Aws-cdk: CodeCommitSourceAction tries to add a policy to an imported role
In an attempt to build a cross account codepipeline, I have used CodeCommitSourceAction as follows:
// Tools account
const actionProps: any = {};
// Since `CodeCommitSourceAction` doesn't accept a role (in TypeScript) even though the
// abstract `Action` does, have to pass the role via an object of `any` type.
actionProps.role = Role.fromRoleArn(this, 'code-commit-role', codeCommitRoleArn);
const sourceAction = new CodeCommitSourceAction({
actionName: 'CodeCommit',
repository: codeCommitRepository,
output: sourceOutput,
...actionProps
});
When using Role.fromRoleArn I assume that the role exists, potentially in a different account (it is in a different Dev account). However CodeCommitSourceAction tries to create a policy for it according to its source code https://github.com/awslabs/aws-cdk/blob/master/packages/%40aws-cdk/aws-codepipeline-actions/lib/codecommit/source-action.ts#L95-L105 which results in the following resource in the template:
codecommitrolePolicyC2DD4708:
Type: AWS::IAM::Policy
Properties:
PolicyDocument:
Statement:
- Action:
- codecommit:GetBranch
- codecommit:GetCommit
- codecommit:UploadArchive
- codecommit:GetUploadArchiveStatus
- codecommit:CancelUploadArchive
Effect: Allow
Resource: arn:aws:codecommit:us-west-2:123456789012:repository
Version: "2012-10-17"
PolicyName: codecommitrolePolicyC2DD4708
Roles:
- ToolsAcctCodePipelineCodeCommitRole
Metadata:
aws:cdk:path: ToolsCodePipelineStack/code-commit-role/Policy/Resource
This fails because ToolsAcctCodePipelineCodeCommitRole, obviously, doesn't exist in this Tools account. It is in the Dev account.
I think CodeCommitSourceAction should be able to distinguish if the role is imported or not and add only if the role is auto created by the same account.
All 13 comments
Thanks for reporting @kadishmal .
@rix0rrr is this a consequence of the recent change to add Policies to imported Roles?
I have the same. Policies are being added to the imported roles.
I created roles and pipeline with sceptre that work for sceptre. When I modify the infrastructure build to use cdk deploy, I get this error "AccessDenied: Cross-account pass role is not allowed ", so something in the cdk deploy is looking for a missing policy in the cross-account imported role, or you've hard-coded that error in the cdk deploy? idk
I'm using this: cdk deploy --path-metadata=false --role-arn=$rolearn --app "node bin/$env/event-guardduty.js" --output=templates
where $rolearn is the arn of the role in the other account. Is that the wrong way to do this?
I don't think the two are related @cbrothersnow .
"AccessDenied: Cross-account pass role is not allowed "
That's an IAM error, not a CDK error. We definitely don't do that validation in the CDK.
I'm afraid what you're trying to do can't be achieved in IAM (unless I'm missing something).
It’s what I do in Sceptre:
sceptre $sceptre_var --var "iam_role=$role" launch-stack $acct $stack
So I thought it would be the same with CDK. I created a pipeline using Sceptre with imported roles created by Sceptre in both the same account and the cross account. Within that Sceptre pipeline I had a codebuild with CDK shell that works great if the role is in the same account, but gets that error message if the role is in a cross account.
That same pipeline created with Sceptre works both same account and cross account with a Sceptre codebuild using the above statement.
I had already tried creating cross account roles with CDK, then importing those roles into a pipeline created with CDK. The deploy of the CDK created pipeline attached policy statements both to my project role and my cross account role in the same account. I get the same AccessDenied message with this CDK pipeline.
I tried using the roles created and modified by the CDK pipeline in the Sceptre pipeline and I get a similar message trying to deploy with Sceptre.
I’ve tried everything I can think of, although it’s totally possible the problem is trying to do CDK the same way as Sceptre. I don’t know any other way.
I want a CodePipeline in a build account with the CodeCommit, that creates and launches CloudFormation templates in a dev or prod account, as per the AWS Whitepaper describing cross account deploys. Is it something with KMS possibly?
