Adguardfilters: Turkcell iframe injection
Description:
- Current behaviour:
My beloved ISP (Turkcell Superonline) does not miss any opportunity to violate basic privacy requirements. Periodically (about every week), I get a iframe injection. Actual content of the iframe is probably blocked using this line. I say probably because I could not reproduce it after disabling uBlock Origin then refreshing the page.
Raw HTML part:
<img style="display: none;" src="http://176.235.38.79:8080/ev/49xxxxxxxxxxx23.png?0=51011xxxxxxxxxxxxxxxxxxxxxxdfc42&1=downloaded&2=http%3A%2F%2Fwww.xxxxxxxxxxxx.net%2FMakale%2F34%2Fmilstd1553%2F">
<div id="n_49xxxxxxxxxxx23" style="visibility: visible; position: fixed; z-index: 2147483647; bottom: 0px; right: 0px; opacity: 1; transition: opacity 1000ms ease-in 0s;">
<iframe src="http://guvenliinternet.turkcell.com.tr/ibntest.html" style="background: white none repeat scroll 0% 0%; width: 300px; height: 370px; margin: 20px; padding: 15px; border-radius: 10px; box-shadow: black 3px 3px 20px 2px; frameborder="0"></iframe>
<span style="position: absolute; top: 20px; display: inline-block; text-align: center; font-size: 11px; font-weight: bold; user-select: none; border-radius: 15px; border: 1px solid grey; width: 15px; height: 15px; line-height: 15px; color: grey; cursor: pointer; box-sizing: content-box; font-family: times new roman; right: 20px; background-color: white;>×</span>
</div>
<img style="display: none;" src="http://176.235.38.79:8080/ev/49xxxxxxxxxxx23.png?0=51011xxxxxxxxxxxxxxxxxxxxxxdfc42&1=displayed&2=">
_Sorry for redacting some parts because I believe they may increase the chance to de-anonymize me by my ISP. And I've also blurred website URL because it's just a random occurence, I do not want to cause any irrelevant traffic to the said website._
Screenshot:
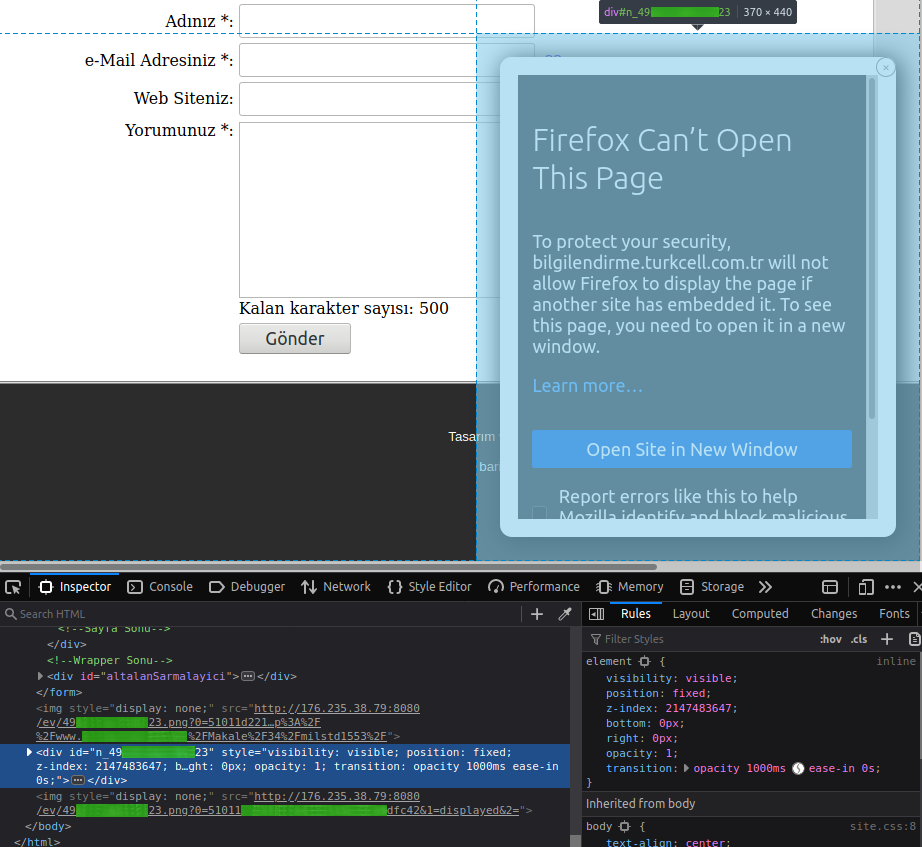
- Expected behaviour:
It would be better to be able to completely block iframes injected by Turkcell.
