Amplify-js: Cognito authenticateUser security hole
Do you want to request a feature or report a bug?
Bug (security hole). I think this is something that needs to be fixed in Cognito and not the SDK, but I figured I'd open this issue here just in case. I'm also going to post in the AWS Developer Forums when it lets me.
What is the current behavior?
As it was already mentioned in this forum discussion thread and in this issue comment, returning specific error messages on sign in failure exposes a security hole, allowing an attacker to enumerate users.
What is the expected behavior?
As per OWASP's recommendation:
[Cognito] should respond with a generic error message regardless of whether the user ID or password was incorrect.
A generic "Incorrect username or password." error message would be the best.
Which versions of Amplify, and which browser / OS are affected by this issue? Did this work in previous versions?
N/A
Thanks.
All 17 comments
@olistic thanks for reporting. We will talk to Cognito team about this issue.
@yuntuowang what do you think?
I will call this out with Cognito team.
@yuntuowang thanks.
Is there any update on this?
Hi,
There are numbers of concerns regarding this on github/aws forums (see https://forums.aws.amazon.com/message.jspa?messageID=749743#749743) so it will be good to have AWS standing on this -
hello,
really enjoying doing full stack dev with amplify et al keep up the great work. we too see that the more generic response would be better ala iam for aws console
any update?
thanks
Bumping this, as it is a security issue on every website that calls Cognito directly from the browser. Even if you intercept the error return and write your own UI message, it is trivial to open the Console and see the message returned from Cognito.
The sad thing is that this was added as a "feature" by someone on the Cognito team...
It's still an issue. Not really a good thing to let an attacker know a particular username exists and only the password remains to be exploited. This must be fixed ASAP.
cc @yuntuowang
Why is this problem neglected for a long time?
Does AWS neglect security?
Do users who use Cognito for their business correctly recognize this threat?
As many others here I consider this highly problematic.
Not "only" for the security of the app, but in apps/services where the user's email address is being used as username (and many services do that) it might also violate the GDPR, since it is leaking information about natural persons, as it is easily possible to find out if a certain person is using a certain app/service by simply typing their email address into the logon field and hit enter.
This issue has been automatically marked as stale because it has not had recent activity. It will be closed if no further activity occurs. Thank you for your contributions.
I think this issue is important to resolve because as outlined above, it might violate GDPR and the OWASP guidelines.
This is a serious security hole that needs to be addressed. This issue has been open for over 1 year.
This issue was addressed in a recent release of Amazon Cognito, see this doc for more details.
Per the above comment by the Cognito team this issue was addressed. Closing but please let us know if there are any further issues.
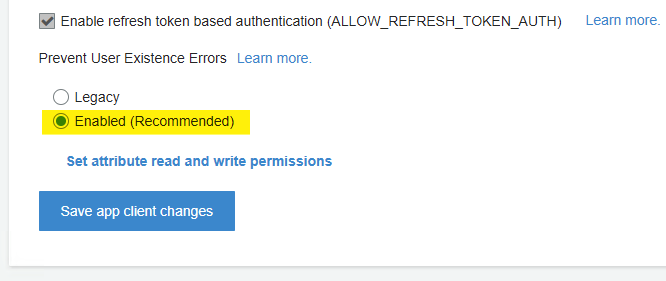
For others arriving here from search engines, here is the documentation explaining how to prevent UserNotFoundException errors from Cognito:
Basically, go to your User Pool in Cognito, select App clients, click Show Details, and enable Prevent User Existence Errors:
Most helpful comment
For others arriving here from search engines, here is the documentation explaining how to prevent
UserNotFoundExceptionerrors from Cognito:Basically, go to your
User Poolin Cognito, selectApp clients, clickShow Details, and enablePrevent User Existence Errors: