i know this sounds unreasonable and childish, but i'd somehow love the originally scheduled release to happen, just for the fun of it. 😃
i'm already curious since i first read the date, hence my smiley reaction, and there hasn't been a notepad++ april's fool since 2015, as i can recall.
this would also be the first notepad++ ever released on exactly april 1st (i think v2.9 being the closest, released on 02.04.2005) so everybody could call it a major "done it, been there" project milestone 😉
maybe just a little hidden insider message at the installer or the change.log ? 🙏
or the search and replace panel mirrored, fleeing and scrolling away from the mouse pointer ? 😂
... let the surprises come ...
back on topic:
thanks for the clarification about only the trust chain listing beerisgood.
i guess i got confused because beerisgood is the first and only entry in that list, and members like donho as well as all contributors are absent.
if i see my reaction in a positive way: we now know, more or less, how user requests of other people, with the same zero knowledge about gpg, could eventually look like, and we now have a reference answer for that. 👍
as topics like that are pretty new to notepad++, i'd also appreciate your presence at the community, as you could give us a hand, if security questions are asked. or write basic security tutorials, if you don't enjoy or lack time to support daily user requests.
many thanks and greetings,
metachuh
I have no idea what are you talking about.
The thing is, that when web server (for example Apache) doesn't have specified types of files which he serves by it's extension, then he tries to determine file type by it's content.
For example, when Microsoft introduced the Office XML ("x") file formats in Office 2007 (.docx, .xlsx etc.) then Apache treated them as ZIP archives, because in point of fact - they are ZIP archives with lot's of XML and other files in them. That's why it was neccesary to add the MIME type to the Apache configuration telling him, that those "x" files are not archives, but "simple" document files. It was back in 2006.
Now same thing is true in this case: the .sig files you provide are binary files with unknown extension and no clear format (from the web server's point of view). That's why when user downloads the file, it's type can't be determined and could result in unpredictable type definition.
For better understanding, look at the following screenshot which shows the situation where user is downloading the .sig file. It says that file appears to be an ZIP archive.
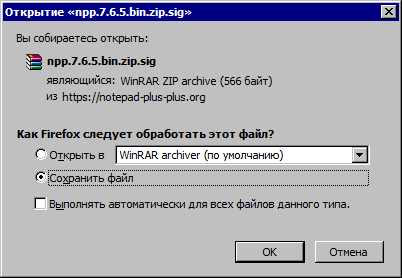
To solve this you need to do one of two things:
- add MIME types to web server's configuration (you can refer to RFC 3156);
- change .sig file format to ASCII.
I don't know if it's good idea to release a update (with GPG signed now) at 1. April cause April jokes. Would wait to 2. April
I agree, with such security changes I would strongly suggest not to release the new version on April 1st.
@beerisgood @saelic
I don't know if it's good idea to release a update (with GPG signed now) at 1. April cause April jokes. Would wait to 2. April
I agree, with such security changes I would strongly suggest not to release the new version on April 1st.
Damn it! Why are you security guy always serious? (Stupid question, but I need to cry it out)
OK, v7.6.5 is just released on 31th March near midnight.
https://notepad-plus-plus.org/news/v7.6.5-with-gpg-signatures.html
or the search and replace panel mirrored, fleeing and scrolling away from the mouse pointer ?
@MetaChuh A "feature" I really want to implement is a Maybe button beside of Yes and No in every dialog of Notepad++. It's too late for this April fools' day, "Maybe" in the next one.
Thank you everybody to make this release happen!
Damn it! Why are you security guy always serious?
Perfectionism, care and military-like mentality - all of which I love :)
After quick checking the release announcement I've noticed, that file https://notepad-plus-plus.org/repository/7.x/7.6.5/npp.7.6.5.checksums.sha256.sig does not exist.
yes, you are correct.
thanks for spotting this so quickly.
it is there, but the .sig file extension is missing.
npp.7.6.5.checksums.sha256 31-Mar-2019 23:47 732
https://notepad-plus-plus.org/repository/7.x/7.6.5/npp.7.6.5.checksums.sha256
After quick checking the release announcement I've noticed, that file file https://notepad-plus-plus.org/repository/7.x/7.6.5/npp.7.6.5.checksums.sha256.sig does not exist.
