Go-ethereum: Node auto send a lot of transaction after call eth.sendTransaction() in one time
Node auto send a lot of transaction after call eth.sendTransaction() in one time
System information
Geth version: 1.8.7-stable
OS & Version: Linux
Commit hash : (if develop)
Steps to reproduce the behaviour
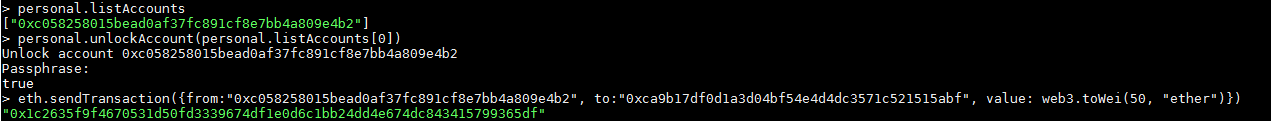
eth.sendTransaction({from:"0xc058258015bead0af37fc891cf8e7bb4a809e4b2", to:"0xca9b17df0d1a3d04bf54e4d4dc3571c521515abf", value: web3.toWei(50, "ether")})
Backtrace
- I send a transaction in one time :
- After i send a transaction , node submitted the original transaction , but it appear a lot of strange transaction that i never send it:

- And this strange behavior of node , will result the sender account decrease a lot of ETH:
(Originaly balance of sender account have 1510.0483 ether , it only send 50 ether to other account , but the balance of sender account only have 5 when it send the 50 ether transaction)

All 7 comments
Did you open the HTTP/WebSocket interface for the whole internet to access? There are people actively scanning for Ethereum nodes, connecting to them and trying to send out funds from them. If you opened your machine for the entire world, someone will actively try to exploit it when you unlock your account.
And here's the proof: your recipient account on:
- Rinkeby: https://rinkeby.etherscan.io/address/0x7097f41f1c1847d52407c629d0e0ae0fdd24fd58
- Ropsten: https://ropsten.etherscan.io/address/0x7097f41F1C1847D52407C629d0E0ae0fDD24fd58
- Kovan: https://kovan.etherscan.io/address/0x7097f41F1C1847D52407C629d0E0ae0fDD24fd58
- Mainnet: https://etherscan.io/address/0x7097f41F1C1847D52407C629d0E0ae0fDD24fd58
Please never open your API ports to the whole internet.
@karalabe
Thank you a lot!
I am able to recreate this exploit after playing around with a testnet, unlocking an account for signing, and openeing ports. After submitting a tx for the unlocked account, a botnet is actively spamming the account to drain the account of ether. This often makes the account unable to send an additional account for avery long period of time due to the gas price used. Theres also a post here on this topic. https://blog.rapid7.com/2018/07/09/blockchain-blunders-exposing-digital-pickpockets-in-the-ethereum-ecosystem/
The user tx will finish first:
> eth.pendingTransactions
[{
blockHash: null,
blockNumber: null,
from: "0x343b66786ada487cf186250908c1886552eb660d",
gas: 3000000,
gasPrice: 3000000000,
hash: "0xa81c2fedba97ef13c612c85c484c11be03315a4180eecb03d7aec52fb3d4efab",
input: "0x94d008ef00000000000000000000000080ce9596ed870b0a03e57d3b311e5c67c29e1d26000000000000000000000000000000000000000000000000000000000000000100000000000000000000000000000000000000000000000000000000000000600000000000000000000000000000000000000000000000000000000000000000",
nonce: 34,
r: "0x9f8164751a032a406b5e2cbcda9e5d719bf4ec90fe66cee753eef6570ab2bc31",
s: "0x6731f6401873e0152354e55b40ab151b18e280c1d0637d3d30cf96d223a22202",
to: "0x3976dbe85660f991a6f7fb56fe021149c13781e4",
transactionIndex: 0,
v: "0xe059",
value: 0
}]
And then a following spam of txs follows:
eth.pendingTransactions
[{
blockHash: null,
blockNumber: null,
from: "0x343b66786ada487cf186250908c1886552eb660d",
gas: 21000,
gasPrice: 75713925761000,
hash: "0x1ae89c0dccafba24cef61112787ef640cf2b84d2a4a79d790ac25ea2a23b4fa1",
input: "0x",
nonce: 35,
r: "0x2601bbadaeba3ebc7fc99dd04a2224106ccdb012d32c4315ea918e5efc4f410f",
s: "0x6c8fb12456f90542eadbd74ce3c032464b142fccc3cbb6396508c38147bea001",
to: "0x7097f41f1c1847d52407c629d0e0ae0fdd24fd58",
transactionIndex: 0,
v: "0xe05a",
value: 28409864936019000000
}, {
blockHash: null,
blockNumber: null,
from: "0x343b66786ada487cf186250908c1886552eb660d",
gas: 21000,
gasPrice: 75713925761000,
hash: "0xabf2db6f5c52fcca50938e906a68db6002a03dd078150c94f57b213d7a5af6b2",
input: "0x",
nonce: 36,
r: "0x60645600b34ab198be3bb8307ae80b62b02337dae703a4e4154b1d0b281f6b19",
s: "0x715ce33a57ee7e261478007a03329639d0fa113b40c2da6e0b34dc1e6e084e10",
to: "0x8652328b96ff12b20de5fdc67b67812e2b64e2a6",
transactionIndex: 0,
v: "0xe05a",
value: 28409864936019000000
}, {
blockHash: null,
blockNumber: null,
from: "0x343b66786ada487cf186250908c1886552eb660d",
gas: 21000,
gasPrice: 75713925761000,
hash: "0xfc06cdcf1f12b8c43d6600b078f2e3d77e9d5bacecacb3f82ef100802bdda240",
input: "0x",
nonce: 37,
r: "0x2becffb934cd8ae116b61332d72c8acc95ad8794b1869a023a824145c1ee26b6",
s: "0x5e6104bcc06e8fbcbf08d62ebf1ee975e8824f1899c4340c3ff5c73fd275a76",
to: "0x8652328b96ff12b20de5fdc67b67812e2b64e2a6",
transactionIndex: 0,
v: "0xe059",
value: 28409864936019000000
}, {
blockHash: null,
blockNumber: null,
from: "0x343b66786ada487cf186250908c1886552eb660d",
gas: 21000,
gasPrice: 75713925761000,
hash: "0x70c6341a27e5c650584e174547e1f4bf5e2b777acf2e334b58454edca96c4a7c",
input: "0x",
nonce: 38,
r: "0x48da0e419c461cf53d6bd60f3a8e3f98382fd47f6851234f206b6002c5a2199a",
s: "0x7c2637f0c74a529ba10cdd8a8aef3aa65896797f260d2f006e918d8d3eb5052e",
to: "0x7097f41f1c1847d52407c629d0e0ae0fdd24fd58",
transactionIndex: 0,
...
]
Additionally the accounts used by the spamming are listed here:
0x7097f41f1c1847d52407c629d0e0ae0fdd24fd58
0x6e4cc3e76765bdc711cc7b5cbfc5bbfe473b192e
https://etherscan.io/address/0x8652328b96ff12b20de5fdc67b67812e2b64e2a6
https://etherscan.io/address/0x7097f41f1c1847d52407c629d0e0ae0fdd24fd58
https://etherscan.io/address/0x6e4cc3e76765bdc711cc7b5cbfc5bbfe473b192e
As you can see this appears to have been exploited as early as 7 hours on the mainnet ago by these accounts.
This bot is looking for any 8545 traffic and as it effects puppeth and public chains alike.
@karalabe is there really no other solution than to force users to enforce a particular usage of geth + ports? Is there no warning that can be spit out by geth when this is detected?
There is a PR that will introduce a new flag and force users to explicitly specify --insecure-something-something, otherwise it will refuse to unlock accounts if the RPC is open. It's however a breaking change for exchanges, so we can only merge that when we do a big version bump.
It might be interesting to have an "unlock for N transactions" mechanism as well. It seems the user initiated tx always gets executed first.
