Metasploit-framework: db_import not able to import openvas xml data
Steps to reproduce
- Create scan report with OpenVas Version 9 (now called gvm) in XML
- Open msfconsole
- Import XML with
db_import ~/xml_name.xml
Expected behavior
msf5 > db_import rr.xml
[*] Importing 'Openvas XML' data
[*] Importing host 10.0.2.15
[*] Importing host 10.0.2.15
[*] Importing host 10.0.2.15
[*] Importing host 10.0.2.15
[*] Importing host 10.0.2.15
[*] Importing host 10.0.2.15
[*] Successfully imported path/to/test.xm
Current behavior
msf5 > db_import rr.xml
[*] Importing 'OpenVAS XML' data
[*] Import: Parsing with 'Nokogiri v1.10.10'
[-] **Error while running command db_import: Validation failed: Port must be an integer**
Call stack:
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/validations.rb:79:in raise_record_invalid'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/validations.rb:43:in `save!'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/attribute_methods/dirty.rb:29:in `save!'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:291:in `block in save!'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:351:in `block in with_transaction_returning_status'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/database_statements.rb:213:in `block in transaction'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/transaction.rb:184:in `within_new_transaction'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/database_statements.rb:213:in `transaction'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:220:in `transaction'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:348:in `with_transaction_returning_status'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:291:in `save!'
`/usr/share/metasploit-framework/lib/msf/core/db_manager/service.rb:132:in `block in report_service'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord`-4.2.11.3/lib/active_record/connection_adapters/abstract/connection_pool.rb:292:in with_connection'
`/usr/share/metasploit-framework/lib/msf/core/db_manager/service.rb:61:in `report_service'
`/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/service_data_proxy.rb:38:in `block in report_service'
`/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/core.rb:166:in `data_service_operation'
`/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/service_data_proxy.rb:36:in `report_service'
`/usr/share/metasploit-framework/lib/rex/parser/nokogiri_doc_mixin.rb:152:in `db_report'
`/usr/share/metasploit-framework/lib/rex/parser/openvas_nokogiri.rb:179:in `record_service'
`/usr/share/metasploit-framework/lib/rex/parser/openvas_nokogiri.rb:117:in `end_element'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/document.rb:127:in end_element_namespace'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/parser.rb:110:in parse_with'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/parser.rb:110:in parse_memory'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/parser.rb:83:in parse'
`/usr/share/metasploit-framework/lib/msf/core/db_manager/import/open_vas.rb:11:in `import_openvas_noko_stream'
`/usr/share/metasploit-framework/lib/msf/core/db_manager/import/open_vas.rb:22:in `import_openvas_new_xml'
`/usr/share/metasploit-framework/lib/msf/core/db_manager/import.rb:100:in `import'
`/usr/share/metasploit-framework/lib/msf/core/db_manager/import.rb:219:in `import_file'
`/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/db_import_data_proxy.rb:17:in `block in import_file'
`/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/core.rb:166:in `data_service_operation'
`/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/db_import_data_proxy.rb:15:in `import_file'
`/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1464:in `block (3 levels) in cmd_db_import'
`/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1457:in `each'
`/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1457:in `block (2 levels) in cmd_db_import'
`/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1451:in `each'
`/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1451:in `block in cmd_db_import'
`/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/connection_pool.rb:292:in `with_connection'
`/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1446:in `cmd_db_import'
`/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:523:in `run_command'
`/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:474:in `block in run_single'
`/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:468:in `each'
`/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:468:in `run_single'
`/usr/share/metasploit-framework/lib/rex/ui/text/shell.rb:158:in `run'
`/usr/share/metasploit-framework/lib/metasploit/framework/command/console.rb:48:in `start'
`/usr/share/metasploit-framework/lib/metasploit/framework/command/base.rb:82:in `start'
`/usr/bin/msfconsole:23:in `<main>'
Metasploit version
Framework: 5.0.101-dev
Console : 5.0.101-dev
Additional Information
Module/Datastore
The following global/module datastore, and database setup was configured before the issue occurred:
Collapse
[framework/core]
LogLevel=3
[framework/ui/console]
ActiveWorkspace=open
History
The following commands were ran during the session and before this issue occurred:
Collapse
351 workspace -a open
352 hosts
353 set LogLevel 3
354 db_import rr.xml
355 debug
Errors
The following errors occurred before the issue occurred:
Collapse
[09/22/2020 16:09:18] [e(0)] core: Dependency for windows/encrypted_shell_reverse_tcp is not supported
[09/22/2020 16:09:18] [e(0)] core: Dependency for windows/x64/encrypted_shell_reverse_tcp is not supported
[09/22/2020 16:09:18] [e(0)] core: Dependency for windows/x64/encrypted_reverse_tcp is not supported
[09/22/2020 16:09:18] [e(0)] core: Dependency for windows/encrypted_reverse_tcp is not supported
