Amplify-js: missing credentials in config (can't refresh login token)
Hi,
As you may know, after an hour the login token will expire.
So, after an hour (when AWS.config.credentials.needsRefresh() is true) I'm trying to refresh the cognito user's session, which does work for the first hour I'm calling it, but after 2 hours I'm receiving an error, although the exact same routine, as 1 hour before (when it successfully refreshed) takes place.
Can the login token be refreshed only once?
This is my code:
if(AWS.config.credentials.needsRefresh()) {
clearInterval(messwerte_updaten);
AWS.config.credentials.refresh(function (err) {
if (err) {
console.log(err);
}
else {
callLambda();
}
});
}
The error i'm receiving is:
missing credentials in config
could not load credentials from constructor
Invalid login token. Token expired: 1446742058 >= 1446727732
I'm stuck at this problem for 5 days now, tried everything from Stackoverflow, AWS Docs and GitHub but nothing works for me...so helpful answers are highly appreciated.
thanks in advance.
All 16 comments
Hi @tipsfedora
Amplify can handle credentials for you (this would be the recommended way), looks like you are currently using the aws-sdk directly.
In that case, you could try with the getPromise() method of the credentials (no need to create a new instance of AWS.CognitoIdentityCredentials).
await AWS.config.credentials.getPromise();
call_Lambda();
Gonna try it out tomorrow at work, will report the outcome here.
Thanks so far.
Doesn't work.
Error Messages:
CredentialsError: Missing credentials in config
message: "Could not load credentials from constructor", code: "CredentialsError",
NotAuthorizedException: Invalid login token. Token expired: 1520330904 >= 1520327627
Updated the question, still going.
Hi @tipsfedora, login tokens can be refreshed many times as long as refreshToken is valid. Can you double check when you call "cognitoUser.refreshSession(cognitoUser.signInUserSession.refreshToken, (err, session)", is the refreshToken here not missing?
The refreshToken isn't missing. This is what i receive when i console.log() the refreshToken:
Object { token: "eyJjdHkiOiJKV1QiLCJlbmMiOiJBMjU2R0NNIiwiYWxnIjoiUlNBLU9BRVAifQ.ORWdUFDu5ZlGv2YZnw8xLCTSM_oKtAR_8xTptpDOpdfsi_E5XWwuaryyVdtPdxk6eLd4bg6hBkxP68EYNR3dpQ4iFdwF3TXupzubqzw0ri8QfvqGaXol5GbZAX7jRzwdZniBjTkgajDieCai9B706QWjTHWFGh_FLgFZO996tWl1393fwZthqNdqo8YFOrG9TxNZB1gbboeahM24jRXxQc4x3QvqMlr8uPn1BXir6eVT5iYHN7Asa0cEX8SOTla42qk-uaF_0ZG8MN9QoX8L_xwEu0hsm-yCK7PMAT6DCKr_1Y0Shb_IgjCKkoy192MgZZhi68ZgI23reDkxzA0lRw.nXVlQoC1ddXdSCKZ.7gnF4AK0yevFOWB0Imt2h5cKnFfs8hMIXFcACoP1R7zuTSJQL4NCPTKnwEdEjlRYoJ9JG7a0oaCTe05moCiT0pqneMqb3mufH_hB-X-Kd2ZSkd8S9N0mbtrWUjOm7NX_2rDpIoK9inZEhsw8BqfATX9lULW2Q-JRWO-4Q4QHSYWM3dPvRMwbe8neQH59oA8a_heYJ2HgZBad2Ydl-U89dettbHTGuXIECF0sV5mqDanFP66A8Ie14GOBaSQfbtuzBjmZJNi7S07ZIrlVy4vusbh-69NAxCF8fP7jdnq-FrUTvgBYyIhYhMTErYK7nf(.....)
As its mentioned in the AWS docs, the refreshToken is valid for 30 days, so i shouldn't have any problems refreshing the login token.
After 1 hour i can successfully refresh my login token, but after 2 hours i suddenly receive an error.
@tipsfedora when using amplify, you need to be sure to configure it with your cognito identity pool ID and appropriate configurations (if you are not using awsmobile-cli/mobile hub). The identity pool needs to have appropriate IAM roles i.e. authenticated / unauthenticated for what you want to do. At that point once your configure the library, it will handle refreshing your credentials for your users, see here for example.
You would just need to make sure you configure Amplify first, prior to making any calls to anything like API or similar.