Steps to reproduce the problem:
It occurs in any HTTP website every few days. It's enough to visit a non-HTTPS site.
System configuration
Filters:
Built-in
- uBlock filters
- uBlock filters – Badware risks
- uBlock filters – Privacy
- uBlock filters – Resource abuse
- uBlock filters – Unbreak
Ads
- AdGuard Base
- AdGuard Mobile Ads
- EasyList
Privacy
- AdGuard Tracking Protection
- EasyPrivacy
- Fanboy’s Enhanced Tracking List
Malware domains
- Online Malicious URL Blocklist
- Spam404
Annoyances
- AdGuard Annoyances
- AdGuard Social Media
- Anti-Facebook
- EasyList Cookie
- Fanboy’s Annoyance
- Fanboy’s Social
- uBlock filters – Annoyances
Multipurpose
- Peter Lowe’s Ad and tracking server list
Regions, languages
- TUR: AdGuard Turkish
Custom
- Malvertising filter list by Disconnect
Information | Value
--- | ---
Operating system: | Ubuntu 18.04.5 LTS
Browser: | Mozilla Firefox v81.0 (64-bit)
AdGuard version: | using uBlock Origin v1.30.2
Filters enabled: | listed above
AdGuard DNS: | None
All 20 comments
If element is embeded before parse page maybe works html filtering*?
tr##^img[src*=".png"][src*="&"]:has(+ div > iframe[src*="turkcell.com.br"])
tr##^div[id][style*="fixed"]:has(> iframe[src*="turkcell.com.br"])
tr##^div[id][style*="fixed"]:has(> iframe[src*="turkcell.com.br"]) + img[src*=".png"][src*="&"]
Hide elements with CSS are no safe to protect privacy but should hide annoyance for many guests.
The iframe also can be loaded with inline-script, these possible test remove with html filtering* if anybody found code on "view-source:".
* - It may not work as if the site has regional encoding for Turkish characters and has not been added by compatibility tests (whether the texts are correctly read by the browser) in uBO.
The problem will probably also be the extent to which a iframe can appear, if it appears outside the '.tr' it can only make it difficult to hide/block how it would not be easy to use scriptlets or network blocking.
For Chromium(/Safari) with uBO (lastest Safari 12-14 need use AdGuard technology for best results) maybe needed is use scriptlet to abort inline-script/script from random file (if after abort to run few part of script disables shown iframe).
If no works sciptlet solution, then maybe possible only hide iframe with lack of privacy.
At best scenario, they changed the name of the script/directories or domain and hence some minor leakage.
If element is embeded before parse page maybe works html filtering*?
I feel like this is the case. I have no idea how a back-end works at ISP scale but I think they'd have to parse the page I requested first and look for a suitable point to place the iframe.
tr##^img[src*=".png"][src*="&"]:has(+ div > iframe[src*="turkcell.com.br"]) tr##^div[id][style*="fixed"]:has(> iframe[src*="turkcell.com.br"]) tr##^div[id][style*="fixed"]:has(> iframe[src*="turkcell.com.br"]) + img[src*=".png"][src*="&"]If i'm not mistaken, I should add these in My filters page of uBO, right?
Hide elements with CSS are no safe to protect privacy but should hide annoyance for many guests.
Definitely. It's a privacy violation but also an annoyance. If it gets harder to completely block it, at least I will try to hide it.
The iframe also can be loaded with
inline-script, these possible test remove with html filtering* if anybody found code on "view-source:".
- It may not work as if the site has regional encoding for Turkish characters and has not been added by compatibility tests (whether the texts are correctly read by the browser) in uBO.
Inline script pushed by ISP? Wow, I did not think about this before you mention it. It sounds even more problematic. I did not look for it but I will scrutiny the page source in the next occurrence.
The problem will probably also be the extent to which a iframe can appear, if it appears outside the '
.tr' it can only make it difficult to hide/block how it would not be easy to use scriptlets or network blocking.For Chromium(/Safari) with uBO (lastest Safari 12-14 need use AdGuard technology for best results) maybe needed is use scriptlet to abort
inline-script/script from random file (if after abort to run few part of script disables shown iframe).If no works sciptlet solution, then maybe possible only hide iframe with lack of privacy.
At best scenario, they changed the name of the script/directories or domain and hence some minor leakage.
I see. I have to look into blocking inline scripts.
Thank you so much for your detailed answer.
@gediz do you see ads on HTTP or also on HTTPS pages?
Please provide full urls without xxx(is 176.235.38.79:8080/ev/ - ads source?)
@gediz do you see ads on HTTP or also on HTTPS pages?
Please provide full urls withoutxxx(is176.235.38.79:8080/ev/- ads source?)
I've never see them appear on an HTTPS page yet, so I can say it's HTTP only for now.
Okay, I will provide full URL when the ad is seen again.
By the way, I think http://176.235.38.79:8080/ev/49xxxxxxxxxxx23.png?0=51011.... URL is source of a tracking pixel. It's used to do not show the same ad repeatedly. Because even though I do not block the ad yet, It does not appear again just after I reload the same page.
Actual ad page seems to be http://guvenliinternet.turkcell.com.tr/ibntest.html. There's another strange thing about this page is when I look at the Network tab of Developer Options while this page is loading, I see my phone number as an argument in a JSON request. I will provide more context when I'm at home.
Ok. Also you can record HAR file and send it to [email protected]
https://kb.adguard.com/en/android/solving-problems/har
I can check all content.
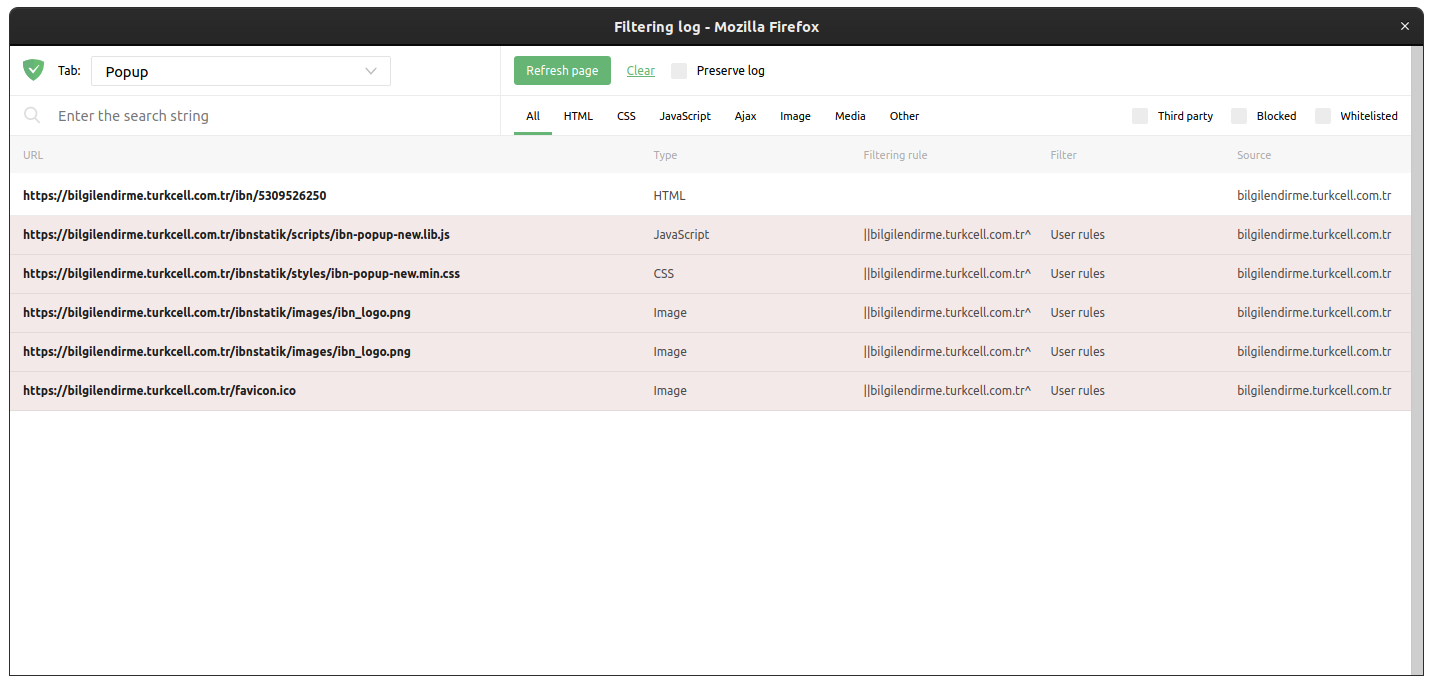
@gediz please add ||bilgilendirme.turkcell.com.tr^ to user rules, clear filtering log and check again.
