Che: What is the easy way to get Che CA cert for end-user
Is your enhancement related to a problem? Please describe.
We have the documentation https://www.eclipse.org/che/docs/che-7/setup-che-in-tls-mode-with-self-signed-certificate/#che-usage-with-tls_setup-che-in-tls-mode-with-self-signed-certificate that describes how to Set up and use Che with self-signed Cert.
And it's more for Che Administrators...
Che End-user don't have cluster access to download CA certificate.
This issue is created to collect opinions and ideas how Che end-user can easily get CA cert to import into browser.
Possible option:
- It would be great if Che Server serves CA and gives users an ability to download it as a file. But I'm not sure if it's really secure thing to do.
- chectl could provide some command to retrieve non-CA but end certificate user is able to import into browser (I afraid it won't be possible to import such certificate into firefox). Like https://superuser.com/questions/1104984/get-a-servers-ssl-tls-certificate-using-openssl-s-client/1176346
- Another
All 7 comments
/cc @mmorhun
@sleshchenko that's interesting issue.
As about possible ways to resolve. First what comes into my mind is to create new chectl command which will retrieve CA certificate (as chectl has cluster wide rights) and write it into a file which could be imported into a browser. Downside of it is that only cluster admins will be able to use this approach.
I also do not mind about Che master endpoint to serve the public part of CA certificate. But you mentioned some security issues there, could you please elaborate on them?
Also we may retrieve public part of Che server certificate by just querying it (we may use chectl without admin rights for the cluster, for example). But I am not sure that this is the best idea. The good way to go is using CA public certificate as Che servers's one might be renewed after some time and this will force users to redo the procedure again and again.
I also do not mind about Che master endpoint to serve the public part of CA certificate. But you mentioned some security issues there, could you please elaborate on them?
I can imagine a situation when the attacker owns the network which you use and replaces some endpoints, like Che one.
Then they will be able to let you download any self-signed CA they need, after you import it into a browser - all attacker endpoints will be trusted for you.
I'm not sure it's technically possible or even makes sense. It's just my imagination
@skryzhny You know more about networks, do you think it's safe to server public CA cert via CHe Server?
Also we may retrieve public part of Che server certificate by just querying it (we may use chectl without admin rights for the cluster, for example). But I am not sure that this is the best idea.
Maybe I do something wrong but Firefox does not allow to import end (CA:false) certificate. Could you recheck it on your side?
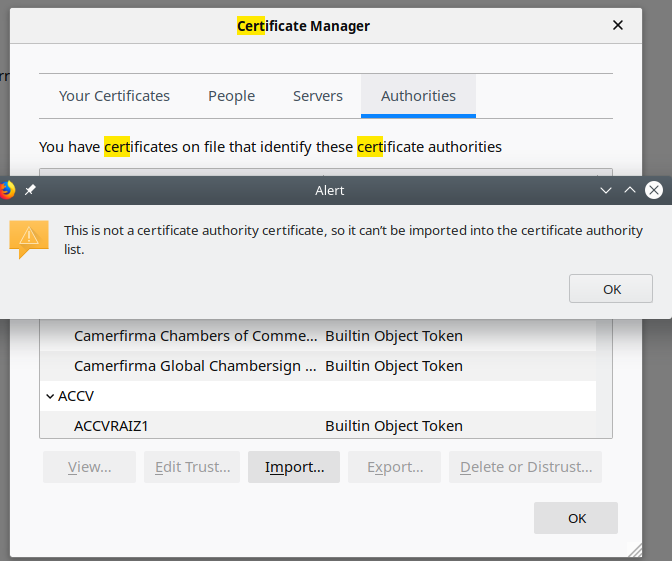
I can imagine a situation when the attacker owns the network which you use and replaces some endpoints, like Che one.
Then retraiving the certificate by querying Che server is not safe too.
In this case the only secure way is to pass the CA public certificate directly to the users. And this would be task of Che server administrator.
We can't determine if user trusts network or not.
Only thing I can imagine - create a web-page that contains a download link to CA and warning about possible risks if user accesses that page over untrusted network.
Probably it should be only page that serves unencrypted traffic.
@sleshchenko
we added chectl cacert:export command to retrieves Eclipse Che self-signed certificate.
Does it solve your issue?
Does it solve your issue?
I think so.
Fixed by https://github.com/che-incubator/chectl/pull/669
Most helpful comment
Then retraiving the certificate by querying Che server is not safe too.
In this case the only secure way is to pass the CA public certificate directly to the users. And this would be task of Che server administrator.