[09/22/2020 16:09:42] [e(0)] core: Problem reporting service - ActiveRecord::RecordInvalid Validation failed: Port must be an integer
[09/22/2020 16:09:42] [e(0)] core: Problem generating DB Import - ActiveRecord::RecordInvalid Validation failed: Port must be an integer
[09/22/2020 21:39:33] [e(0)] core: Problem reporting service - ActiveRecord::RecordInvalid Validation failed: Port must be an integer
[09/22/2020 21:39:33] [e(0)] core: Problem generating DB Import - ActiveRecord::RecordInvalid Validation failed: Port must be an integer
[09/22/2020 21:42:21] [e(0)] core: Problem reporting service - ActiveRecord::RecordInvalid Validation failed: Port must be an integer
Call stack:
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/validations.rb:79:in `raise_record_invalid'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/validations.rb:43:in `save!'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/attribute_methods/dirty.rb:29:in `save!'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:291:in `block in save!'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:351:in `block in with_transaction_returning_status'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/database_statements.rb:213:in `block in transaction'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/transaction.rb:184:in `within_new_transaction'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/database_statements.rb:213:in `transaction'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:220:in `transaction'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:348:in `with_transaction_returning_status'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:291:in `save!'
/usr/share/metasploit-framework/lib/msf/core/db_manager/service.rb:132:in `block in report_service'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/connection_pool.rb:292:in `with_connection'
/usr/share/metasploit-framework/lib/msf/core/db_manager/service.rb:61:in `report_service'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/service_data_proxy.rb:38:in `block in report_service'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/core.rb:166:in `data_service_operation'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/service_data_proxy.rb:36:in `report_service'
/usr/share/metasploit-framework/lib/rex/parser/nokogiri_doc_mixin.rb:152:in `db_report'
/usr/share/metasploit-framework/lib/rex/parser/openvas_nokogiri.rb:179:in `record_service'
/usr/share/metasploit-framework/lib/rex/parser/openvas_nokogiri.rb:117:in `end_element'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/document.rb:127:in `end_element_namespace'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/parser.rb:110:in `parse_with'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/parser.rb:110:in `parse_memory'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/parser.rb:83:in `parse'
/usr/share/metasploit-framework/lib/msf/core/db_manager/import/open_vas.rb:11:in `import_openvas_noko_stream'
/usr/share/metasploit-framework/lib/msf/core/db_manager/import/open_vas.rb:22:in `import_openvas_new_xml'
/usr/share/metasploit-framework/lib/msf/core/db_manager/import.rb:100:in `import'
/usr/share/metasploit-framework/lib/msf/core/db_manager/import.rb:219:in `import_file'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/db_import_data_proxy.rb:17:in `block in import_file'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/core.rb:166:in `data_service_operation'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/db_import_data_proxy.rb:15:in `import_file'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1464:in `block (3 levels) in cmd_db_import'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1457:in `each'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1457:in `block (2 levels) in cmd_db_import'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1451:in `each'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1451:in `block in cmd_db_import'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/connection_pool.rb:292:in `with_connection'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1446:in `cmd_db_import'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:523:in `run_command'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:474:in `block in run_single'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:468:in `each'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:468:in `run_single'
/usr/share/metasploit-framework/lib/rex/ui/text/shell.rb:158:in `run'
/usr/share/metasploit-framework/lib/metasploit/framework/command/console.rb:48:in `start'
/usr/share/metasploit-framework/lib/metasploit/framework/command/base.rb:82:in `start'
/usr/bin/msfconsole:23:in `<main>'
[09/22/2020 21:42:21] [e(0)] core: Problem generating DB Import - ActiveRecord::RecordInvalid Validation failed: Port must be an integer
Call stack:
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/validations.rb:79:in `raise_record_invalid'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/validations.rb:43:in `save!'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/attribute_methods/dirty.rb:29:in `save!'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:291:in `block in save!'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:351:in `block in with_transaction_returning_status'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/database_statements.rb:213:in `block in transaction'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/transaction.rb:184:in `within_new_transaction'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/database_statements.rb:213:in `transaction'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:220:in `transaction'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:348:in `with_transaction_returning_status'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:291:in `save!'
