Azure-docs: Firewall rules creation
Hi there,
We have successfully deployed Redis caches with ARM templates, however we can't seem to do the same with firewall rules (as part of the same deployment). I'm not getting any errors, just no rules applied to the firewall section.
This is the ARM template (IPs just for replication purposes):
"resources": [
{
"apiVersion": "2015-08-01",
"name": "[parameters('redisCacheName')]",
"type": "Microsoft.Cache/Redis",
"location": "[parameters('redisCacheLocation')]",
"properties": {
"enableNonSslPort": "[parameters('enableNonSslPort')]",
"sku": {
"capacity": "[parameters('redisCacheCapacity')]",
"family": "P",
"name": "Premium"
},
"resources": [
{
"type": "firewallRules",
"apiVersion": "2017-10-01",
"dependsOn": [
"[parameters('redisCacheName')]"
],
"location": "[resourceGroup().location]",
"name": "KubernetesIP",
"properties": {
"startIpAddress": "1.2.3.4",
"endIpAddress": "1.2.3.4"
}
},
{
"type": "firewallRules",
"apiVersion": "2017-10-1",
"dependsOn": [
"[parameters('redisCacheName')]"
],
"location": "[resourceGroup().location]",
"name": "CronIP",
"properties": {
"startIpAddress": "2.2.2.2",
"endIpAddress": "2.2.2.2"
}
}
],
Document Details
⚠ Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.
- ID: ce050b09-7c14-6aa4-494a-b4cd8aa06f88
- Version Independent ID: 9f494624-ccca-71b7-a650-998330279211
- Content: Provision a Redis Cache using Azure Resource Manager
- Content Source: articles/redis-cache/cache-redis-cache-arm-provision.md
- Service: cache
- GitHub Login: @wesmc7777
- Microsoft Alias: wesmc
All 16 comments
@mariojacobo We are happy to hear that you were able to resolve your issue. We will keep the thread closed as a result.
What was the solution to this issue @mariojacobo?
@thecherrytree we didn't find the solution, just gave up on the product completely, and moved to another cloud.
@BryanTrach-MSFT or @Mike-Ubezzi-MSFT -- can you please reopen this story - I believe this is a legitimate bug. When we deploy firewall rules, their deployment to the redis cache is random and unpredictable. We're deploying 5 firewall rules. Sometimes they all deploy, sometimes one deploys, sometimes none deploy. What explains this behavior?
