Keepassxc: VirusTotal says code signature for KeePassXC-2.3.4.dmg is invalid
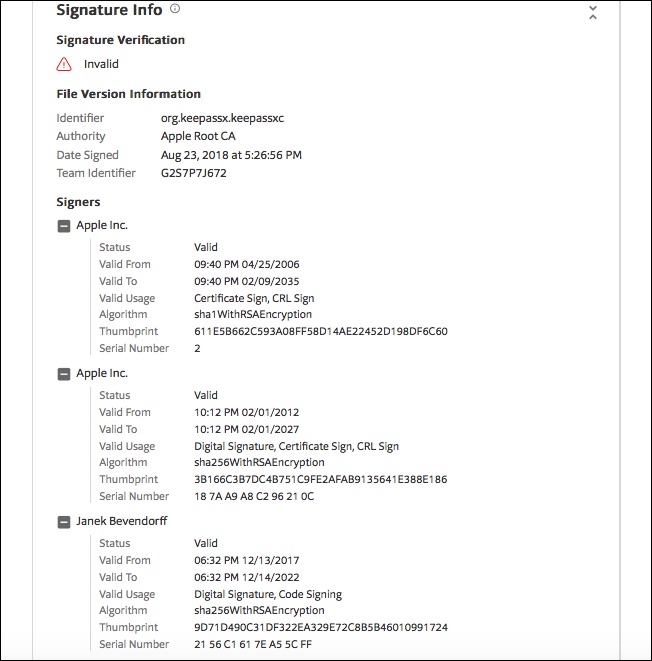
This probably is not a huge issue, but VirusTotal indicates that the Apple Developer ID code signature (also known as Gatekeeper) for the macOS KeePassXC 2.3.4 release is "Invalid."
The app signature seems to verify ok on an actual macOS 10.12.6 system using codesign -vv and codesign codesign -dv --verbose=4
Expected Behavior
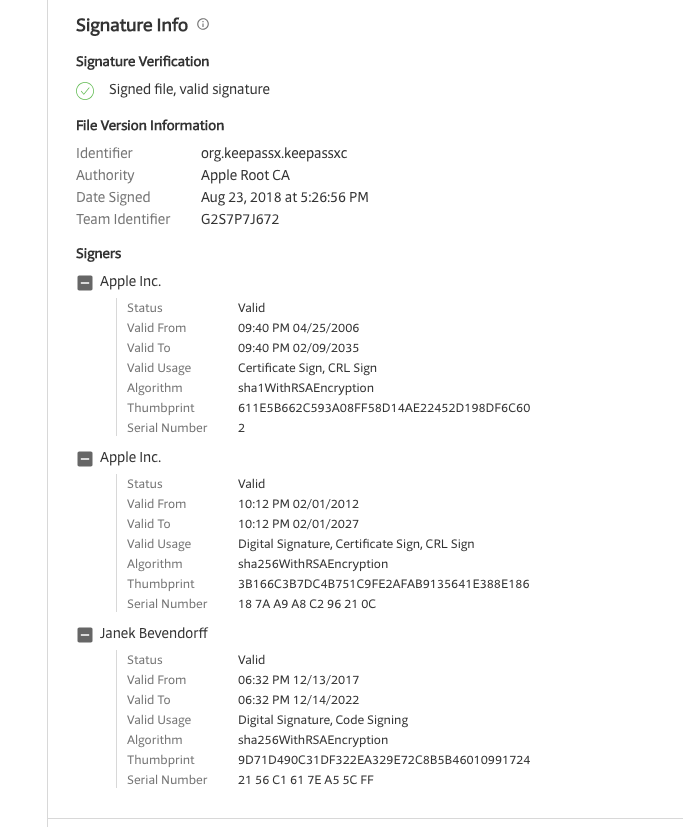
Signature verification by VirusTotal should be "Signed file, valid signature" as is the case for previous releases of KeePassXC such as 2.3.3:
https://www.virustotal.com/#/file/1219dd686aee2549ef8fe688aeef22e85272a8ccbefdbbb64c0e5601db17fbdb/details
Current Behavior
VirusTotal reports the Signature as "Invalid."
See attached screengrab of VT "Signature Info" for KeePassXC-2.3.4.dmg
Possible Solution
I'm not really sure. Maybe the VT signature parser is just being weird with respect to this file.
Steps to Reproduce (for bugs)
Submit the KeePassXC-2.3.4.dmg file to VirusTotal.com.
In the 'Details' pane view the 'Signature Info"
or view direct link to the VT info:
https://www.virustotal.com/#/file/59d7530625866c3d7d5cfa753e12dee0f052f79e1a7572f8e5633ad915369228/details
Context
This issue has made me feel somewhat unsure that the KeePassXC-2.3.4.dmg release is authentic and unmodified and signed by a currently valid Apple Developer ID.
All 9 comments
First off, Virus Total is a third-party to Apple and not in any way shape or form an authoritative source, in my opinion.
With that said, the DMG was built and uploaded by our maintainer @phoerious who owns the Apple ID key. If Apple's codesign marks it valid than it is valid.
As you can see, all signatures are marked valid in the virus total report.
My understanding is that the various file attributes displayed by VirusTotal are not derived from the participating AV engines. So, the issue of a false positive is not relevant to the code sign results.
So, I think concerns about the 'authoritativeness' of VirusTotal are misplaced in this context.
the DMG was built and uploaded by our maintainer @phoerious who owns the Apple ID key.
I believe you. But I shouldn't need to. This is exactly the situation that code signing was designed to prove conclusively. Is the item in question signed by the person indicated and is it in the same condition it was in when it was signed. Apple's tool says yes to both while VT's tool seems to say yes to the first and no to the second, although it is hard to tell exactly what aspect of the code signature it is claiming is 'Invalid.'
I would guess its the same problem as #1671 and entirely Apple's fault.
BTW when I go to Virus Total using the link you provided, it says valid.
BTW when I go to Virus Total using the link you provided, it says valid.
I linked to the VT info for KeePassXC-2.3.3.dmg (the previous release) in the Expected Behavior section of my original message.
The link to the VT info showing the code signature as "Invalid' for KeePassXC-2.3.4.dmg (the current release) is in the "Steps to reproduce" section.
It was a bug in VirusTotal, that is now fixed.
See told you..
It was a bug in VirusTotal, that is now fixed.
Thanks @karlhiramoto @VirusTotal !
Can you tell us a bit more about the VT code sign parser for macOS files?
I think I've noticed that if a file submission contains more than one executable that VT seems to pick one at random to display code sign details. Is this something that might possibly be addressed in the future?
@gretraholisi I'd love to continue the discussion on improving VT. I'd rather do it via email, rather than the keypass github :-) Can you please send some examples, of your use case to [email protected] ? If you address it to me, someone on the team will assign the email to me. I can then take a look at what occurs in the particular case.
In general we try and display for example whatever codesign -dvvv example.app would show
Most helpful comment
See told you..