Amplify-cli: UpdateRolesWithIDPFunction CREATE_FAILED nodejs8.10
Describe the bug
When I deploy an evvironment for the first time, the cloudformation stack fails to build itself
Amplify CLI Version
4.12.0
To Reproduce
in a new project without team provider file, init and then push api and auth.
Expected behavior
The api and auth stacks should be deployed.
Screenshots
https://i.imgur.com/sQ1dMxt.png
Desktop (please complete the following information):
- OS: Ubuntu 19.10
- Node Version: 12.13
Additional context
I can provide the stacks ARN if needed.
All 42 comments
@simon-lanf Can you check amplify -v and confirm that you're using 4.12.0?
@simon-lanf Can you check
amplify -vand confirm that you're using 4.12.0?
It is. I said in the first post, I used '-v' to find it out.
Here's the output of 'npm -g ls --depth=0'
[...]
├─┬ @aws-amplify/[email protected]
│ ├── @types/[email protected]
│ ├── @types/[email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ ├── [email protected]
│ └── [email protected]
[...]
@simon-lanf Can you check your amplify/awscloudformation/nested-cloudformation-stack.yml file and see if the Node runtime is set to 8.10 - and change it to "Runtime": "nodejs10.x" and then try pushing?
@kaustavghosh06 It already is node10.
> cat amplify/backend/awscloudformation/nested-cloudformation-stack.yml | grep 'nodejs'
"Runtime": "nodejs10.x"
The template that's loaded for the stack is generated by AWS, has the following description: "Root stack for the Amplify AWS CloudFormation provider"
Here's the content:
{
"AWSTemplateFormatVersion" : "2010-09-09",
"Description" : "Root stack for the Amplify AWS CloudFormation provider",
"Parameters":{
"DeploymentBucketName":{
"Description": "Name of the common deployment bucket provided by the parent stack",
"Type": "String",
"Default": "DeploymentBucket"
},
"AuthRoleName":{
"Type": "String",
"Default": "AuthRoleName"
},
"UnauthRoleName":{
"Type": "String",
"Default": "UnauthRoleName"
}
},
"Resources": {
"DeploymentBucket" : {
"Type" : "AWS::S3::Bucket",
"DeletionPolicy" : "Retain",
"Properties": {
"BucketName": {"Ref": "DeploymentBucketName"}
}
},
"AuthRole": {
"Type": "AWS::IAM::Role",
"Properties": {
"RoleName": {"Ref": "AuthRoleName"},
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Deny",
"Principal": {
"Federated": "cognito-identity.amazonaws.com"
},
"Action": "sts:AssumeRoleWithWebIdentity"
}
]
}
}
},
"UnauthRole": {
"Type": "AWS::IAM::Role",
"Properties": {
"RoleName": {"Ref": "UnauthRoleName"},
"AssumeRolePolicyDocument":{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Deny",
"Principal": {
"Federated": "cognito-identity.amazonaws.com"
},
"Action": "sts:AssumeRoleWithWebIdentity"
}
]
}
}
}
},
"Outputs" : {
"Region": {
"Description": "CloudFormation provider root stack Region",
"Value": {"Ref": "AWS::Region"},
"Export": {
"Name" : { "Fn::Sub" : "${AWS::StackName}-Region"}
}
},
"StackName": {
"Description": "CloudFormation provider root stack ID",
"Value": {"Ref": "AWS::StackName"},
"Export": {
"Name" : { "Fn::Sub" : "${AWS::StackName}-StackName"}
}
},
"StackId": {
"Description": "CloudFormation provider root stack name",
"Value": {"Ref": "AWS::StackId"},
"Export": {
"Name" : { "Fn::Sub" : "${AWS::StackName}-StackId"}
}
},
"DeploymentBucketName": {
"Description": "CloudFormation provider root stack deployment bucket name",
"Value": {"Ref": "DeploymentBucketName"},
"Export": {
"Name" : { "Fn::Sub" : "${AWS::StackName}-DeploymentBucketName"}
}
},
"AuthRoleArn": {
"Value": {"Fn::GetAtt": ["AuthRole", "Arn"]}
},
"UnauthRoleArn": {
"Value": {"Fn::GetAtt": ["UnauthRole", "Arn"]}
},
"AuthRoleName": {
"Value": {"Ref": "AuthRole"}
},
"UnauthRoleName": {
"Value": {"Ref": "UnauthRole"}
}
}
}
Can you try pushing again from your local using amplify push and check if you see the same error?