Some time later please check bilgilendirme.turkcell.com.tr in filtering log(blocked/not blocked)
It's done. I will report when I find a clue. Thanks a lot.
@gediz any news?)
Sorry for long delay but I've waited deliberately to find a logged incident. I did not see any inject iframe since I've added the custom rule you provided, but there's no also log about this yet. What are the chances about it's actively being blocked thanks to custom rule but not being logged?
IMO no possible if you correct cleared cache and now use AdGuard rules logger.
@gediz maybe you need to visit more HTTP, not httpS sites)
@krystian3w
IMO no possible if you correct cleared cache and now use AdGuard rules logger.
I actually did not clear the cache. Just added the custom rule and resetted AdGuard block count. I will clear the cache now.
@Alex-302
@gediz maybe you need to visit more HTTP, not httpS sites)
I especially visit the HTTP sites everyday where I've seen at least one iframe. Maybe it was about cache.
I think I gave you guys enough headache. You can close the issue if you want. I will inspect it with a clean browser with only AdGuard enabled and report my findings. Thank you so much for your precious time.
Ok. I don't add that rule to filter because do not know if it is required.
Hello again.
I'm back with some news. I've seen an iframe on an HTTP page but again, it was just the frame. Content was blocked. AdGuard AdBlocker has successfully blocked 2 elements according to the block count placed on the extension icon. I've checked the logs but it obviously requires a reload as you already know. So I've opened up a new tab and entered to the same URL as previous one but the frame did not appear again and the block count was 1. And there's what I could catch.
Screenshot from log window:
HTML of injected frame:
<img style="display: none;" src="http://176.235.38.79:8080/ev/25021111525433.png?0=51011d221fdacb43c8115b60cb9dfc42&1=downloaded&2=http%3A%2F%2Flinux-sunxi.org%2FSpecial%3ARecentChanges">
<div id="n_25021111525433" style="visibility: visible; position: fixed; z-index: 2147483647; bottom: 0px; right: 0px; opacity: 1; transition: opacity 1000ms ease-in 0s;">
<iframe src="http://guvenliinternet.turkcell.com.tr/ibntest.html" style="background: none repeat scroll 0% 0% white;width: 300px; height: 370px; margin-top: 20px; margin-right: 20px; margin-bottom: 20px; margin-left: 20px; padding-top: 15px; padding-right: 15px; padding-bottom: 15px; padding-left: 15px; border-radius: 10px; box-shadow: black 3px 3px 20px 2px;" frameborder="0"></iframe>
<span style="position: absolute; top: 20px; display: inline-block; text-align: center; font-size: 11px; font-weight: bold; user-select: none; border-radius: 15px; border: 1px solid grey; width: 15px; height: 15px; line-height: 15px; color: grey; cursor: pointer; box-sizing: content-box; font-family: times new roman; right: 20px; background-color: white;">×</span>
</div>
Screenshot of the injected iframe:

URL of the popup: https://bilgilendirme.turkcell.com.tr/ibn/5309526250
Actual content of the frame, when opened in a separate window. Some accumulated notifications:

HTML of the popup content:
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8" />
<meta
name="viewport"
content="width=device-width, initial-scale=1, maximum-scale=1, user-scalable=0"
/>
<title>Popup</title>
<script src="/ibnstatik/scripts/ibn-popup-new.lib.js"></script>
<link rel="stylesheet" href="/ibnstatik/styles/ibn-popup-new.min.css" />
<script>
$(function () {
$(".owl-carousel").owlCarousel({
items: 1,
loop: false,
dots: true,
nav: false,
autoHeight: true,
autoHeightClass: "owl-height",
});
var owl = $(".owl-carousel");
owl.owlCarousel();
$(".owl-next").click(function () {
owl.trigger("next.owl.carousel");
});
$(".owl-prev").click(function () {
owl.trigger("prev.owl.carousel", [300]);
});
});
</script>
</head>
<body>
<div class="uxr-container">
<div class="uxr-line"></div>
<div class="uxr-wrapper">
<div class="uxr-logo">
<img src="/ibnstatik/images/ibn_logo.png" alt="Turkcell" />
</div>
<ul class="owl-carousel owl-theme">
<li class="item">
<div class="uxr-title">Turkcell’den bildiriminiz var</div>
<div class="uxr-desc">
<p>
Superbox Fırsat 10 Mbps sona ermistir. Size uygun diger
tekliflerimiz icin www.turkcell.com.tr yi ziyaret edebilirsiniz.