/usr/share/metasploit-framework/lib/msf/core/db_manager/service.rb:132:in `block in report_service'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/connection_pool.rb:292:in `with_connection'
/usr/share/metasploit-framework/lib/msf/core/db_manager/service.rb:61:in `report_service'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/service_data_proxy.rb:38:in `block in report_service'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/core.rb:166:in `data_service_operation'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/service_data_proxy.rb:36:in `report_service'
/usr/share/metasploit-framework/lib/rex/parser/nokogiri_doc_mixin.rb:152:in `db_report'
/usr/share/metasploit-framework/lib/rex/parser/openvas_nokogiri.rb:179:in `record_service'
/usr/share/metasploit-framework/lib/rex/parser/openvas_nokogiri.rb:117:in `end_element'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/document.rb:127:in `end_element_namespace'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/parser.rb:110:in `parse_with'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/parser.rb:110:in `parse_memory'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/parser.rb:83:in `parse'
/usr/share/metasploit-framework/lib/msf/core/db_manager/import/open_vas.rb:11:in `import_openvas_noko_stream'
/usr/share/metasploit-framework/lib/msf/core/db_manager/import/open_vas.rb:22:in `import_openvas_new_xml'
/usr/share/metasploit-framework/lib/msf/core/db_manager/import.rb:100:in `import'
/usr/share/metasploit-framework/lib/msf/core/db_manager/import.rb:219:in `import_file'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/db_import_data_proxy.rb:17:in `block in import_file'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/core.rb:166:in `data_service_operation'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/db_import_data_proxy.rb:15:in `import_file'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1464:in `block (3 levels) in cmd_db_import'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1457:in `each'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1457:in `block (2 levels) in cmd_db_import'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1451:in `each'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1451:in `block in cmd_db_import'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/connection_pool.rb:292:in `with_connection'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1446:in `cmd_db_import'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:523:in `run_command'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:474:in `block in run_single'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:468:in `each'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:468:in `run_single'
/usr/share/metasploit-framework/lib/rex/ui/text/shell.rb:158:in `run'
/usr/share/metasploit-framework/lib/metasploit/framework/command/console.rb:48:in `start'
/usr/share/metasploit-framework/lib/metasploit/framework/command/base.rb:82:in `start'
/usr/bin/msfconsole:23:in `<main>'
Logs
The following logs were recorded before the issue occurred:
Collapse
/usr/share/metasploit-framework/lib/metasploit/framework/command/base.rb:82:in `start'
/usr/bin/msfconsole:23:in `<main>'
[09/22/2020 21:42:21] [e(0)] core: Problem generating DB Import - ActiveRecord::RecordInvalid Validation failed: Port must be an integer
Call stack:
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/validations.rb:79:in `raise_record_invalid'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/validations.rb:43:in `save!'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/attribute_methods/dirty.rb:29:in `save!'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:291:in `block in save!'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:351:in `block in with_transaction_returning_status'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/database_statements.rb:213:in `block in transaction'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/transaction.rb:184:in `within_new_transaction'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/database_statements.rb:213:in `transaction'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:220:in `transaction'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:348:in `with_transaction_returning_status'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/transactions.rb:291:in `save!'