That's precisely the command I use. It tells me this:
Current Environment: staging
| Category | Resource name | Operation | Provider plugin |
| -------- | ------------- | --------- | ----------------- |
| Auth | auth | Create | awscloudformation |
| Api | oawebappapi | Create | awscloudformation |
? Are you sure you want to continue? Yes
And the stack fails to build.
Super weird, not able to reproduce the same behavior with v4.12.0 on my machine.
In all of your project, can you grep "8.10" and see if you can find any instance of it?
Unless the CLI version is picking up an older version of the "amplify-provider-awscloudformation" pacakge - the CLI shouldn't be using 8.10 node runtime anymore. Can you also try running amplify plugin scan to re-scan all the dependent packages for the CLI - including the ""amplify-provider-awscloudformation" package and try pushing again.
> amplify status
Current Environment: prod
| Category | Resource name | Operation | Provider plugin |
| -------- | ------------- | --------- | ----------------- |
| Auth | auth | Create | awscloudformation |
| Api | oawebappapi | Create | awscloudformation |
> grep -R '8\.10' .
>
@kaustavghosh06 I've found the actual template causing the problem:
{
"AWSTemplateFormatVersion": "2010-09-09",
"Description": "Root stack for the Amplify AWS CloudFormation provider",
"Parameters": {
"DeploymentBucketName": {
"Description": "Name of the common deployment bucket provided by the parent stack",
"Type": "String",
"Default": "DeploymentBucket"
},
"AuthRoleName": {
"Type": "String",
"Default": "AuthRoleName"
},
"UnauthRoleName": {
"Type": "String",
"Default": "UnauthRoleName"
}
},
"Resources": {
"DeploymentBucket": {
"Type": "AWS::S3::Bucket",
"DeletionPolicy": "Retain",
"Properties": {
"BucketName": {
"Ref": "DeploymentBucketName"
}
}
},
"AuthRole": {
"Type": "AWS::IAM::Role",
"Properties": {
"RoleName": {
"Ref": "AuthRoleName"
},
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Deny",
"Principal": {
"Federated": "cognito-identity.amazonaws.com"
},
"Action": "sts:AssumeRoleWithWebIdentity"
}
]
}
}
},
"UnauthRole": {
"Type": "AWS::IAM::Role",
"Properties": {
"RoleName": {
"Ref": "UnauthRoleName"
},
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Deny",
"Principal": {
"Federated": "cognito-identity.amazonaws.com"
},
"Action": "sts:AssumeRoleWithWebIdentity"
}
]
}
}
},
"authauth": {
"Type": "AWS::CloudFormation::Stack",
"Properties": {
"TemplateURL": "https://s3.amazonaws.com/amplify-oa-web-app-staging-115837-deployment/amplify-cfn-templates/auth/auth-cloudformation-template.yml",
"Parameters": {
"identityPoolName": "oa_web_app_identity_pool",
"allowUnauthenticatedIdentities": false,
"resourceNameTruncated": "auth33ab433b",
"userPoolName": "oa_web_app_user_pool",
"autoVerifiedAttributes": "email",
"mfaConfiguration": "OFF",
"mfaTypes": "SMS Text Message",
"smsAuthenticationMessage": "Your authentication code is {####}",
"smsVerificationMessage": "Your verification code is {####}",
"emailVerificationSubject": "Your OrangeAD verification code",
"emailVerificationMessage": "Your OrangeAD verification code is {####}",
"defaultPasswordPolicy": true,
"passwordPolicyMinLength": 8,
"passwordPolicyCharacters": "",
"requiredAttributes": "email",
"userpoolClientGenerateSecret": true,
"userpoolClientRefreshTokenValidity": 30,
"userpoolClientWriteAttributes": "address,family_name,locale,given_name,name,phone_number,email",
"userpoolClientReadAttributes": "address,email,family_name,locale,given_name,name,phone_number",
"userpoolClientLambdaRole": "auth33ab433b_userpoolclient_lambda_role",
"userpoolClientSetAttributes": true,
"useDefault": "manual",
"authSelections": "identityPoolAndUserPool",
"resourceName": "auth",
"thirdPartyAuth": false,
"userPoolGroups": false,
"adminQueries": false,
"triggers": "{}",
"hostedUI": false,
"userPoolGroupList": "",
"authRoleArn": {
"Fn::GetAtt": [