</p>
</div>
</li>
<li class="item">
<div class="uxr-title">Turkcell’den bildiriminiz var</div>
<div class="uxr-desc">
<p>
Kontratsız Superbox Fırsat 10 Mbps paketiniz 249 TL ye hattiniza
tanimlanmistir ve fatura kesim tarihinde yenilenecektir.
Paketinizi 10.12.2020 00:00 tarihine kadar keyifle kullanmanizi
dileriz. Detayli bilgi icin www.turkcell.com.tr
</p>
</div>
</li>
<li class="item">
<div class="uxr-title">Turkcell’den bildiriminiz var</div>
<div class="uxr-desc">
<p>
Superbox 5 GB Hediye paketiniz ucretsiz hattiniza
tanimlanmistir. Paketinizi 09.12.2020 12:07 tarihine kadar
keyifle kullanmanizi dileriz. Detayli bilgi icin
www.turkcell.com.tr
</p>
</div>
</li>
<li class="item">
<div class="uxr-title">Turkcell’den bildiriminiz var</div>
<div class="uxr-desc">
<p>
Superbox kontratli paketiniz 7 gun sonra sona erecektir.
Kampanya bitiminde paketiniz, kontratsiz ucreti uzerinden
otomatik olarak hattiniza tanimlanacaktir. Kampanyanizi
yenilemek icin 532 nolu Turkcell Musteri Hizmetleri'ni aramanizi
rica ederiz.
</p>
</div>
</li>
<li class="item">
<div class="uxr-title">Turkcell’den bildiriminiz var</div>
<div class="uxr-desc">
<p>
Superbox kontratli paketiniz 15 gun sonra sona erecektir.
Kampanya bitiminde paketiniz, kontratsiz ucreti uzerinden
otomatik olarak hattiniza tanimlanacaktir. Kampanyanizi
yenilemek icin 532 nolu Turkcell Musteri Hizmetleri'ni aramanizi
rica ederiz.
</p>
</div>
</li>
</ul>
<div class="owl-nav">
<div class="owl-prev"></div>
<div class="owl-next"></div>
</div>
</div>
</div>
</body>
</html>
Thanks in advance.
Hi. Could you please try to record new HAR?
Open dev tools with
and visit few non-httpS sites. And export HAR.
After that I will add ||bilgilendirme.turkcell.com.tr^ to filter.
I will try to record new HAR but it's repeat period looks random. I have to summon up a developer tool before entering every single HTTP website. I will do my best.
I will try to record new HAR but it's repeat period looks random. I have to summon up a developer tool before entering every single HTTP website. I will do my best.
You could leave a tab open with http://example.com and devtools open with preserve log checked, and refresh it a couple times a day.
I will try to record new HAR but it's repeat period looks random. I have to summon up a developer tool before entering every single HTTP website. I will do my best.
You could leave a tab open with
http://example.comand devtools open withpreserve logchecked, and refresh it a couple times a day.
Neat idea, thanks. I will try this.
This issue has been automatically marked as stale because it has not had recent activity. It will be closed if no further activity occurs. Thank you for your contributions.