/usr/share/metasploit-framework/lib/msf/core/db_manager/service.rb:132:in `block in report_service'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/connection_pool.rb:292:in `with_connection'
/usr/share/metasploit-framework/lib/msf/core/db_manager/service.rb:61:in `report_service'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/service_data_proxy.rb:38:in `block in report_service'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/core.rb:166:in `data_service_operation'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/service_data_proxy.rb:36:in `report_service'
/usr/share/metasploit-framework/lib/rex/parser/nokogiri_doc_mixin.rb:152:in `db_report'
/usr/share/metasploit-framework/lib/rex/parser/openvas_nokogiri.rb:179:in `record_service'
/usr/share/metasploit-framework/lib/rex/parser/openvas_nokogiri.rb:117:in `end_element'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/document.rb:127:in `end_element_namespace'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/parser.rb:110:in `parse_with'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/parser.rb:110:in `parse_memory'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/nokogiri-1.10.10/lib/nokogiri/xml/sax/parser.rb:83:in `parse'
/usr/share/metasploit-framework/lib/msf/core/db_manager/import/open_vas.rb:11:in `import_openvas_noko_stream'
/usr/share/metasploit-framework/lib/msf/core/db_manager/import/open_vas.rb:22:in `import_openvas_new_xml'
/usr/share/metasploit-framework/lib/msf/core/db_manager/import.rb:100:in `import'
/usr/share/metasploit-framework/lib/msf/core/db_manager/import.rb:219:in `import_file'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/db_import_data_proxy.rb:17:in `block in import_file'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/core.rb:166:in `data_service_operation'
/usr/share/metasploit-framework/lib/metasploit/framework/data_service/proxy/db_import_data_proxy.rb:15:in `import_file'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1464:in `block (3 levels) in cmd_db_import'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1457:in `each'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1457:in `block (2 levels) in cmd_db_import'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1451:in `each'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1451:in `block in cmd_db_import'
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/activerecord-4.2.11.3/lib/active_record/connection_adapters/abstract/connection_pool.rb:292:in `with_connection'
/usr/share/metasploit-framework/lib/msf/ui/console/command_dispatcher/db.rb:1446:in `cmd_db_import'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:523:in `run_command'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:474:in `block in run_single'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:468:in `each'
/usr/share/metasploit-framework/lib/rex/ui/text/dispatcher_shell.rb:468:in `run_single'
/usr/share/metasploit-framework/lib/rex/ui/text/shell.rb:158:in `run'
/usr/share/metasploit-framework/lib/metasploit/framework/command/console.rb:48:in `start'
/usr/share/metasploit-framework/lib/metasploit/framework/command/base.rb:82:in `start'
/usr/bin/msfconsole:23:in `<main>'
Version/Install
The versions and install method of your Metasploit setup:
Collapse
Framework: 5.0.101-dev
Ruby: ruby 2.7.1p83 (2020-03-31 revision a0c7c23c9c) [x86_64-linux-gnu]
Install Root: /usr/share/metasploit-framework
Session Type: Connected to msf. Connection type: postgresql. Connection name: #<Msf::DBManager:0x0000557c1eeef530>.