"AuthRole",
"Arn"
]
},
"unauthRoleArn": {
"Fn::GetAtt": [
"UnauthRole",
"Arn"
]
},
"parentStack": {
"Ref": "AWS::StackId"
},
"permissions": "",
"dependsOn": "",
"env": "staging"
}
}
},
"apioawebappapi": {
"Type": "AWS::CloudFormation::Stack",
"Properties": {
"TemplateURL": "https://s3.amazonaws.com/amplify-oa-web-app-staging-115837-deployment/amplify-cfn-templates/api/cloudformation-template.json",
"Parameters": {
"CreateAPIKey": 0,
"AppSyncApiName": "oawebappapi",
"DynamoDBBillingMode": "PAY_PER_REQUEST",
"DynamoDBEnableServerSideEncryption": "false",
"AuthCognitoUserPoolId": {
"Fn::GetAtt": [
"authauth",
"Outputs.UserPoolId"
]
},
"S3DeploymentBucket": "amplify-oa-web-app-staging-115837-deployment",
"S3DeploymentRootKey": "amplify-appsync-files/df9abd8d0366627660fb900120cd444a7b3f6ed1",
"env": "staging"
}
}
},
"UpdateRolesWithIDPFunction": {
"DependsOn": [
"AuthRole",
"UnauthRole",
"authauth"
],
"Type": "AWS::Lambda::Function",
"Properties": {
"Code": {
"ZipFile": {
"Fn::Join": [
"\n",
[
"const response = require('cfn-response');",
"const aws = require('aws-sdk');",
"let responseData = {};",
"exports.handler = function(event, context) {",
" try {",
" let authRoleName = event.ResourceProperties.authRoleName;",
" let unauthRoleName = event.ResourceProperties.unauthRoleName;",
" let idpId = event.ResourceProperties.idpId;",
" let promises = [];",
" let authParamsJson = { 'Version': '2012-10-17','Statement': [{'Effect': 'Allow','Principal': {'Federated': 'cognito-identity.amazonaws.com'},'Action': 'sts:AssumeRoleWithWebIdentity','Condition': {'StringEquals': {'cognito-identity.amazonaws.com:aud': idpId},'ForAnyValue:StringLike': {'cognito-identity.amazonaws.com:amr': 'authenticated'}}}]};",
" let unauthParamsJson = { 'Version': '2012-10-17','Statement': [{'Effect': 'Allow','Principal': {'Federated': 'cognito-identity.amazonaws.com'},'Action': 'sts:AssumeRoleWithWebIdentity','Condition': {'StringEquals': {'cognito-identity.amazonaws.com:aud': idpId},'ForAnyValue:StringLike': {'cognito-identity.amazonaws.com:amr': 'unauthenticated'}}}]};",
" if (event.RequestType == 'Delete') {",
" delete authParamsJson.Statement.Condition;",
" delete unauthParamsJson.Statement.Condition;",
" let authParams = { PolicyDocument: JSON.stringify(authParamsJson),RoleName: authRoleName};",
" let unauthParams = {PolicyDocument: JSON.stringify(unauthParamsJson),RoleName: unauthRoleName};",
" const iam = new aws.IAM({ apiVersion: '2010-05-08', region: event.ResourceProperties.region});",
" promises.push(iam.updateAssumeRolePolicy(authParams).promise());",
" promises.push(iam.updateAssumeRolePolicy(unauthParams).promise());",
" Promise.all(promises)",
" .then((res) => {",
" console.log(\"delete response data\" + JSON.stringify(res));",
" response.send(event, context, response.SUCCESS, {});",
" });",
" }",
" if (event.RequestType == 'Update' || event.RequestType == 'Create') {",
" const iam = new aws.IAM({ apiVersion: '2010-05-08', region: event.ResourceProperties.region});",
" let authParams = { PolicyDocument: JSON.stringify(authParamsJson),RoleName: authRoleName};",
" let unauthParams = {PolicyDocument: JSON.stringify(unauthParamsJson),RoleName: unauthRoleName};",
" promises.push(iam.updateAssumeRolePolicy(authParams).promise());",
" promises.push(iam.updateAssumeRolePolicy(unauthParams).promise());",
" Promise.all(promises)",
" .then((res) => {",
" console.log(\"createORupdate\" + res);",
" console.log(\"response data\" + JSON.stringify(res));",
" response.send(event, context, response.SUCCESS, {});",
" });",
" }",
" } catch(err) {",
" console.log(err.stack);",
" responseData = {Error: err};",
" response.send(event, context, response.FAILED, responseData);",
" throw err;",
" }",
"};"
]
]
}
},
"Handler": "index.handler",
"Runtime": "nodejs10.x",
"Timeout": "300",
"Role": {
"Fn::GetAtt": [
"UpdateRolesWithIDPFunctionRole",
"Arn"
]
}
}
},