Supose a scenario in which you want your blockchain to be exposed to all the internet, you want people
to invoke your smart contract from any source.
For that you need to launch your node with rpcport and origin "*"
Also you need the node account unlocked for mining purposes.
On that scenario, a bot like those ones will decrease your coinbase balance quickly..
So, is there a way to achieve this on a secured way?
I have tried to run 2 nodes, 1 of them with the rpc ports blocked and with the unlocked account, the other one has the rpc ports open but the account is locked.
The second node is just for interactions with metamas/myetherwallet/etc.
The thing is if i hit that 2nd node, since the account isnt unlocked, it can mine the blocks:
WARN [08-01|19:53:13.837] Block sealing failed
err="authentication needed: password or unlock"
Is there a way to build a "safe proxy" or something like that? a node that you can access by rpc and it will send the transactions to the other node that can mine?
already solved this problem with bots? and if you change the port to another problem does not solve? how to avoid it? without blocking access from the outside!
spam - 0x7097f41F1C1847D52407C629d0E0ae0fDD24fd58
after unlock.personalaccount(eth.account[0])
3930819.992510775000014 CUSTOM ETH open 8545 port
INFO [01-28|16:57:46.878] Commit new mining work number=66 sealhash=654450…5f2e2f uncles=0 txs=1 gas=21000 fees=69505.00749 elapsed=492.565µs
INFO [01-28|16:57:47.114] Submitted transaction fullhash=0xc6542e566c867feaf4e1e5d0d5c3e33048a8b30d8d5d262449b8d42f27ec91b3 recipient=0x7097f41F1C1847D52407C629d0E0ae0fDD24fd58
INFO [01-28|16:57:47.679] Submitted transaction fullhash=0xc5e7c4fd6c06c6dc532715463baecae261025d2cc85ca6d52f82ea7eeea06300 recipient=0x7097f41F1C1847D52407C629d0E0ae0fDD24fd58
INFO [01-28|16:57:48.373] Submitted transaction fullhash=0x1b5e6c1ac3470f4022e3b31abf25141a804d69975b43507e8dced4584bf7fd00 recipient=0x7097f41F1C1847D52407C629d0E0ae0fDD24fd58
INFO [01-28|16:57:49.023] Submitted transaction fullhash=0x721052e679af65acf492e3e1f38e31cd1bcae0746157b8cfe1718f9d682ce631 recipient=0x7097f41F1C1847D52407C629d0E0ae0fDD24fd58
INFO [01-28|16:57:49.643] Submitted transaction fullhash=0x9fc606fbed5b7a9613eff51e96d048761b2e1b56ccc21f4e122fa453ba300fee recipient=0x7097f41F1C1847D52407C629d0E0ae0fDD24fd58
INFO [01-28|16:57:49.878] Commit new mining work number=66 sealhash=654450…5f2e2f uncles=0 txs=1 gas=21000 fees=69505.00749 elapsed=351.271µs
INFO [01-28|16:57:50.243] Submitted transaction fullhash=0x803cd377587c413d9f6fcb0f56f93100a8ba5fdd5a8e9e8818f135725c977f17 recipient=0x7097f41F1C1847D52407C629d0E0ae0fDD24fd58
INFO [01-28|16:57:50.866] Submitted transaction fullhash=0xd4193f408bccfd8f9039e80218295810bc559f697106b2d485cff6dafd4007b4 recipient=0x7097f41F1C1847D52407C629d0E0ae0fDD24fd58
INFO [01-28|16:57:51.886] Submitted transaction fullhash=0x3db31fcfd65269b253cd8d4a7dff1ee802a252f3c0970a0e2d3147920b2a5dce recipient=0x7097f41F1C1847D52407C629d0E0ae0fDD24fd58
3930819.992510775000014 CUSTOM ETH open 8545 port
Most helpful comment
Did you open the HTTP/WebSocket interface for the whole internet to access? There are people actively scanning for Ethereum nodes, connecting to them and trying to send out funds from them. If you opened your machine for the entire world, someone will actively try to exploit it when you unlock your account.
And here's the proof: your recipient account on:
Please never open your API ports to the whole internet.