Identityserver4: Exception: Correlation failed. When building own authorization url.
I've tried to google the correlation error but just can't seem to find an answer that fits my use case.
So I'm building my own authorize url like this:
https://localhost:44359/connect/authorize/callback?client_id=mvc&redirect_uri=https%3A%2F%2Flocalhost%3A44333%2Fsignin-oidc&scope=openid%20profile%20**custom_scope**&response_type=id_token%20code&response_mode=form_post&nonce=xyz
My custom_scope will be displayed in the consent page but when I press on the allow button I get the correlation error. I've tried to remove the custom_scope but I still get the same error after the consent page.
I've compared it to the authorize url that the qucikstart identityserver4 samples generates when pressing on the _Secure_ button:
https://localhost:44359/connect/authorize/callback?client_id=mvc&redirect_uri=https%3A%2F%2Flocalhost%3A44333%2Fsignin-oidc&scope=openid%20profile%20offline_access&response_type=code%20id_token&response_mode=form_post&nonce=636778722636587877.ZTczYjY5NDQtYjFiOC00ODQ5LTk4YWUtNTRmNTRlYTU5NTU4MzZiNGMzZDUtMDFhNy00OGI1LWI2YjItYWY4ZWIyMzQ1YmY3&state=CfDJ8JNTJYpahO5PkQSG8ENRghjERX48NX1Qbwoa_GJzBAcmmGDhfK6dozZDmcULO1gtcaBO7WcJrYIJIW8BRo3LdhZP29j_hkpHq29lW0j51DaSDCz-Kq4WvdLOJoG3pHfjmMhHckKzkTbJxeYWn8CSe5GkbSJKgAiOwJTowVhDF4aAMdbPzp04ilB_dghQiwfxkkydFHIfvkgV5aosS5NPMVO6JRaDAzBPpdltEdLFumqJfYRPaAuFfsxaQCgVI10NDJzQNFnYq6VZ0-05m7Nb7eBaGN3g3zI0o0wilRqE8jihW0IzGSj_wfUHHfS3eRbhgXzib2ICqAZHkS-a_RcR0ek&x-client-SKU=ID_NET&x-client-ver=2.1.4.0
What I can see is that the url is exactly the same except for the custom scope im adding and the nounce.
What am I doing wrong?
All 22 comments
Check your logs for any errors or info that might help.
Does this count as logs?
System.Exception: Correlation failed.
at Microsoft.AspNetCore.Authentication.RemoteAuthenticationHandler`1.HandleRequestAsync()
at Microsoft.AspNetCore.Authentication.AuthenticationMiddleware.Invoke(HttpContext context)
at Microsoft.AspNetCore.Diagnostics.DeveloperExceptionPageMiddleware.Invoke(HttpContext context)
I'm trying to figure out what im missing so I used a clean 5_HybridFlowAuthenticationWithApiAccess project.
And when entering: http://localhost:5010/signin-oidc I'm getting the "Correlation failed" error. In this case what is causing this? Is it the missing cookies?
ConfigureService of 5_HybridFlowAuthenticationWithApiAccess
JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Clear();
services.AddAuthentication(options =>
{
options.DefaultScheme = "Cookies";
options.DefaultChallengeScheme = "oidc";
})
.AddCookie("Cookies")
.AddOpenIdConnect("oidc", options =>
{
options.SignInScheme = "Cookies";
options.Authority = "http://localhost:5000";
options.RequireHttpsMetadata = false;
options.ClientId = "mvc";
options.ClientSecret = "secret";
options.ResponseType = "code id_token";
options.SaveTokens = true;
options.GetClaimsFromUserInfoEndpoint = true;
options.Scope.Add("api1");
options.Scope.Add("offline_access");
options.ClaimActions.MapJsonKey("website", "website");
});
Also between my client - IdentityServer4 I've noticed now that after the consent screen. IdentityServer4 redirects to:
https://localhost:44359/connect/authorize/callback?client_id=ttp1&scope=openid profile offline_access custom_scope1 custom_scope2&response_type=id_token code&redirect_uri=https://localhost:44333/signin-oidc&response_mode=form_post&nonce=xyz
And then:
https://localhost:44333/signin-oidc when the error happens.