"UpdateRolesWithIDPFunctionOutputs": {
"Type": "Custom::LambdaCallout",
"Properties": {
"ServiceToken": {
"Fn::GetAtt": [
"UpdateRolesWithIDPFunction",
"Arn"
]
},
"region": {
"Ref": "AWS::Region"
},
"idpId": {
"Fn::GetAtt": [
"authauth",
"Outputs.IdentityPoolId"
]
},
"authRoleName": {
"Ref": "AuthRoleName"
},
"unauthRoleName": {
"Ref": "UnauthRoleName"
}
}
},
"UpdateRolesWithIDPFunctionRole": {
"Type": "AWS::IAM::Role",
"Properties": {
"RoleName": {
"Fn::Join": [
"",
[
{
"Ref": "AuthRoleName"
},
"-idp"
]
]
},
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": [
"lambda.amazonaws.com"
]
},
"Action": [
"sts:AssumeRole"
]
}
]
},
"Policies": [
{
"PolicyName": "UpdateRolesWithIDPFunctionPolicy",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"logs:CreateLogGroup",
"logs:CreateLogStream",
"logs:PutLogEvents"
],
"Resource": "arn:aws:logs:*:*:*"
},
{
"Effect": "Allow",
"Action": "iam:UpdateAssumeRolePolicy",
"Resource": {
"Fn::GetAtt": [
"AuthRole",
"Arn"
]
}
},
{
"Effect": "Allow",
"Action": "iam:UpdateAssumeRolePolicy",
"Resource": {
"Fn::GetAtt": [
"UnauthRole",
"Arn"
]
}
}
]
}
}
]
}
}
},
"Outputs": {
"Region": {
"Description": "CloudFormation provider root stack Region",
"Value": {
"Ref": "AWS::Region"
},
"Export": {
"Name": {
"Fn::Sub": "${AWS::StackName}-Region"
}
}
},
"StackName": {
"Description": "CloudFormation provider root stack ID",
"Value": {
"Ref": "AWS::StackName"
},
"Export": {
"Name": {
"Fn::Sub": "${AWS::StackName}-StackName"
}
}
},
"StackId": {
"Description": "CloudFormation provider root stack name",
"Value": {
"Ref": "AWS::StackId"
},
"Export": {
"Name": {
"Fn::Sub": "${AWS::StackName}-StackId"
}
}
},
"DeploymentBucketName": {
"Description": "CloudFormation provider root stack deployment bucket name",
"Value": {
"Ref": "DeploymentBucketName"
},
"Export": {
"Name": {
"Fn::Sub": "${AWS::StackName}-DeploymentBucketName"
}
}
},
"AuthRoleArn": {
"Value": {
"Fn::GetAtt": [
"AuthRole",
"Arn"
]
}
},
"UnauthRoleArn": {
"Value": {
"Fn::GetAtt": [
"UnauthRole",
"Arn"
]
}
},
"AuthRoleName": {
"Value": {
"Ref": "AuthRole"
}
},
"UnauthRoleName": {
"Value": {
"Ref": "UnauthRole"
}
}
}
}
Notice the Node version for the lambda function resource UpdateRolesWithIDPFunction.
I'm trying on a different computer right now. My whole setup is a CloudFormation stack (code repo, amplify app, etc...). I'm deleting it all right now. Then I will recreate it and re-do everything on a new computer that never had node installed on it before, I'll come back with the results.
@simon-lanf Please let me know if you were able to reproduce. Thanks!
I'm having the same issue.
I'm running Amplify CLI 4.12.0 on MacOS 10.15.2
I've set up an example Vue project, added Amplify, added an api and auth with the default config and when I push my git branch to trigger the automated deploy I get the following stack:
2020-01-16T23:17:22.553Z [INFO]: CREATE_FAILED
UpdateRolesWithIDPFunction AWS::Lambda::Function
Thu Jan 16 2020 23:17:21 GMT+0000 (Coordinated Universal Time)
The runtime parameter of nodejs8.10 is no longer supported for creating or updating AWS Lambda functions. We recommend you use the new runtime (nodejs12.x) while creating or updating functions.
(Service: AWSLambdaInternal; Status Code: 400;
Error Code: InvalidParameterValueException;
Request ID: 9aee33c7-ab62-4bed-ab44-2214e937b049)
If I remove auth and push the changes to my repo, the automated build is successful.
Also, curiously for me, the build appears to work when I run amplify push.
I have the same UpdateRolesWithIDPFunction config as the OP.
I've spent ages looking into this issue over the past couple of days to no avail. This article is along the same lines, but explicitly says that if you're running the latest version of Amplify CLI - which we are - that it isn't relevant: https://aws-amplify.github.io/docs/cli/lambda-node-version-update
Any help would be greatly appreciated!
