Amplify-cli: error message when using amplify push && amplify codegen models "@auth directive with 'userPools' provider found, but the project has no Cognito User Pools authentication provider configured."
Describe the bug
When trying to build a graphql API that will allow authenticated fields as well as a publicly accessible fields in order to populate a public web page (e.g., blog posts);
Amplify CLI Version
4.22.0
To Reproduce
Steps to reproduce the behavior or terminal output if applicable
$> amplify init
? Enter a name for the project sample_project
? Enter a name for the environment dev
? Choose your default editor: Atom Editor
? Choose the type of app that you're building javascript
Please tell us about your project
? What javascript framework are you using angular
? Source Directory Path: src
? Distribution Directory Path: dist
? Build Command: npm run-script build
? Start Command: ng serve
Using default provider awscloudformation
$> amplify push$> amplify add auth
$> amplify add auth
Using service: Cognito, provided by: awscloudformation
The current configured provider is Amazon Cognito.
Do you want to use the default authentication and security configuration? Manual configuration
Select the authentication/authorization services that you want to use: User Sign-Up, Sign-In, connected with AWS IAM controls (Enables per-user Storage features for images or other content, Analytics, and more)
Please provide a friendly name for your resource that will be used to label this category in the project: testdef8faa7def8faa7
Please enter a name for your identity pool. testdef8faa7_identitypool_def8faa7
Allow unauthenticated logins? (Provides scoped down permissions that you can control via AWS IAM) Yes
Do you want to enable 3rd party authentication providers in your identity pool? No
Please provide a name for your user pool: testdef8faa7_userpool_def8faa7
Warning: you will not be able to edit these selections.
How do you want users to be able to sign in? Email
Do you want to add User Pool Groups? Yes
? Provide a name for your user pool group: test_group
? Do you want to add another User Pool Group No
✔ Sort the user pool groups in order of preference · test_group
Do you want to add an admin queries API? No
Multifactor authentication (MFA) user login options: OFF
Email based user registration/forgot password: Enabled (Requires per-user email entry at registration)
Please specify an email verification subject: Your verification code
Please specify an email verification message: Your verification code is {####}
Do you want to override the default password policy for this User Pool? No
Warning: you will not be able to edit these selections.
What attributes are required for signing up? Email
Specify the app's refresh token expiration period (in days): 30
Do you want to specify the user attributes this app can read and write? No
Do you want to enable any of the following capabilities?
Do you want to use an OAuth flow? No
? Do you want to configure Lambda Triggers for Cognito? No
Successfully added resource testdef8faa7def8faa7 locally
$> amplify push- Cloudformation succeeded$> amplify add apiw/IAM
$> amplify add api
? Please select from one of the below mentioned services: GraphQL
? Provide API name: sample_project
? Choose the default authorization type for the API IAM
? Do you want to configure advanced settings for the GraphQL API Yes, I want to make some additional changes.
? Configure additional auth types? No
? Configure conflict detection? No
? Do you have an annotated GraphQL schema? No
? Do you want a guided schema creation? Yes
? What best describes your project: Single object with fields (e.g., “Todo” with ID, name, description)
? Do you want to edit the schema now? No
The following types do not have '@auth' enabled. Consider using @auth with @model
- Todo
Learn more about @auth here: https://docs.amplify.aws/cli/graphql-transformer/directives#auth
GraphQL schema compiled successfully.
$> amplify push
? Do you want to update code for your updated GraphQL API Yes
? Do you want to generate GraphQL statements (queries, mutations and subscription) based on your schema types?
This will overwrite your current graphql queries, mutations and subscriptions Yes
⠏ Updating resources in the cloud. This may take a few minutes...
$> amplify update apiw/ IAM && UserPools
? Please select from one of the below mentioned services: GraphQL
? Select from the options below Walkthrough all configurations
? Choose the default authorization type for the API IAM
? Do you want to configure advanced settings for the GraphQL API Yes, I want to make some additional changes.
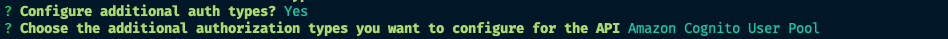
? Configure additional auth types? Yes
? Choose the additional authorization types you want to configure for the API
? Configure conflict detection? No
The following types do not have '@auth' enabled. Consider using @auth with @model
- Todo
Learn more about @auth here: https://docs.amplify.aws/cli/graphql-transformer/directives#auth
GraphQL schema compiled successfully.
- add @auth block to schema.graphql
type Todo @model
@auth( rules: [
{ allow: owner },
{ allow: public, operations: [read], provider: iam }
])
{
id: ID!
name: String!
description: String
}
$> amplify push
✔ Successfully pulled backend environment dev from the cloud.
Current Environment: dev
| Category | Resource name | Operation | Provider plugin |
| -------- | -------------------------- | --------- | ----------------- |
| Api | sample_project | Update | awscloudformation |
| Auth | userPoolGroups | No Change | awscloudformation |
| Auth | testdef8faa7def8faa7 | No Change | awscloudformation |
? Are you sure you want to continue? Yes
✖ An error occurred when pushing the resources to the cloud
@auth directive with 'userPools' provider found, but the project has no Cognito User Pools authentication provider configured.
Expected behavior
Expect for defined IAM and Cognito User Pools to be setup and available for deployment; successful push of new scheme with valid IAM and Cognito auth methods;
Desktop (please complete the following information):
Ubuntu
- Node Version: v10.19.0
Additional context
After replicating steps, amplify/backend/amplify-meta.json is missing any entries in the additionalAuthenticationProviders:
"api": {
"sample_project": {
"service": "AppSync",
"providerPlugin": "awscloudformation",
"output": {
"authConfig": {
"additionalAuthenticationProviders": [],
"defaultAuthentication": {
"authenticationType": "AWS_IAM"
}
},
"GraphQLAPIIdOutput": "fodkrejm2vgdzkecgmkoyrz2tm",
"GraphQLAPIEndpointOutput": "https://owbys52sqvd4zj57tgfpsz6ste.appsync-api.us-east-1.amazonaws.com/graphql"
},
"providerMetadata": {
"s3TemplateURL": "https://s3.amazonaws.com/amplify-sample-dev-151849-deployment/amplify-cfn-templates/api/cloudformation-template.json",
"logicalId": "apisample"
},
"lastPushTimeStamp": "2020-07-02T20:50:38.938Z",
"lastPushDirHash": "jSvBewBN3ApZZxGVJfYrlbRiN+I="
}
}
All 6 comments
manually adding:
{
"authenticationType": "AMAZON_COGNITO_USER_POOLS",
"userPoolConfig": {
"userPoolId": "us-east-1_CNhehjx0O"
}
}
to the amplify-meta.json - API -> output -> authConfig -> additionalAuthenticationProviders section results in a successful build and push;
@jasimmonsv you could also update the API using amplify update api command and add additional auth type to your API.
@yuth Step 7 is amplify update api; please reopen this ticket;
That command is apparently not committing the configuration to the right file.
Sorry I missed that part
When choosing additional auth type, you will have to select Amazon Congnito User Pool by pressing <space bar> and then <return>, pressing <return> key does not select the any values.

son of a.... :facepalm:
thank you @yuth... this whole time
This worked for me. Thank you! I just encountered this.
Most helpful comment
Sorry I missed that part
When choosing additional auth type, you will have to select Amazon Congnito User Pool by pressing
<space bar>and then<return>, pressing<return>key does not select the any values.