Core: Unable to setup Cloudflare integration
The problem
Hi guys,
I'm trying to migrate cloudflare to the new integration. I've created a new token with the right scopes but when I put it into the integration settings I receive Failed to connect error.
What am I doing wrong?
Environment
- Home Assistant Core release with the issue: 0.117.0
- Last working Home Assistant Core release (if known): 0.116.4
- Operating environment (OS/Container/Supervised/Core): Home Assistant Container
- Integration causing this issue: cloudflare
- Link to integration documentation on our website: https://www.home-assistant.io/integrations/cloudflare/
Problem-relevant configuration.yaml
Traceback/Error logs
Additional information
Token is active:
$ curl -s "https://api.cloudflare.com/client/v4/user/tokens/verify" \
-H "Authorization: Bearer MYTOKEN" \
-H "Content-Type:application/json" | jq -r .result.status
active
and with right scopes:
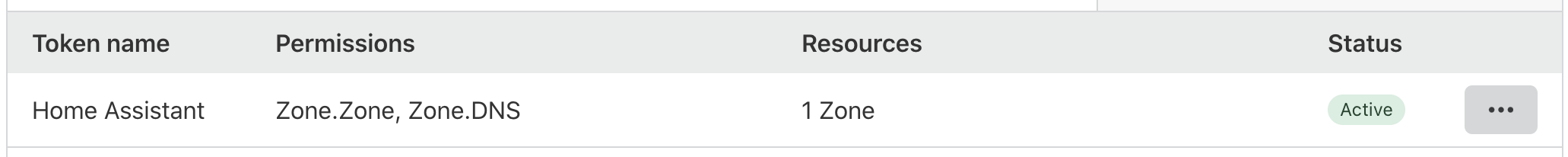
All 20 comments
cloudflare documentation
cloudflare source
(message by IssueLinks)
Hey there @ludeeus, @ctalkington, mind taking a look at this issue as its been labeled with an integration (cloudflare) you are listed as a codeowner for? Thanks!
(message by CodeOwnersMention)
How far did you get?
I try to setup a new integration, I put the token, end 😅
The error points to a connection or timeout issue.
The curl you did, can you run that from inside the container as well?
The error points to a connection or timeout issue.
{
"type": "form",
"flow_id": "3e82c54283dd4e159121d25da3546c42",
"handler": "cloudflare",
"step_id": "user",
"data_schema": [
{
"type": "string",
"name": "api_token",
"required": true
}
],
"errors": {
"base": "cannot_connect"
},
"description_placeholders": null
}
The curl you did, can you run that from inside the container as well?
bash-5.0# curl -s "https://api.cloudflare.com/client/v4/user/tokens/verify" \
-H "Authorization: Bearer TOKEN" \
-H "Content-Type:application/json" | jq -r .result.status
active
Same problem, thought it could be AdGuard Home but disabling it didn't help...
My token is also checked and active
Just tried putting the token repeatedly (retry after Failed to connect) and worked!
Just tried putting the token repeatedly (retry after Failed to connect) and worked!
That's not normal at all. How many times did you try?
@ludeeus I tried again as @Chreece suggested and now the error message changed to _Invalid authentication_
{
"type": "form",
"flow_id": "b1f5732b41b14e5abae2bc4614e0ed6b",
"handler": "cloudflare",
"step_id": "user",
"data_schema": [
{
"type": "string",
"name": "api_token",
"required": true
}
],
"errors": {
"base": "invalid_auth"
},
"description_placeholders": null
}
Just tried putting the token repeatedly (retry after Failed to connect) and worked!
That's not normal at all. How many times did you try?
I think 3 or 4 times.
When I tried before the success, the integration did something (saw some scrollbars left and under coming and going) but Failed to connect. Maybe it's a time out because connection problem thing. I'm using Adguard home, Wireguard and some other goodies that made my Internet connection a bit slower (at least at dns level).
Sorry for too much info, I'm trying only to give some thoughts on the problem 😀
I have no speed or filtering issue at all, cloudflare was (and is) reachable from my LAN
Invalid auth you get if you are not authorized for the requested enpoints
Invalid auth you get if you are not authorized for the requested enpoints
I added the requested scopes. Do you think I did something wrong?
Yes, you limited it to 1 zone, it needs to be able to list all zones.
Yes, you limited it to 1 zone, it needs to be able to list all zones.
Really? 🦉 Is there a specific reason for that? I think that from a security standpoint this could be improved.
There's no need to be able to edit all my zones. wdyt?
BTW I tried it again with the suggested scopes and it worked
It needs to be able to read/list all zones so you can choose the correct one on the second screen.
CF does not offer that level of granulated permissions in their UI.
You can create a token with their API if you want that.
I can have read on all zones and edit on a sigle one if I create the token via API? Good to know ty
Yes @maxcanna
https://api.cloudflare.com/#user-api-tokens-create-token
curl -X POST "https://api.cloudflare.com/client/v4/user/tokens" \
-H "Authorization: Bearer xxxxxxxxxxxxxxx" \
-H "Content-Type: application/json" \
--data '{"name":"test","policies":[{"effect":"allow","resources":{"com.cloudflare.api.account.zone.*":"*"},"permission_groups":[{"id":"xxxxxxxxxxxxxxx","name":"Zone Read"}]},{"effect":"allow","resources":{"com.cloudflare.api.account.zone.xxxxxxxxxxxxxxx":"*"},"permission_groups":[{"id":"xxxxxxxxxxxxxxx","name":"Zone Write"},{"id":"xxxxxxxxxxxxxxx","name":"DNS Read"}]}]}'
The first policy is creating read access to all zones, the second policy is creating read/write to a single zone.
Awesome! TY @ludeeus