@jonperryxlm can you tell me what is the exact command you are executing ?
Le jeudi 16 janvier 2020, jonperryxlm notifications@github.com a écrit :
I'm having the same issue.
I'm running Amplify CLI 4.12.0 on MacOS 10.15.2
I've set up an example Vue project, added Amplify, added an api and auth
with the default config and when I push my git branch to trigger the
automated deploy I get the following stack:2020-01-16T23:17:22.553Z [INFO]: CREATE_FAILED
UpdateRolesWithIDPFunction AWS::Lambda::Function
Thu Jan 16 2020 23:17:21 GMT+0000 (Coordinated Universal Time)
The runtime parameter of nodejs8.10 is no longer supported for creating or
updating AWS Lambda functions. We recommend you use the new runtime
(nodejs12.x) while creating or updating functions.
(Service: AWSLambdaInternal; Status Code: 400;
Error Code: InvalidParameterValueException;
Request ID: 9aee33c7-ab62-4bed-ab44-2214e937b049)If I remove auth and push the changes to my repo, the automated build is
successful.Also, curiously for me, the build appears to work when I run amplify push.
I have the same UpdateRolesWithIDPFunction config as the OP.
I've spent ages looking into this issue over the past couple of days to no
avail. This article is along the same lines, but explicitly says that if
you're running the latest version of Amplify CLI - which we are - that it
isn't relevant: https://aws-amplify.github.io/
docs/cli/lambda-node-version-updateAny help would be greatly appreciated!
—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHub
https://github.com/aws-amplify/amplify-cli/issues/3187?email_source=notifications&email_token=AN6SWFJNMC3P53RCAQBX5PDQ6DWMLA5CNFSM4KGYEKK2YY3PNVWWK3TUL52HS4DFVREXG43VMVBW63LNMVXHJKTDN5WW2ZLOORPWSZGOEJF6LVY#issuecomment-575399383,
or unsubscribe
https://github.com/notifications/unsubscribe-auth/AN6SWFOMGJRANQMIN3UJSD3Q6DWMLANCNFSM4KGYEKKQ
.
@simon-lanf these are my build settings:
version: 0.1
backend:
phases:
build:
commands:
- amplifyPush --simple
frontend:
phases:
preBuild:
commands:
- npm ci
build:
commands:
- npm run build
artifacts:
baseDirectory: dist
files:
- '**/*'
cache:
paths:
- node_modules/**/*
What are the commands you use with the cli ?
Le jeudi 16 janvier 2020, jonperryxlm notifications@github.com a écrit :
@simon-lanf https://github.com/simon-lanf these are my build settings:
version: 0.1
backend:
phases:
build:
commands:
- amplifyPush --simple
frontend:
phases:
preBuild:
commands:
- npm ci
build:
commands:
- npm run build
artifacts:
baseDirectory: dist
files:
- '/'
cache:
paths:
- node_modules//—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHub
https://github.com/aws-amplify/amplify-cli/issues/3187?email_source=notifications&email_token=AN6SWFIY5THYXNQS74CROODQ6EH5BA5CNFSM4KGYEKK2YY3PNVWWK3TUL52HS4DFVREXG43VMVBW63LNMVXHJKTDN5WW2ZLOORPWSZGOEJGGVSY#issuecomment-575433419,
or unsubscribe
https://github.com/notifications/unsubscribe-auth/AN6SWFLXUVNF6FSFO3BUNO3Q6EH5BANCNFSM4KGYEKKQ
.
With the cli, I'm just doing
amplify add auth
then accepting the defaults and running amplify push
And that works. It just creates the UpdateRolesWithIDPFunction with Node 8.10 runtime
And for completeness, my local node version is 12.13.0
I think I might have resolved my issue. It turns out (for me at least), the automated build process for my branches was using Amplify CLI v1.12.0 (!).
Absolutely no idea why and this doesn't seem to be visible anywhere, but by updating my "Build Image Settings" to include "Amplify CLI: Latest" as an override it seems to work now.
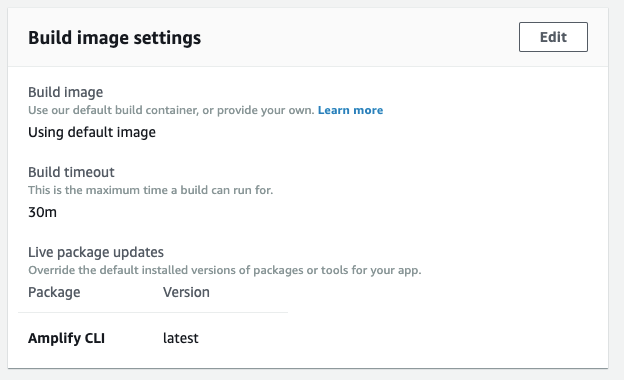
Here are the logs from the first build post change:
2020-01-17T20:08:13.824Z [INFO]: # Ensuring NPM package '@aws-amplify/cli' is version: 'latest'
2020-01-17T20:08:22.635Z [INFO]: # Patching NPM package '@aws-amplify/cli' from 1.12.0 to 4.12.0...