I'm not using AWS amplify. I'm using AWS Cognito and AWS Cognito Identity and some other libaries which i got from here: https://sdk.amazonaws.com/builder/js/
Since I'm working on a browser side only app, I'm using plain javascript. can you implement aws amplify in plain js/html apps like<script src="aws-amplify.js"></script>?
Hi @tipsfedora, I think you can use amazon-cognito-identity-js package directly which is under amplify repo: https://github.com/aws/aws-amplify/tree/master/packages/amazon-cognito-identity-js
You can import the SDK by ""
After almost 2 weeks i finally solved it.
The problem was that i didn't update theAWS.config.credentials Object with the new Id Token.
In case someones reading this and is having similar issues, do the following:
You need the refresh token to receive a new id token. Now, update the AWS.config.credentials object with the new token.
here is an example of my code, which runs smoothly!
refresh_token = session.getRefreshToken(); // you'll get session from calling cognitoUser.getSession()
if (AWS.config.credentials.needsRefresh()) {
cognitoUser.refreshSession(refresh_token, (err, session) => {
if(err) {
console.log(err);
}
else {
AWS.config.credentials.params.Logins['cognito-idp.<YOUR-REGION>.amazonaws.com/<YOUR_USER_POOL_ID>'] = session.getIdToken().getJwtToken();
AWS.config.credentials.refresh((err)=> {
if(err) {
console.log(err);
}
else{
console.log("TOKEN SUCCESSFULLY UPDATED");
}
});
}
});
}
Since, there are more people facing this issue, I'd be really happy if this gets added into the AWS Amplify documentation!
Hi @tipsfedora, glad it worked and thank you so much for posting your solution.
Hi @mlabieniec, can you work on putting this solution into Amplify doc in a suitable way? Thanks a lot!!
Closing.
@david114 thanx a ton for going through this so I don't have to.
Note to AWS team:
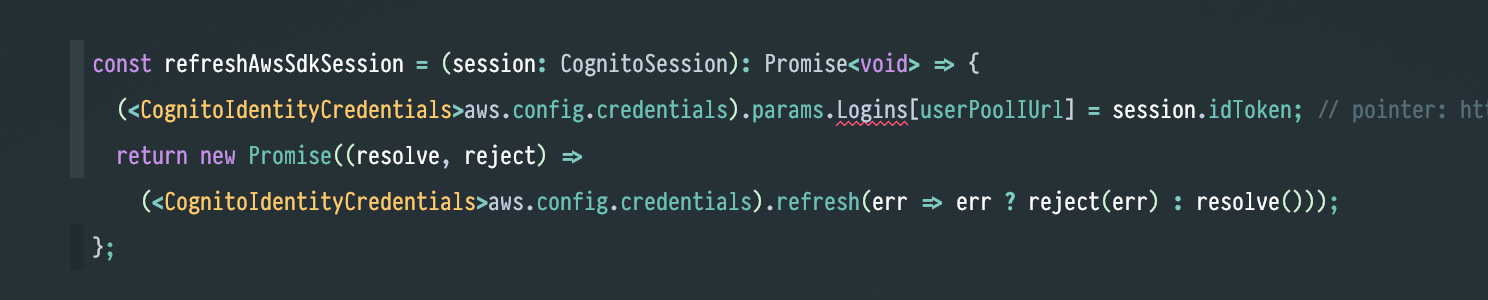
Logins is not part of the params type.
@david114 thank you so much for resolving and posting here. We struggled for months with this with AWS in 2017. Our solution finally was to place a fix in the aws-sdk code to ensure the correct tokens were passed for huge multipart uploads. Integrated this fix into our code base over the weekend, works a charm!
@paolavness you're very welcome.
I am using AWS.config.crendentials.update() to update my crendentials and i want latest cognitoIdentityId so Is it necessary to call get() method of AWS.config.crendentials to get latest cognitoIdentityId because it is taking too much time like 6-7 secs
Is there any way to avoid get() call?
Most helpful comment
After almost 2 weeks i finally solved it.
The problem was that i didn't update the
AWS.config.credentialsObject with the new Id Token.In case someones reading this and is having similar issues, do the following:
You need the refresh token to receive a new id token. Now, update the
AWS.config.credentialsobject with the new token.here is an example of my code, which runs smoothly!
Since, there are more people facing this issue, I'd be really happy if this gets added into the AWS Amplify documentation!