@mariojacobo can you reopen?
As an example -- here is a recent deployment. All of the firewall rules are stated as created. The deployment logs say they are all successful.
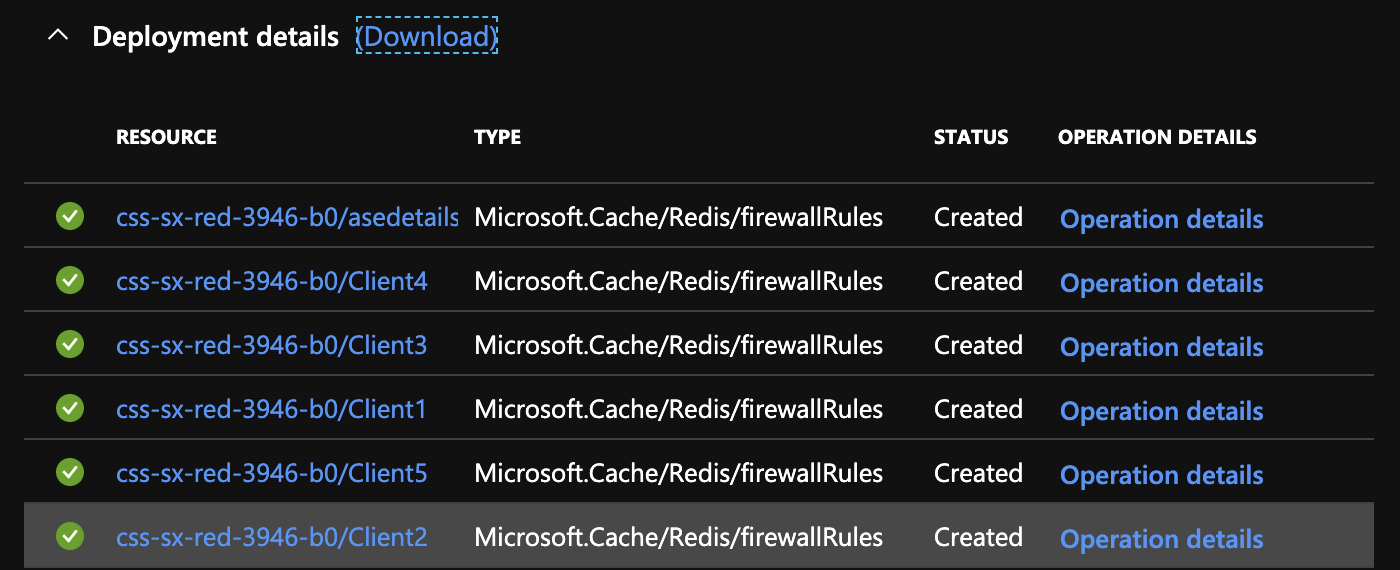
When I actually go to the Cache and look at the firewall one is missing:
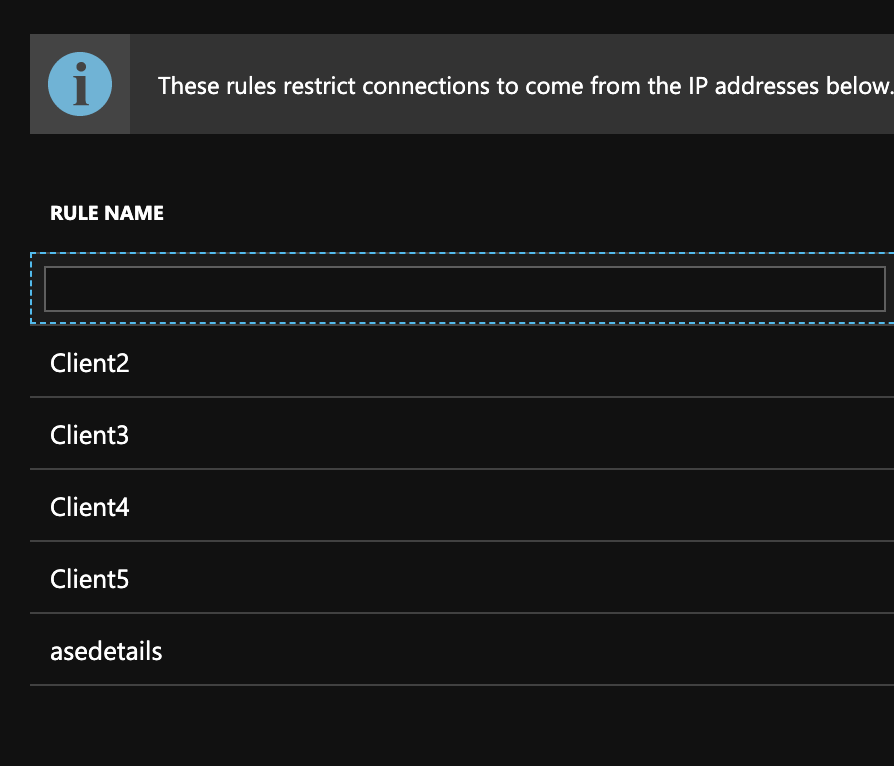
All of the logs, deployment.json, deployment_operations.json say that they were created.
Here are the root resources generating the firewall rules:
{
"type": "Microsoft.Cache/Redis/firewallRules",
"apiVersion": "2018-03-01",
"name": "[concat(variables('redisCacheName'), '/', 'asedetails')]",
"dependsOn": [
"[resourceId('Microsoft.Cache/Redis/', concat(variables('redisCacheName')))]"
],
"properties": {
"startIP": "[reference('getAseDetails').outputs.details.value.StartIP]",
"endIP": "[reference('getAseDetails').outputs.details.value.endIP]"
}
},
{
"type": "Microsoft.Cache/Redis/firewallRules",
"apiVersion": "2018-03-01",
"name": "[concat(variables('redisCacheName'), '/', parameters('firewallIpAddresses')[copyIndex()].clientName)]",
"location": "[variables('location')]",
"dependsOn": [
"[resourceId('Microsoft.Cache/Redis/', concat(variables('redisCacheName')))]"
],
"properties": {
"startIP": "[parameters('firewallIpAddresses')[copyIndex()].start]",
"endIP": "[parameters('firewallIpAddresses')[copyIndex()].end]"
},
"copy": {
"name": "firewallrulecopy",
"count": "[length(parameters('firewallIpAddresses'))]"
},
"condition": "[variables('allowAzureIps')]"
}
@mariojacobo Can you please send your Azure Subscription ID and instance name to AzCommunity and I will forward to the product group to be investigated. This is a better means to investigate. I am going to use your Subscription ID to enable a onetime free support request and return instructions to have that SR created. Please send back to me the SR # that is created so that I can use the SR to capture the issue and resolution. Thank you!
@thecherrytree If you are having the same issue, please follow the instruction in the previous comment and I can assist you.
@Mike-Ubezzi-MSFT thanks, but it's no longer required on my end. We moved on to another provider.
@Mike-Ubezzi-MSFT - it looks like those Redis Cache rules showed up several hours later. Is it possible for someone to explain this behavior before I submit a ticket? Is this "working as expected"?
Hi Carson – I am having some issues accessing GitHub and hope by responding to this email thread that this makes it as a comment to the issue. Please file a support ticket for this, as I did escalate this to the product group. There may have been a manual intervention to resolve it but that is not a workable solution, nor is the delay if it wasn’t a manual intervention. Thank you!
Mike Ubezzi
Cloud Solutions Engineer II | Azure CxP
+1 (425) 722-2789
Update: The product group is investigating this issue.
@thecherrytree I received feedback on this issue and this is a known issue that is being addressed. The current solution is to sequentially step through each one instead of listing multiple valies:
I think this customer is hitting a known bug when creating multiple firewall resources in parallel. We are already actively working on a fix for this issue. Until this issue is fixed, the customer can work around this issue by creating the firewall rules sequentially. This can be done by leveraging the ‘dependsOn’ template functionality: https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-group-define-dependencies#dependson. Each firewall resource should depend on the previous firewall resource in order to have them created sequentially.
Please let us know if you are still having issues.
Thanks for the update on this, Mike. So this sounds like an interesting solution. We will test it. We've leveraged dependsOn for many of our resources as a standard practice, so we're familiar with this capability.
I have one question: Would a dependsOn work with an array of rules of variable length that are being passed into a resource using the copyIndex() function?
In our case, our input firewall rules are of a variable length, we utilize the copyindex() function to iterate through them:
{
"type": "Microsoft.Cache/Redis/firewallRules",
"apiVersion": "2018-03-01",
**"name": "[concat(variables('redisCacheName'), '/', parameters('firewallIpAddresses')[copyIndex()].clientName)]",**
"location": "[variables('location')]",
"dependsOn": [
"[resourceId('Microsoft.Cache/Redis/', concat(variables('redisCacheName')))]"
],
"properties": {
**"startIP": "[parameters('firewallIpAddresses')[copyIndex()].start]",
"endIP": "[parameters('firewallIpAddresses')[copyIndex()].end]"**
},
**"copy": {
"name": "firewallrulecopy",
"count": "[length(parameters('firewallIpAddresses'))]"
}**,
"condition": "[variables('allowAzureIps')]"
}
What would a dependsOn look like with the copy index function? If a dependsOn is the position of the index-1, with the exception of the first resource, I'm not sure this solution would work for us...
@thecherrytree You can use a serial copy, which is one firewall rule at a time:
If the solution is to create 1 firewall rule at a time, there is a way to deploy resource using Copy Serially i.e. one resource at a time using mode: Serial,
https://github.com/Azure/azure-docs-json-samples/blob/master/azure-resource-manager/multipleinstance/serialcopystorage.json
Ok, great. That makes sense, I didn't realize that the default was parallel... Since we're using the serial copy, that means our resource would look like this? Let me test it and get back to you.
{
"type": "Microsoft.Cache/Redis/firewallRules",
"apiVersion": "2018-03-01",
"name": "[concat(variables('redisCacheName'), '/', parameters('firewallIpAddresses')[copyIndex()].clientName)]",
"location": "[variables('location')]",
"dependsOn": [
"[resourceId('Microsoft.Cache/Redis/', concat(variables('redisCacheName')))]"
],
"properties": {
"startIP": "[parameters('firewallIpAddresses')[copyIndex()].start]",
"endIP": "[parameters('firewallIpAddresses')[copyIndex()].end]"
},
"copy": {
"name": "firewallrulecopy",
"count": "[length(parameters('firewallIpAddresses'))]",
"mode": "serial",
"batchSize": 1
},
"condition": "[variables('allowAzureIps')]"
}
@thecherrytree Wanted to follow-up to see if this second option of a serial copy method was working for you? There could be a difference if you are itemizing a list of individual IPs versus a range as detailed in the sample you provided. Thanks for any update.