Azure-docs: [MySQL] How to configure custom client certificates at MySQL server end
Description:
Currently, the documentation provides instructions for configuring SSL during MySQL server-client communication.
As per the above documentation, we can use the root CA certificate which is publicly available for the communication. But it was noticed that when we do not set the certificate, we are still able to communicate with the MySQL server by using MySQL client SSL mode.
As per the informative guide, we can configure custom client (and server certificates too) on the server side which can be used to perform client certificate based verification and restrictions on the server end.
Is uploading custom client certificates which can be used for verification allowed with Azure MySQL service? If so, do we have documentation available with steps for achieving this?
Suggested Assignees:
@ajlam @JasonWHowell
Document Details
⚠ Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.
- ID: 77a94e6f-a799-494f-f2f9-171c1804e5f4
- Version Independent ID: 0ca5e2ae-5889-61ef-3ce7-5c447f7519a6
- Content: Configure SSL - Azure Database for MySQL
- Content Source: articles/mysql/howto-configure-ssl.md
- Service: mysql
- GitHub Login: @ajlam
- Microsoft Alias: andrela
All 7 comments
Hello @chirangaalwis, Thank you for your feedback! We will review and update as appropriate.
@chirangaalwis Enforcing to use the SSL does not necessarily need to provide the certificate. There are multiple modes to use SSL. If we select 'Require and Verify CA' then it become mandatory to provide the certificate. However, if we select other options then we might not need to provide the certificate.
Also as per the article, currently only mentioned certificate can be used to connect to Azure MySQL:
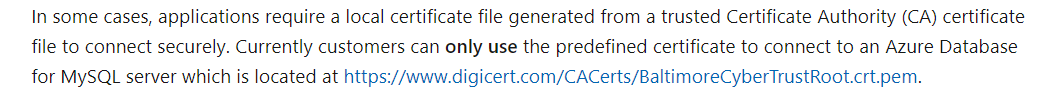
@chirangaalwis Enforcing to use the SSL does not necessarily need to provide the certificate. There are multiple modes to use SSL. If we select 'Require and Verify CA' then it become mandatory to provide the certificate. However, if we select other options then we might not need to provide the certificate.
@AnuragSharma-MSFT thanks for the above information. But I didn't encounter any options which allows users to enforce 'Require and Verify CA' on the server side in the Azure Portal. I only came across the option to enforce SSL. But as you have mentioned, this does not require us to always provide the certificate.
How can we achieve the above? Do we have a guide which provides the necessary instructions?
@chirangaalwis - Let me attempt to clarify. First to enable SSL, SSL needs to be enabled on MySQL server side. You would enable it on server side from Azure portal which is the option you are referring to. A certificate viz (https://www.digicert.com/CACerts/BaltimoreCyberTrustRoot.crt.pem) (soon to be changed to https://cacerts.digicert.com/DigiCertGlobalRootG2.crt.pem) is used on the server side to encrypt all the connections. This is irrespective of whether you specify and configure certificate on the client side.
If on the client side, certificate is not specified (no verify ca on client side drive), connections from server are still encrypted but connections initiated from client to the server is not encrypted. This can potential lead to eavesdropping where someone can listen in the connections between client and server. To prevent this, on client side, you can enforce SSL by setting require and verify CA. When you do verify CA, you need to configure certificate on client side too which will enforce SSL connections originated from client and will reach in the encrypted format to the server and vice-versa.
On client side, in the connection string, you would specify sslmode=verify-ca to enforce this on client side. sslmode=disable, sslmode=allow, sslmode=prefer, or sslmode=require doesnt require certificates from client side.
Hope that clarifies !!!
@savjani thanks a bunch for the clarification. I will try this out and get back, if required.
@chirangaalwis we'll close out the issue since a resolution has been provided. Please let us know if further assistance is needed. Thanks! Jason #please-close
Can we enable mTLS with the MySQL server? That's the key requirement of the original post. @JasonWHowell @savjani