Generator-jhipster: Integrate automatic dependency scanning for security vulnerabilities.
Hi Folks, Brian here from Snyk
I had a chat with Matt Raible @mraible yesterday and he asked me to submit this issue.
We would love to integrate our free open-source dependency scanning capabilities into JHipster. As Snyk can scan issues in for multiple ecosystems like NodeJS, Java and .Net we feel that an integration makes sense.
What we would like to achieve is that JHipster users can use Snyk out of the box to scan their applications when they build. This to prevent dependencies with vulnerabilities entering the application or warn the user when there is a vulnerability found. Basically providing help to the developers out of the box to keep their application more secure.
Me and my team would be happy to discuss this further.
All 14 comments
@bmvermeer thanks for entering this issue. ❤️
If developers want to integrate Snyk w/o JHipster adding support, how would they do it?
Is it as simple as:
npm install -g snyk
snyk test
Will this test package.json and pom.xml? What about Gradle, will it auto detect build.gradle and build.gradle.kts?
Do you think we should install Snyk and run it as part of the app-generation process, or only when generating CI/CD files? If CI/CD, what commands should we run?
Another thought: JHipster has support for generating K8s config and building Docker images with Jib. How can Snyk help scan those configurations and detect vulnerabilities?
@mraible
It is indeed as easy as you say to use the snyk cli.
npm install -g snyk
snyk test
But before the first test a user needs to authenticate once with their free account.
By using
snyk auth
you will get redirected to the browser and you can signing or signup. If you already have an account the token can be provided like
snyk auth <token>
The test command snyk test will look for a manifest file itself and use this for scanning this can be any manifest file we support.
(package.json, pom.xml, build.gradle etc.) If you want to scan all. projects including the projects in subfolders you can supply the flag --all-projects.
For docker images, you can use the same cli
snyk container test [options] [image]
To test docker images.
For both Snyk Open Source (the dependency scanning) and Snyk Container, you can also use the monitor function.
This takes a snapshot of that moment sends it to the Snyk platform and monitors it daily. So if some vuln is discovered over time (or a fix for an. existing vuln) you will be notified. This is normally used just before you app goes into production.
snyk monitor
snyk container monitor
For Kubernetes, we recently release iac (infrastructure as code). The team is still developing more features around this.
For now, you can scan individual Kubernetes files like this.
snyk iac test /path/to/Kubernetes.yaml
There are tons of flags to do extra things like output in json etc, but this is the recap.
For reference:
https://support.snyk.io/hc/en-us/categories/360000456217-Snyk-CLI
and the help section in the CLI itself.
snyk --help
Results from my Twitter poll indicate that users would like to see Snyk configured locally, as well as in the CI/CD generator.
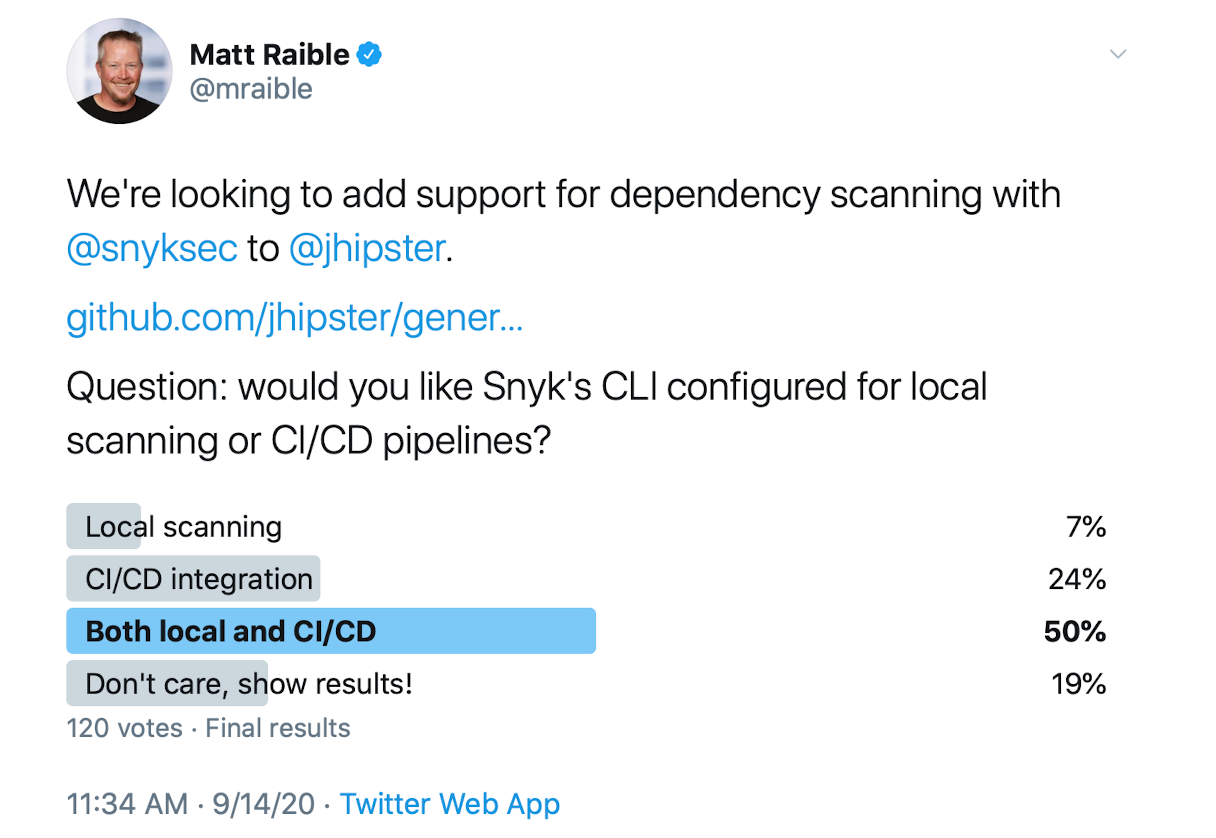
@bmvermeer I think there are two paths forward:
- Create an app with JHipster and check it into GitHub. Create a branch and PR that shows what needs to change to add Snyk CLI by default. It's probably just another dependency and possibly updating the
README. Then, usejhipster ci-cdto set up a CI pipeline. Check all these changes in so we can see what code needs to change. - Write up a blog post that describes how to integrate Snyk for local scanning and CI/CD.
For more information about CI/CD with JHipster, see Setting up Continuous Integration.
Thanks, @mraible
I will schedule some time next week to do some research on the first one.
Probably I will make it a 2 step task. First creating a blog post and after that see if and how we can really integrate.
@bmvermeer Any updates?
Yes we will release a blog post on how to integrate Snyk with JHipster this week (probably today).
I will post a link here when it is live.
I did not yet figure out if and where I can put this in the generator.
@bmvermeer Cool! I'd be happy to help integrate it into the generator (or a blueprint).
This issue is stale because it has been open 30 days with no activity.
Our core developers tend to be more verbose on denying. If there is no negative comment, possibly this feature will be accepted.
We are accepting PRs :smiley:.
Comment or this will be closed in 7 days
Re-opening and adding a bug bounty. I'll work on it near the end of the year if no one else picks it up.
It should be similar to what I did for SonarCloud in CICD, so I'm starting to work on this
It should be ready for v7 I think
all work is done, so it's ready for the beta release next week
Most helpful comment
@mraible https://snyk.io/blog/jhipster-security-scanning/