2020-01-17T20:09:16.425Z [INFO]: # Done patching NPM package '@aws-amplify/cli'
I only thought to do this when it started failing on graphql statements that were straight out of the docs and was recommending that I use outdated annotations.
Anyway, hopefully this will solve all my current problems and maybe give some insight to help the OP!
Just want to chime in that I've had this problem as well just now, with the package version override being the only way to fix it.
EDIT: It turns out this also fixed another issue that I was having: My backend wasn't showing up in the online console. Only instructions on how start a new app linked to that backend. I assumed that successfully deploying might end up linking it, but now, after using the cli version override, the environment was added to the console immediately when the deployment started.
Joining in on the report train.
Environment
MacOS 10.14.6
$ npm install -g @aws-amplify/cli
$ amplify --version
Scanning for plugins...
Plugin scan successful
4.13.2
$ node -v
v13.0.1
Reproduction
amplify init
amplify add auth
amplify push
Error
Resource Name: UserPoolClientLambda (AWS::Lambda::Function)
Event Type: create
Reason: The runtime parameter of nodejs8.10 is no longer supported for creating or updating AWS Lambda functions. We recommend you use the new runtime (nodejs12.x) while creating or updating functions. (Service: AWSLambdaInternal; Status Code: 400; Error Code: InvalidParameterValueException; Request ID: f6d965b6-e4a6-4a0e-a380-fc07ac950266)
First Manual Fix
Changed ./amplify/backend/auth/REDACTED/REDACTED-cloudformation-template.yml so that it uses nodejs12.x instead of nodejs8.10. This did however not fix the issue.
CREATE_FAILED UpdateRolesWithIDPFunction AWS::Lambda::Function Mon Feb 10 2020 21:21:52 GMT+0100 (Central European Standard Time) The runtime parameter of nodejs8.10 is no longer supported for creating or updating AWS Lambda functions. We recommend you use the new runtime (nodejs12.x) while creating or updating functions. (Service: AWSLambdaInternal; Status Code: 400; Error Code: InvalidParameterValueException; Request ID: 7cfd2014-17ca-4f05-aade-f9d3fc84095d)
Second Manual Fix
Changed ./amplify/backend/awscloudformation/nested-cloudformation-stack.yml so that it uses nodejs12.x instead of nodejs8.10. This did however not fix the issue.
CREATE_FAILED UpdateRolesWithIDPFunction AWS::Lambda::Function Mon Feb 10 2020 21:27:17 GMT+0100 (Central European Standard Time) The runtime parameter of nodejs8.10 is no longer supported for creating or updating AWS Lambda functions. We recommend you use the new runtime (nodejs12.x) while creating or updating functions. (Service: AWSLambdaInternal; Status Code: 400; Error Code: InvalidParameterValueException; Request ID: c60b892e-aba6-4339-897a-2292a197e405)
Checked for nodejs8.10
Fixed the runtime first, then
$ grep -R '8\.10' amplify
amplify push
$ grep -R '8\.10' amplify
amplify/backend/awscloudformation/nested-cloudformation-stack.yml: "Runtime": "nodejs8.10",
Does that mean that amplify overrides the template and therefore prevents manual fixes?
Is there a new release of the amplify-cli planned to fix this?
+1 this exists also when updating any settings on the cognito userpool resources using the cloudformation templates
I was facing the same issue and @bahrmichael explanation describes it exactly.
I solved it by upgrading amplify-cli from v4.5.0 to v4.13.2
so i was able to get past this by upgrading amplify-cli globally. just wish there was a prompt on the cli that mentioned a newer version being available with an option to update.
Sorry I didn't see you posted a comment @yashutanna . Yes, I second that. Versions are pushed out so quickly with major changes from AWS and no warnings that the cli version is outdated.
amplify-cli v4.13.2 doesn't work for me. It keeps overwriting my nodejs12.x fix. Do you know which version doesn't have this bug?
Just checked that there is no local version of amplify interfering.
