Amplify-js: Can we refresh token sooner
* Which Category is your question related to? *
Auth
* What AWS Services are you utilizing? *
E.g. Cognito
* Provide additional details e.g. code snippets *
We are using Amplify for authentication to our Angular app with Cognito User Pool, sometimes our user is getting access token has expired error. We are trying to figure out a solution to allow refresh token easier instead of extract 1h. Let's say if we logged at 10 am then the token is refreshing at 11 am, we saw that driftLock stored in the storage is 0.
Is there any way to allow refreshing access token easier i.e. before 10mins?
We are using the latest version of Angular and Amplify
All 11 comments
This doesn't directly answer your question, but I believe if you add this line:
//before your code, inside an async function
await Auth.currentSession();
It will refresh the tokens if they have expired. Then your code can proceed as normal with fresh tokens. I'm sure an Amplify dev will correct me if I'm wrong :P
Yeah, we are doing likes this since we are using Angular interceptor to get the access token and add to HTTP request header, but access token has expired error still occur. Also, that error is rarely happening and hard to reproduce.
Basically, Amplify does have a job to auto refresh token, but right now it seems doesn't refresh ahead of expiration time
Oh I see.
I checked the AuthClass and didn't see a method for forcing a token refresh before the expiry, so the Amplify team will probably have to add a method for that or you'd have to manually send the refresh token to the TOKENS endpoint and grab new tokens, then inject them into a new service client and execute your request. I don't know if you can inject them into the global AWS client directly without interfering with the auto-token refrsh functionality.
You can probably temporarily ameliorate this problem just by increasing the max session time for the authenticated role in your Cognito IdP though.
Edit: actually instead of manually constructing the URI and sending the refresh token to the TOKEN endpoint, it'd probably be easier to import the cognito sdk and pass the refresh token into the IntiateAuth API. Then, again, inject those into your service client credential's object before making your request.
Well, access token and id token valid within 1h and cannot be changed. Your solution might work, but it add complexity, amplify does refresh, so we just need to adjust function to refresh it on time, maybe add a new prop
@hoang-innomizetech are you sure that the max role duration is 1 hour? I think that's the default. I don't know if Amplify supports setting the DurationsSecond parameter for the internal authentication logic.
@elorzafe does Amp support DurationSeconds, and if not is there any way to monkey patch OP's code to get them unblocked?
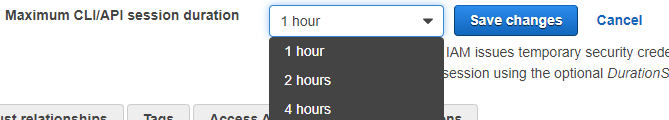
Edit: nvm, didn't realize Cognito had a hard limit of 1 hour in id token (and presumably access token). Well, you could still refresh your access token manually on a setInterval. I don't know how to inject them into Amplify and/or the S3 service client and how that affects an upload that's already in progress.
Maybe OP could write a module that generates pre-signed S3 urls and uses those for the upload?
https://docs.aws.amazon.com/AWSJavaScriptSDK/latest/AWS/S3.html#getSignedUrlPromise-property
@hoang-innomizetech I am looking the clock skew problem now, we want to have a solution for this, there are other related issues #3719 #3699 #2014
This issue has been automatically marked as stale because it has not had recent activity. It will be closed if no further activity occurs. Thank you for your contributions.
This is happening for me too. Seem to get logged out for no apparent reason.
It seems they're opened a PR #4205
This issue has been automatically marked as stale because it has not had recent activity. It will be closed if no further activity occurs. Thank you for your contributions.
This issue has been automatically closed because of inactivity. Please open a new issue if are still encountering problems.
Most helpful comment
@hoang-innomizetech I am looking the clock skew problem now, we want to have a solution for this, there are other related issues #3719 #3699 #2014