Install Method: Other - Please specify
All 8 comments
@mjrdon Thanks for the error report; It would be great if you attached the xml_name.xml for us to use as sample data to replicate and fix this issue
I've tried replicating this issue with no luck, I tried using an XML export from gvm-start and it imported successfully:
> db_import ~/Downloads/report-c3ea0dde-3dba-4403-8a49-298fea5bb4f1.xml
[*] Importing 'OpenVAS XML' data
[*] Import: Parsing with 'Nokogiri v1.10.10'
[*] Successfully imported /home/kali/Downloads/report-c3ea0dde-3dba-4403-8a49-298fea5bb4f1.xml
For visibility, I exported the report as XML from the gvm UI:
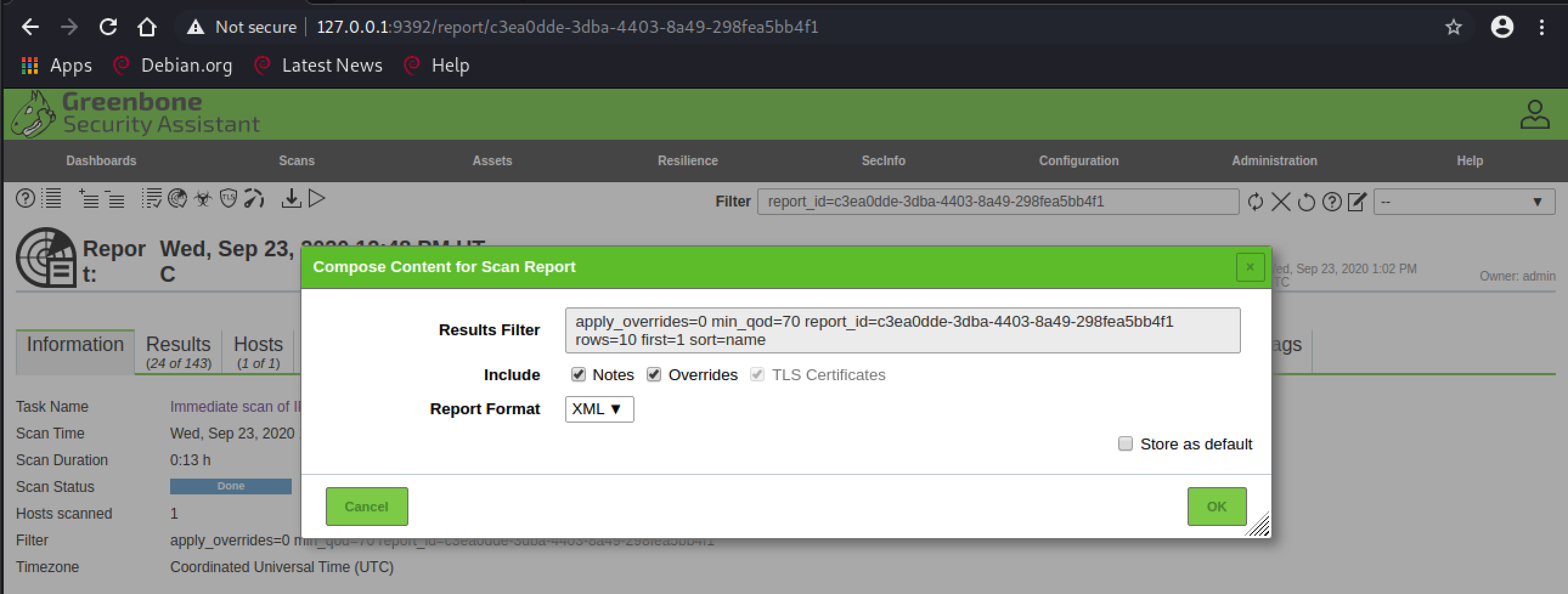
To help debug and fix this issue, please let me know how you exported your XML - and attaching the XML output would also help :+1:
@adfoster-r7 thanks for the help. Just to clarify, I am using GVM 11 (OpenVAS 9), but I used the command line gvm-cli to produce the xml report. I'm assuming this is because db_import is parsing the xml based on the deprecated OpenVAS 7. Anways, my xml command was as follows:
<get_reports report_id='${report_id}' filter='levels=hml' details='1' ignore_pagination='1' />" > ~/rr.xml
The returned xml was too long to paste here, so please look here:
https://paste.ee/p/49dPu
@mjrdon Thanks for the example import file - the bug should be fixed in the next release of Metasploit :+1:
Pull request: https://github.com/rapid7/metasploit-framework/pull/14200
@adfoster-r7 Great, thanks! Just curious since I haven't applied the fix yet: does vulns display anything on the data?