$ cat package.json| grep amplify
$ cat package-lock.json| grep amplify
@bahrmichael
It seems to be a corrupt installation, try to remove the globally installed Amplify CLI and reinstall again.
did you use yarn or npm to install the amplify CLI?
If you used yarn, remove all amplify related packages from its global installation directory, their names are all prefixed with "amplify-".
After installation, do a fresh amplify plugin scan before you proceed.
I might have used yarn with amplify some day, but not recently.
I did a global reinstall before, but apparently that didn't delete all files (first install seemed to be 3.2.0). Did a find / -name "amplify" -print to find all the amplify files and removed them. Then reinstalled amplify globally with npm install -g @aws-amplify/cli.
$ amplify plugin scan
Scanning for plugins...
Plugin scan successful
Scanning for plugins...
Plugin scan successful
Then reinitialised the project.
$ amplify init
$ amplify add auth
$ grep -R '8\.10' amplify
Now it doesn't find any nodejs8.10 references anymore :)
The next run of amplify push was successful.
So we can confirm that it was indeed a corrupt installation, which was made worse due to somehow having TWO amplifys installed at the same time which allowed some fallback in the command execution. I _really_ have to reset my laptop soon :D
🎉 Thank you @UnleashedMind 🎉
I had the same problem, this is a possible solution:
- Check your nodejs version
node -v- should be at least verstion 12, if not -> upgrade it - Check your amplify version
amplify -v, at this time, you should have at least 4.13.3, if not ->npm -g update @aws-amplify/cli(or yarn global upgrade alternative) - find every single occurrence of
nodejs8.10and replace it withnodejs12.x
Now you should be able to amplify push
- find every single occurrence of
nodejs8.10and replace it withnodejs12.x
That didn't work for me, as amplify push overwrote it back to nodejs8. Can you verify that this is not the case for others?
@bahrmichael Amplify would write it back to Node 8 only if you have an older version of the CLI. From your last comment it looked like updating the latest version, fixed your issue?
@kaustavghosh06 yes
fyi I just got this in the AWS Amplify build. My local build works fine:
Reason: The runtime parameter of nodejs8.10 is no longer supported for creating or updating AWS Lambda functions. We recommend you use the new runtime (nodejs12.x) while creating or updating functions. (Service: AWSLambdaInternal; Status Code: 400; Error Code: InvalidParameterValueException; Request ID: 34bcac86-97f7-49ed-bfe2-d0003b0c1d89)
@hisham Have you pinned an older version of the CLI on the Amplify Console or are you using the latest?
Previously I had no older version pinned. Now I changed to this, let's see if it works:
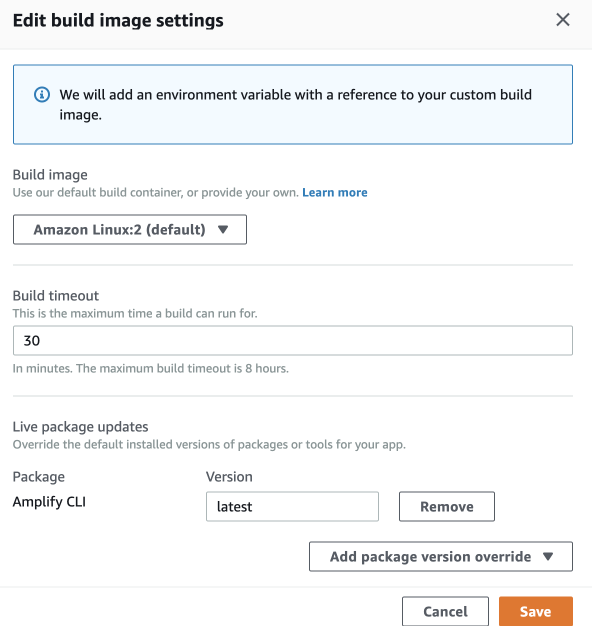
So setting the Amplify CLI Version to 'latest' in build settings fixed things, although before there was no amplify cli override. Strange.
I see this in my AWS Amplify build logs btw - for whatever reason the env is stuck by default at aws amplify cli 1.12.0 and only because of my 'latest' setting does the latest version get used:
2020-06-02T20:45:31.514Z [INFO]: # Ensuring NPM package '@aws-amplify/cli' is version: 'latest'
2020-06-02T20:45:41.322Z [INFO]: # Patching NPM package '@aws-amplify/cli' from 1.12.0 to 4.21.1...
I think I might have resolved my issue. It turns out (for me at least), the automated build process for my branches was using Amplify CLI v1.12.0 (!).
Absolutely no idea why and this doesn't seem to be visible anywhere, but by updating my "Build Image Settings" to include "Amplify CLI: Latest" as an override it seems to work now.
