Metasploit-framework: NoMethodError in exploit/windows/http/efs_fmsw_userid_bof
Steps to reproduce
- use exploit/windows/http/efs_fmsw_userid_bof
- set RHOSTS
- set RPORT
- run
This section should also tell us any relevant information about the
environment; for example, if an exploit that used to work is failing,
tell us the victim operating system and service versions.
Current behavior
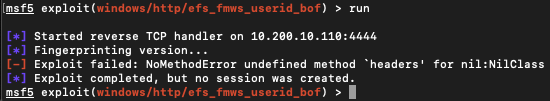
I get "[-] Exploit failed: NoMethodError undefined method `headers' for nil:NilClass" as shown in the picture at the top of the post...
System stuff
Metasploit version
5.0.68
I installed Metasploit with:
- Nightly Installer
OS
MacOS Catalina 10.15.2
All 5 comments
It looks like the get_version method fails to account for res.nil? in the event that the connection fails.
Are you sure that port 80 on the remote host is open?
def get_version
#
# NOTE: Version 5.3 still reports "4.0" in the "Server" header
#
version = nil
res = send_request_raw({'uri' => '/whatsnew.txt'})
if res && res.body =~ /What's new in Easy File Management Web Server V(\d\.\d)/
version = $1
vprint_status "Found version: #{version}"
elsif res.headers['server'] =~ /Easy File Management Web Server v(4\.0)/
version = $1
vprint_status "Based on Server header: #{version}"
end
version
end
Sorry, the port I actually used was 8080 and I am sure it is open because I ran nmap on that machine. It's a pentesting network set up at our university.
Sorry, the port I actually used was 8080 and I am sure it is open because I ran nmap on that machine. It's a pentesting network set up at our university.
Please try with set HTTPTRACE true and set VERBOSE true for debug output.
There is a bug here, but you shouldn't be hitting it if the server is responding with HTTP headers (which you would expect for a HTTP server...)
Oh, God, I... I just reverted the virtual machine on which the server was running and it suddenly worked. I apologize for bothering you, can';t believe i didn't think of this earlier.. :( Still, if you say there is a bug ( and I guess it's the fact that the 'elseif' in the snippet you provided does not check for nil), maybe it was not useless after all.
Thank you.
maybe it was not useless after all.
Yeah there's definitely a bug. Thanks. I'll take a look into it later.
Most helpful comment
Oh, God, I... I just reverted the virtual machine on which the server was running and it suddenly worked. I apologize for bothering you, can';t believe i didn't think of this earlier.. :( Still, if you say there is a bug ( and I guess it's the fact that the 'elseif' in the snippet you provided does not check for nil), maybe it was not useless after all.
Thank you.