Cert-manager: Set a CommonName when using ingress-shim
Is your feature request related to a problem? Please describe.
If the CA requires the common name to be provided then we cannot use the ingress resource with just this cert-manager.io/issuer annotation since the common name is not provided to Vault. So we need to manually create a certificate for every ingress resource and then bind it to the ingress TLS secret ref.
Describe the solution you'd like
Add support for annotation cert-manager.io/common-name in the ingress resource. Similar to this:
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
annotations:
kubernetes.io/ingress.class: internal-ingress
cert-manager.io/issuer: vault-issuer
cert-manager.io/common-name: foo.example.com
labels:
...
/kind feature
All 8 comments
In the PKI role itself you can disable a required common name, after that it works for me.
It would still be better if you could specify the common-name somehow, or if it just used the host field for that...
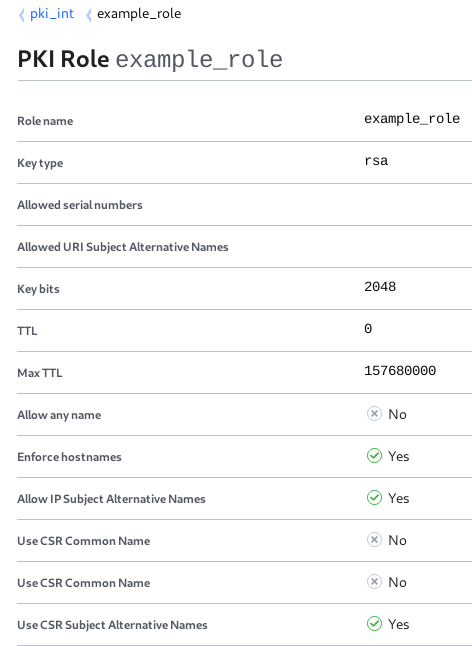
Got same issue after cert-manager upgrade. Any workarounds except disabling common name in vault?
I think we can probably default commonName to equal tls[].hosts[0] in the ingress config when creating/updating the Certificate resource in ingress-shim. We can't make this the default behaviour for Certificate resources themselves as that would prevent people ever being able to avoid creating a Certificate that only specifies dnsNames and no common name.
The other thing to note here is the difference in max length between commonName and a DNS name. A common name can only be up to 63 characters, whereas a dnsName can be 253. So this will also put a limit on the max length of the first DNS name that you specify, which is a bit confusing. In these cases we could opt to not set the commonName at all like we do today.
Could you update your title to reflect this? Would you be interested in making a PR to implement this change too?
/priority backlog
/area ingress-shim
/help-wanted
Issues go stale after 90d of inactivity.
Mark the issue as fresh with /remove-lifecycle stale.
Stale issues rot after an additional 30d of inactivity and eventually close.
If this issue is safe to close now please do so with /close.
Send feedback to jetstack.
/lifecycle stale
/remove-lifecycle stale
I have the same problem and I cannot disable common name on vault.
Is there any solution?
@mercantiandrea for now I can suggest not to use the ingress-shim but to use the Certificate resource to ask for a certificate and link the ingress TLS secret name to the same as in thesecretName field of the Certificate.
We hope to add more configuration options to the ingress-shim in a future release!
I have a use case where I need to import the certificate using keytool from inside the container.
If I generate the cert using ingress-shim + self signed issuer or ca, then keytool won't accept that cert because the DN is empty.
I know this setup is only useful for development. If you use proper CA, they usually gave the certificate with DN included.
I also know that making the Certificate resource by yourself and put the DN there will solve the issue, as @meyskens mentioned.
But other than that, the possibility of adding that annotation options to the ingress-shim seems really interesting.
The proposed solution by @munnerz:
I think we can probably default commonName to equal tls[].hosts[0] in the ingress config when creating/updating the Certificate resource in ingress-shim. We can't make this the default behaviour for Certificate resources themselves as that would prevent people ever being able to avoid creating a Certificate that only specifies dnsNames and no common name.
CMIIW, adding annotation options to the ingress-shim and making default commonName equal to tls[].hosts[] seems like two separate implementations. Can't we just add annotation options without making the commonName default from tls.hosts? If the the annotation are not provided, then just create the certificate without common name like what we have now?
Most helpful comment
I think we can probably default
commonNameto equaltls[].hosts[0]in the ingress config when creating/updating the Certificate resource iningress-shim. We can't make this the default behaviour for Certificate resources themselves as that would prevent people ever being able to avoid creating a Certificate that only specifiesdnsNamesand no common name.The other thing to note here is the difference in max length between commonName and a DNS name. A common name can only be up to 63 characters, whereas a dnsName can be 253. So this will also put a limit on the max length of the first DNS name that you specify, which is a bit confusing. In these cases we could opt to not set the commonName at all like we do today.
Could you update your title to reflect this? Would you be interested in making a PR to implement this change too?
/priority backlog
/area ingress-shim
/help-wanted