Carol Brothers
Senior DevOps Engineer
[signature_193641752]
Email: carol.[email protected]
Phone: (510) 587-6224
University of California, Office of the President
300 Lakeside Drive, 12th floor, 12216
Oakland, CA 94612
[Title: LinkedIn - Description: LinkedIn icon]https://www.linkedin.com/in/carolbrothers
From: Adam Ruka notifications@github.com
Reply-To: aws/aws-cdk reply@reply.github.com
Date: Friday, July 12, 2019 at 10:39 AM
To: aws/aws-cdk aws-cdk@noreply.github.com
Cc: Carol Brothers Carol.Brothers@ucop.edu, Mention mention@noreply.github.com
Subject: Re: [aws/aws-cdk] CodeCommitSourceAction tries to add a policy to an imported role (#3025)
I don't think the two are related @cbrothersnowhttps://github.com/cbrothersnow .
"AccessDenied: Cross-account pass role is not allowed "
That's an IAM error, not a CDK error. We definitely don't do that validation in the CDK.
I'm afraid what you're trying to do can't be achieved in IAM (unless I'm missing something).
—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHubhttps://github.com/aws/aws-cdk/issues/3025?email_source=notifications&email_token=AK5UG7XPAD2LSJAN3VKR7ZDP7C6UHA5CNFSM4H23ZPP2YY3PNVWWK3TUL52HS4DFVREXG43VMVBW63LNMVXHJKTDN5WW2ZLOORPWSZGODZ2M5QI#issuecomment-510971585, or mute the threadhttps://github.com/notifications/unsubscribe-auth/AK5UG7QVPHK3XTHUUQQID6DP7C6UHANCNFSM4H23ZPPQ.
We are facing exactly the same issue while writing a cross-account pipeline. We are facing it in CloudFormationCreateReplaceChangeSetAction. Is there any workaround this issue before it is fixed?
Facing the same issue when importing ecs execution role. Although the role has the permissions, the template produced by cdk attempts to attach a policy with all the ecs permissions (as well as log stream permissions, because I use them elsewhere on the template). If you're importing a role, you should have the option of not adding new permissions to said role. Highly applicable to accounts that don't have permissions to create/modify roles.
I finally got this working, and it's not at all an issue with CDK. Sceptre must do some "magic" when it does a sceptre deploy with the kms keys. The problem was just my misunderstanding of how to create a cross account pipeline. The first thing I did was remove imported roles and let CDK do it's thing. Then I added cross account stuff to the roles. The final piece for me was realizing I needed to put the custom encryption key in the artifact bucket, as well as in the CodeBuild project phase. Figuring it out little by little.
I'm having the same problem described here.
I am using CDK to set up a CodePipeline where its deployment stage deploys the application (a CF template) to another AWS account.
To achieve this, I’m importing an existing IAM role that’s in the deployment account using Role.fromRoleARN() and then setting the role and the deploymentRole properties of CloudFormationCreateUpdateStackActionProps construct to the imported IAM role.
The CDK synthesised template specifies a policy and attaches it to the imported role, hence failing the CloudFormation deploy.
same exact issue here, I'm importing a role using the arn. This role is a cross account role, but CDK seems to be adding a policy to this and also assumes that the cross account role is present in the current account. The only way I have gotten to this to work is to let cdk synthesize the template. Manually the remove the cross account policy. and then deploy using aws cloudformation deploy.
This is on cdk 1.1. Note that similar code works well on cdk v0.34
I got the same issue, and I am switching back to serverless framework... I will probably use this framework once its more matured.
Sorry to the poor experience @kiranch2004 . If you need some help diagnosing the issue, let me know.
Dear @skinny85,
I'm still having some problems deploying a codepipeline into AWS with GitHub Source with CDK.
The problem is that i created the roles before in an another CDK stack. It contains a "build", "buildProject", "deploy" and "pipeline" role with the required permissions.
I want to use these 4 roles for all cicd pipeline for all microservices because i don't want to create new roles for each pipeline.
But when i import the roles then CDK tries to attach a policy to it which contains the same permissions as i gave to the role before.
How can i avoid such a behaviour?
