Magento2: Paypal Module Secure Token Controller Not Properly Validating Requests
Preconditions (*)
- Magento 2.2.7 Community Edition
- PayPal payment method is set up ( I tested specifically with PayFlow Pro but I suspect any PayPal payment method will be effected)
Steps to reproduce (*)
- As a guest navigate to domain.com/paypal/transparent/requestSecureToken/
- Notice that a PayPal secure token is returned as often as you request it, even if you don't have a current quote in your session.
Expected result (*)
- The controller should return the error result when you don't have an existing quote in your session.

Actual result (*)
- A secure token is returned.
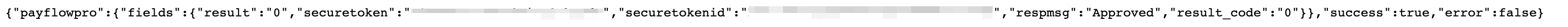
All 12 comments
Hi @prestonchoate. Thank you for your report.
To help us process this issue please make sure that you provided the following information:
- [ ] Summary of the issue
- [ ] Information on your environment
- [ ] Steps to reproduce
- [ ] Expected and actual results
Please make sure that the issue is reproducible on the vanilla Magento instance following Steps to reproduce. To deploy vanilla Magento instance on our environment, please, add a comment to the issue:
@magento-engcom-team give me 2.3-develop instance - upcoming 2.3.x release
For more details, please, review the Magento Contributor Assistant documentation.
@prestonchoate do you confirm that you was able to reproduce the issue on vanilla Magento instance following steps to reproduce?
- [ ] yes
- [ ] no
It appears that the \Magento\Paypal\Controller\Transparent\RequestSecureToken::execute method retrieves the $quote object from Magento\Framework\Session\SessionManager. In this instance it is actually getting \Magento\Checkout\Model\Session. The \Magento\Checkout\Model\Session::getQuote function will create a brand new quote object if one does not exist which means that the error checking for the quote at vendor/magento/module-paypal/Controller/Transparent/RequestSecureToken.php:85 will always return true. If you add a check for !$quote->getId() to that line it should ensure, at the very least, that an actual quote object exists for the session before handing out secure tokens.
@magento-engcom-team This is reproducible on a vanilla Magento install.
Hi @engcom-backlog-nazar. Thank you for working on this issue.
In order to make sure that issue has enough information and ready for development, please read and check the following instruction: :point_down:
- [ ] 1. Verify that issue has all the required information. (Preconditions, Steps to reproduce, Expected result, Actual result).
Details
If the issue has a valid description, the labelIssue: Format is validwill be added to the issue automatically. Please, edit issue description if needed, until labelIssue: Format is validappears.
[ ] 2. Verify that issue has a meaningful description and provides enough information to reproduce the issue. If the report is valid, add
Issue: Clear Descriptionlabel to the issue by yourself.[ ] 3. Add
Component: XXXXXlabel(s) to the ticket, indicating the components it may be related to.[ ] 4. Verify that the issue is reproducible on
2.3-developbranchDetails
- Add the comment@magento-engcom-team give me 2.3-develop instanceto deploy test instance on Magento infrastructure.
- If the issue is reproducible on2.3-developbranch, please, add the labelReproduced on 2.3.x.
- If the issue is not reproducible, add your comment that issue is not reproducible and close the issue and _stop verification process here_!
[ ] 5. Verify that the issue is reproducible on
2.2-developbranch.Details
- Add the comment@magento-engcom-team give me 2.2-develop instanceto deploy test instance on Magento infrastructure.
- If the issue is reproducible on2.2-developbranch, please add the labelReproduced on 2.2.x_Next steps are available in case you are a member of Community Maintainers._
[ ] 6. Add label
Issue: Confirmedonce verification is complete.[ ] 7. Make sure that automatic system confirms that report has been added to the backlog.
Hi @prestonchoate thank you for you report, this issue has already fixed in 2.2-develop and 2.3-develop branch
@engcom-backlog-nazar Do you have the specific commits that addressed this issue or did you just notice that the same behavior doesn't occur in the 2.2.devlop branch?
@prestonchoate i just check that this is not occur in the 2.2.develop branch
I copied the entire paypal module code from the 2.2-develop branch, flushed cache, ran setup-upgrade, di-compile, and deployed static content..... the issue is still happening. I am still getting hit with $0 auth attacks.
I don't think the issue is fixed in the 2.2-develop branch as indicated.
@AndyJAllen It didn't look like the code had changed at all in 2.2-develop, so I definitely think it's reproducible there. As a quick workaround you should be able to change the conditional on vendor/magento/module-paypal/Controller/Transparent/RequestSecureToken line 85 from
if (!$quote or !$quote instanceof Quote) {
To
if (!$quote or !$quote instanceof Quote or !$quote->getId()) {
You could probably expand that to make sure the quote has items before granting the secure token.
Hi preston,
Thanks for the response and attempt to help, however your code change did not work for me. Was there anything else you changed besides that line?
-Andy
@AndyJAllen No that was the only change I made. If you find other things that needed to be fixed for you please share the details!
The CSRF token validation was added to the controller https://github.com/magento/magento2/blob/2.2-develop/app/code/Magento/Paypal/Controller/Transparent/RequestSecureToken.php#L99, but it reduces vectors of attacks. To solve this issue, you need to install magento/module-paypal-captcha OR magento/module-paypal-recaptcha extension which provide Captcha mechanism for Payflow Pro payment form.
Most helpful comment
@AndyJAllen It didn't look like the code had changed at all in 2.2-develop, so I definitely think it's reproducible there. As a quick workaround you should be able to change the conditional on vendor/magento/module-paypal/Controller/Transparent/RequestSecureToken line 85 from
To
You could probably expand that to make sure the quote has items before granting the secure token.