@saelic
Thank you for checking.
Done.
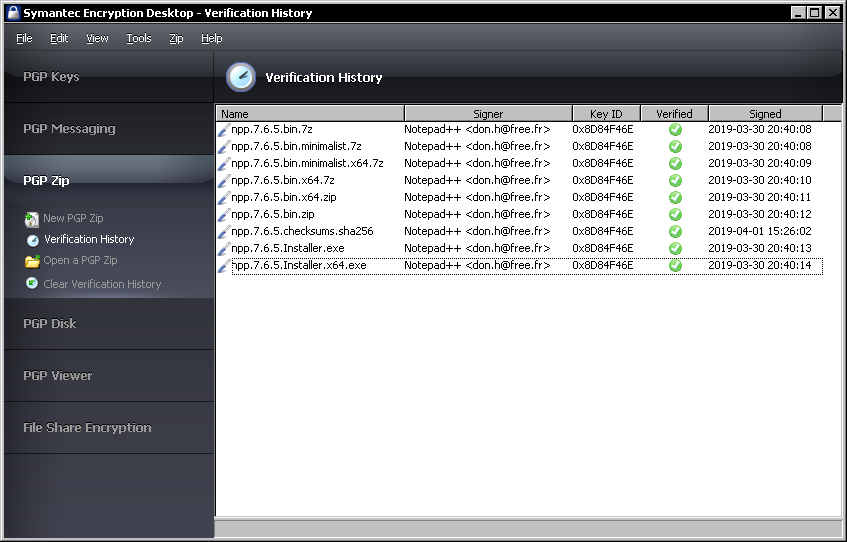
Signatures looks fine:
Another problem: in announcement there is a link to the Release Key (https://github.com/notepad-plus-plus/notepad-plus-plus/blob/master/README.md#notepad-release-key) but under that link there is no key, but only key characteristics. You should upload the public key to GitHub and link to it under the key characteristics (in readme.md).
I would also add a link in announcement, so the result would look like:
To make signature verification possible, you need to obtain a copy of our Release Key:
https://notepad-plus-plus.org/gpg/nppGpgPub.asc
https://github.com/notepad-plus-plus/notepad-plus-plus/blob/master/nppGpgPub.asc
@saelic their is no need to upload the key to GitHub
The key exist on official GPG server
There is, as we were saying:
1 copy on main server;
1 copy on GitHub;
1 copy on key server.
@saelic
Done. I modified the text to make it more explicite.
I'm quite confused:
Both
http://keys.gnupg.net/pks/lookup?op=get&search=0x6C429F1D8D84F46E
&
https://notepad-plus-plus.org/gpg/nppGpgPub.asc
should display the same public key, right? But obviously their contents are not the same.
@donho I don't look (mobile phone) but I guess this is because the key on GPG server include my trust sign and the on on your notepad server doesn't.
But in the end both should work and be the same
@beerisgood
Yes, that makes sense. Thank you!
v7.6.5 has been withdraw?
404 at https://notepad-plus-plus.org/repository/7.x/7.6.5/
@saelic
yes, don has found a major crash issue with session files:
https://notepad-plus-plus.org/community/topic/17395/rolling-back-to-v7-6-4
Ah, OK, thank you for information.
Well it was 1. April release :D
Checksum file, which contained all of the distributive packages, was signed on April 1st, so... payback time ;)
@beerisgood @saelic
The same release note will be in v7.6.6 which is coming out this evening.
That's fine with me. I was just curious what happened,
There is still no file located on GitHub with full public key.
@saelic
Shoul I add nppPublicKey.asc under the root of repository ?
Yes, of course. And link to it in the release announcement and readme.md as I said earlier - see https://github.com/notepad-plus-plus/notepad-plus-plus/issues/2524#issuecomment-478591495.
@saelic
Done. Please let me know if there's something missing.
Thank you
Most helpful comment
The thing is, Don Ho is not even my official name (on my passport). The CN name is hard coded in the source code for the certificate verification of inter-component. And I don't want to people be able to dig my personal info so easily.