Proof:
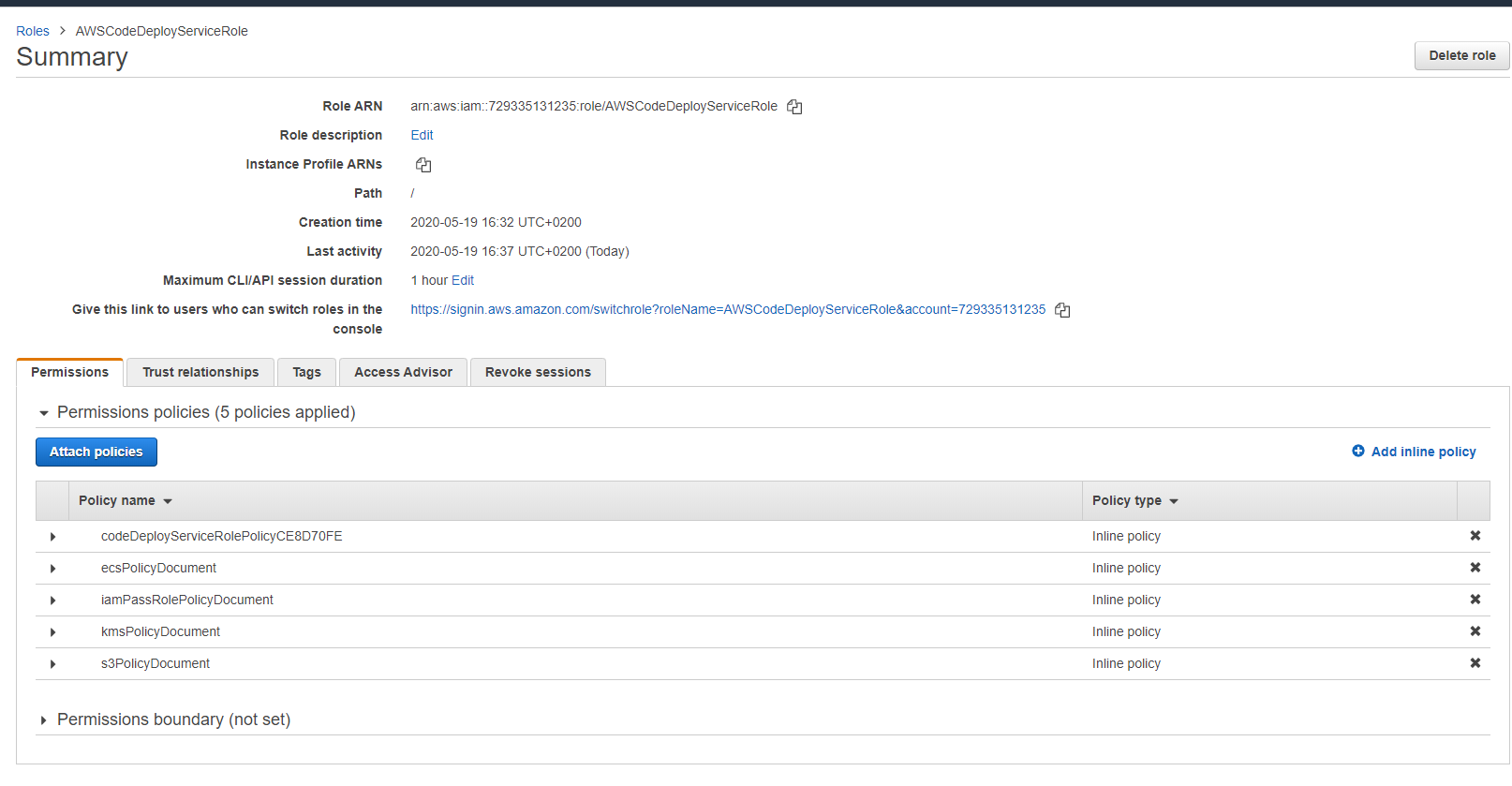
Thanks in advance.
@TamasBartosMentor when importing the Roles, you should pass the mutable parameter as false to the last argument of the call to fromRoleArn: https://docs.aws.amazon.com/cdk/api/latest/docs/@aws-cdk_aws-iam.Role.html#static-from-wbr-role-wbr-arnscope-id-rolearn-options . For example, in TypeScript:
const myRole = iam.Role.fromRoleArn(this, 'MyRole', 'arn:aws:iam::123456789012:role/MyRole', {
mutable: false,
});