@mjrdon It does indeed:
msf6 exploit(multi/handler) > vulns
Vulnerabilities
===============
Timestamp Host Name References
--------- ---- ---- ----------
2020-09-29 16:32:27 UTC 10.0.2.4 Anonymous FTP Login Reporting
2020-09-29 16:32:27 UTC 10.0.2.4 Apache HTTP Server 'httpOnly' Cookie Information Disclosure Vulnerability
2020-09-29 16:32:27 UTC 10.0.2.4 Apache Tomcat AJP RCE Vulnerability (Ghostcat)
2020-09-29 16:32:27 UTC 10.0.2.4 awiki Multiple Local File Include Vulnerabilities
2020-09-29 16:32:27 UTC 10.0.2.4 Check for Backdoor in UnrealIRCd
2020-09-29 16:32:27 UTC 10.0.2.4 Cleartext Transmission of Sensitive Information via HTTP
2020-09-29 16:32:27 UTC 10.0.2.4 DistCC Remote Code Execution Vulnerability
2020-09-29 16:32:27 UTC 10.0.2.4 Distributed Ruby (dRuby/DRb) Multiple Remote Code Execution Vulnerabilities
2020-09-29 16:32:27 UTC 10.0.2.4 /doc directory browsable
2020-09-29 16:32:27 UTC 10.0.2.4 FTP Unencrypted Cleartext Login
2020-09-29 16:32:27 UTC 10.0.2.4 HTTP Debugging Methods (TRACE/TRACK) Enabled
2020-09-29 16:32:27 UTC 10.0.2.4 source_name
2020-09-29 16:32:27 UTC 10.0.2.4 PHP-CGI-based setups vulnerability when parsing query string parameters from php files.
2020-09-29 16:32:27 UTC 10.0.2.4 phpinfo() output Reporting
2020-09-29 16:32:27 UTC 10.0.2.4 Possible Backdoor: Ingreslock
2020-09-29 16:32:27 UTC 10.0.2.4 source_name
2020-09-29 16:32:27 UTC 10.0.2.4 SSH Weak Encryption Algorithms Supported
2020-09-29 16:32:27 UTC 10.0.2.4 SSH Weak MAC Algorithms Supported
2020-09-29 16:32:27 UTC 10.0.2.4 SSL/TLS: Certificate Expired
2020-09-29 16:32:27 UTC 10.0.2.4 SSL/TLS: Certificate Signed Using A Weak Signature Algorithm
2020-09-29 16:32:27 UTC 10.0.2.4 SSL/TLS: Deprecated SSLv2 and SSLv3 Protocol Detection
2020-09-29 16:32:27 UTC 10.0.2.4 SSL/TLS: Diffie-Hellman Key Exchange Insufficient DH Group Strength Vulnerability
2020-09-29 16:32:27 UTC 10.0.2.4 SSL/TLS: OpenSSL CCS Man in the Middle Security Bypass Vulnerability
2020-09-29 16:32:27 UTC 10.0.2.4 SSL/TLS: Report Weak Cipher Suites
2020-09-29 16:32:27 UTC 10.0.2.4 SSL/TLS: SSLv3 Protocol CBC Cipher Suites Information Disclosure Vulnerability (POODLE)
2020-09-29 16:32:27 UTC 10.0.2.4 TCP timestamps
2020-09-29 16:32:27 UTC 10.0.2.4 Test HTTP dangerous methods
2020-09-29 16:32:28 UTC 10.0.2.4 VNC Brute Force Login
2020-09-29 16:32:28 UTC 10.0.2.4 VNC Server Unencrypted Data Transmission
2020-09-29 16:32:28 UTC 10.0.2.4 vsftpd Compromised Source Packages Backdoor Vulnerability
2020-09-29 16:32:28 UTC 10.0.2.4 vsftpd Compromised Source Packages Backdoor Vulnerability
Does that look as expected?
Indeed it does, thanks!
Some of the vulns have respective CVEs in a <ref type:cve> tag. It would be a nice feature to add those to the 'References' column if possible at some point.
@mjrdon That's a good idea! If you create a feature request issue and reference this issue it's something that could be picked up by the community 👀