Here are the logs from the first build post change:
2020-01-17T20:08:13.824Z [INFO]: # Ensuring NPM package '@aws-amplify/cli' is version: 'latest' 2020-01-17T20:08:22.635Z [INFO]: # Patching NPM package '@aws-amplify/cli' from 1.12.0 to 4.12.0... 2020-01-17T20:09:16.425Z [INFO]: # Done patching NPM package '@aws-amplify/cli'I only thought to do this when it started failing on graphql statements that were straight out of the docs and was recommending that I use outdated annotations.
Anyway, hopefully this will solve all my current problems and maybe give some insight to help the OP!
Just a note on this "solution"... It is not unheard of cough for new versions of the amplify cli to introduce breaking changes. Having the amplify-cli set to "latest" in your build config means you have to diligently keep your local amplify-cli up-to-date.
I have been stung a couple of times now - see https://github.com/aws-amplify/amplify-cli/issues/3134#issuecomment-641384593
The fastest way (for now) to get a successful build is to override the amplify cli version in the build settings, but your local cli must always be up-to-date.
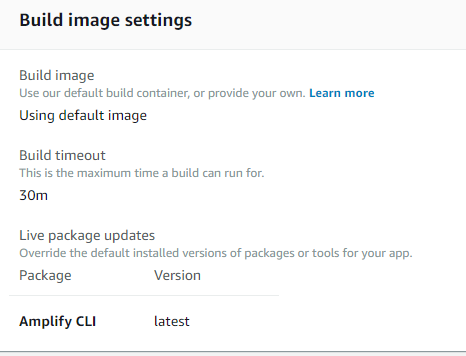
I think I might have resolved my issue. It turns out (for me at least), the automated build process for my branches was using Amplify CLI v1.12.0 (!).
Absolutely no idea why and this doesn't seem to be visible anywhere, but by updating my "Build Image Settings" to include "Amplify CLI: Latest" as an override it seems to work now.
Here are the logs from the first build post change:
2020-01-17T20:08:13.824Z [INFO]: # Ensuring NPM package '@aws-amplify/cli' is version: 'latest' 2020-01-17T20:08:22.635Z [INFO]: # Patching NPM package '@aws-amplify/cli' from 1.12.0 to 4.12.0... 2020-01-17T20:09:16.425Z [INFO]: # Done patching NPM package '@aws-amplify/cli'I only thought to do this when it started failing on graphql statements that were straight out of the docs and was recommending that I use outdated annotations.
Anyway, hopefully this will solve all my current problems and maybe give some insight to help the OP!
Super!! This works for me!!
This is _still_ a problem.
node version: 15.3.0
npm version: 7.0.14
amplify version: 4.37.1
Somehow the build process is injecting node v8.10
If I override the Live package updates version, as above, it works, but I do _not_ want to make that a permanent 'fix', as it is clear that CLI versions break compatibility constantly.
If I change out the Runtime: in XXX-cloudformation-template.yml it overwrites it on build. Resulting in the same The runtime parameter of nodejs8.10 is no longer supported error.
I ran into this problem after merging simple code changes to my production environment (no cloud formation template changes). The Amplify console attempted to deploy the changes, the deployment failed because of this error, and then the rollback failed. The build had deployed just fine to my development stack two days earlier. Now support is telling me that I have to rebuild my entire stack, including Cognito, which means hundreds of our customers will have to reset their passwords. That's unacceptable, so I'm trying to find a solution. I tried testing a new deployment to my dev server using the build image changes mentioned above and that is also now failing. This seems like a significant problem that needs to be addressed quickly. We should have a safe, repeatable way to deploy builds that only changes when we direct it to change.
Most helpful comment
I think I might have resolved my issue. It turns out (for me at least), the automated build process for my branches was using Amplify CLI v1.12.0 (!).
Absolutely no idea why and this doesn't seem to be visible anywhere, but by updating my "Build Image Settings" to include "Amplify CLI: Latest" as an override it seems to work now.

Here are the logs from the first build post change:
2020-01-17T20:08:13.824Z [INFO]: # Ensuring NPM package '@aws-amplify/cli' is version: 'latest' 2020-01-17T20:08:22.635Z [INFO]: # Patching NPM package '@aws-amplify/cli' from 1.12.0 to 4.12.0... 2020-01-17T20:09:16.425Z [INFO]: # Done patching NPM package '@aws-amplify/cli'I only thought to do this when it started failing on graphql statements that were straight out of the docs and was recommending that I use outdated annotations.
Anyway, hopefully this will solve all my current problems and maybe give some insight to help the OP!