Is that correct?
So you are doing a manual authorize request - and but use the MS OIDC handler process the response. Yes absolutely, this will complain about correlation.
The MS handler sets a special cookie that it expects to be present on the callback.
I would recommend you are using the MS handler in both directions.
I do a manual authorize request because I can't add all my scopes Im requesting in my client in the Startup of the client. Is there a way to add scopes to use for the authorization except for the startup?
public void ConfigureServices(IServiceCollection services)
{
services.AddMvc();
JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Clear();
services.AddAuthentication(options =>
{
options.DefaultScheme = "Cookies";
options.DefaultChallengeScheme = "oidc";
})
.AddCookie("Cookies")
.AddOpenIdConnect("oidc", options =>
{
options.SignInScheme = "Cookies";
options.Authority = "https://localhost:44359";
options.ClientId = "tpp1";
options.ClientSecret = "secret";
options.ResponseType = "code id_token";
options.SaveTokens = true;
options.GetClaimsFromUserInfoEndpoint = true;
options.Scope.Add("openid");
options.Scope.Add("profile");
options.Scope.Add("offline_access");
/*
options.Scope.Add("custom_scope_but_now_known_yet_1");
options.Scope.Add("custom_scope_but_now_known_yet_2");
*/
});
}
I want these scopes:
options.Scope.Add("custom_scope_but_now_known_yet_1");
options.Scope.Add("custom_scope_but_now_known_yet_2");
to be added before the authorize request happens.
You can pass additional information in the AuthenticationProperties when you call Challenge on the authN handler. You can then parse that data in the OnRedirectingToIdentityProvider event and amend the protocol message.
I just check the AuthenticationProperties class and I can't figure out where to pass scopes?
There's a items dictionary.
Do you have an example on how to use the AuthenticationProperties in the OnRedirectingToIdentityProvider event?
no. But it is on the context they pass into the event.
I tried something like this now:
But I can't find the scope I added in the dictionary.
[Authorize]
public IActionResult Secure()
{
var dict = new Dictionary<string, string>()
{
{ "scope", "custom_scope_but_now_known_yet_1" }
};
var props = new AuthenticationProperties(dict)
{
RedirectUri = "Home/Secure"
};
return Challenge(props, "oidc");
}
Inside the OnRedirectToIdentityProvider examining the context object:
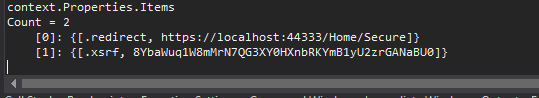
EDIT: I figured it out. I removed the [Authorize] attribute from the action.
No - set the Items property instead.
I can't set the ITems property, its read only. I've to add it as a parameter in the constructor of the AuthenticationProperties.
I've the code like this now:
In the Action:
public IActionResult Secure()
{
var props = new AuthenticationProperties(dict);
return Challenge(props, "oidc");
}
Startup:
options.Events = new OpenIdConnectEvents
{
OnRedirectToIdentityProvider = context =>
{
var scopes = "openid profile offline_access";
foreach (var key in context.Properties.Items.Keys)
{
if (key.Contains("custom_scope."))
{
scopes += $" {key}";
}
}
context.ProtocolMessage.SetParameter("scope", scopes);
return Task.CompletedTask;
}
};
Everything works great I get the correct authorize request and the custom_scopes are there. Accepting the consent as a user also gives me an update in the [PersistedGrants] table with the right consents.
But when redirecting back to the client I get the error message: ArgumentException: An item with the same key has already been added. Key: OpenIdConnect.Code.RedirectUri. What am I missing?
Sorry, don't know. Maybe ask on the Microsoft issue tracker since it is their code.
Rewrote some code, now its all working as intended. Thanks!
I want to know how it is solved.
Hi @PresidentCamacho , Can you post the solution here? Thanks.
@AutismPatient @yasin-uohyd
Are you getting the Correlation failed?
Yes,It indicates that the association failed, which is in an unknown position
Hi@PresidentCamacho , Yes, we still facing this issue only while running web test.
This thread has been automatically locked since there has not been any recent activity after it was closed. Please open a new issue for related bugs.
Most helpful comment
I want to know how it is solved.